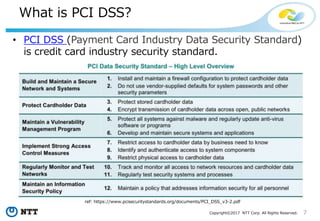
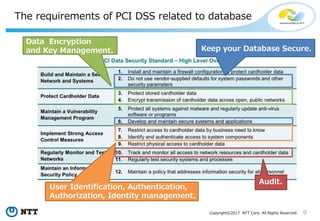
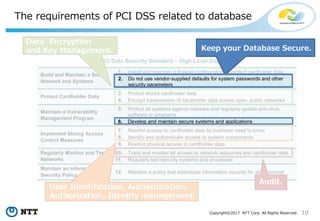
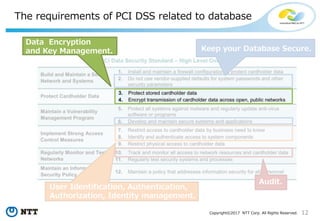
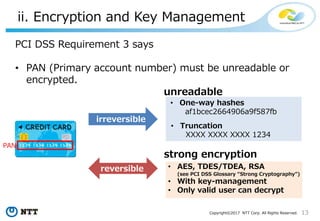
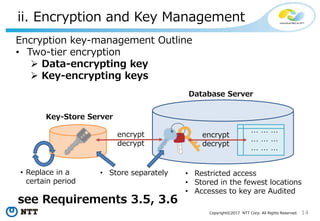
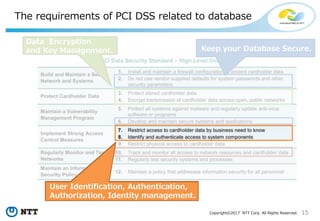
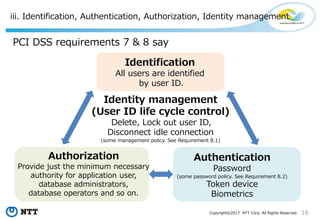
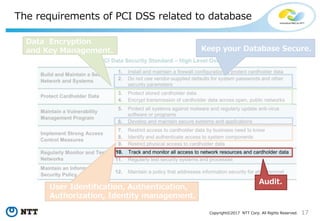
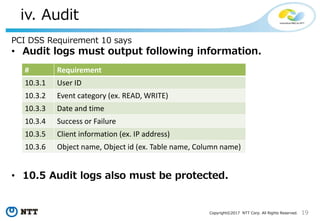
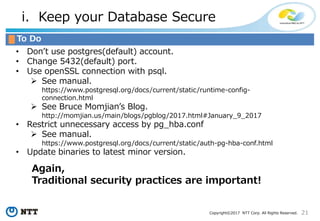
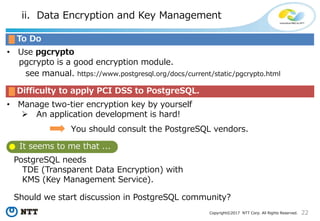
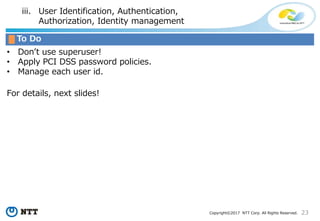
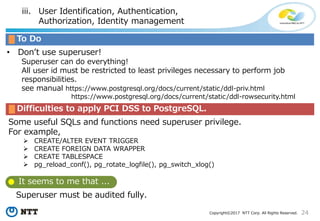
The document discusses the importance of database security within PostgreSQL, particularly in light of PCI DSS requirements for safeguarding credit card transactions in Japan. It outlines security measures like encryption, access control, user authentication, and audit requirements necessary for compliance. The author also indicates challenges in implementing these security standards within PostgreSQL, suggesting the use of tools like pgAudit for improved audit logging.













![40Copyright©2017 NTT Corp. All Rights Reserved.
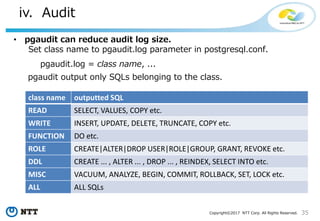
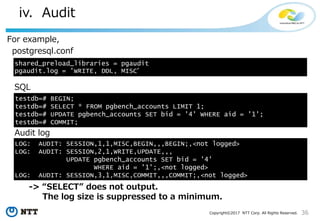
NTT pgaudit
NTT pgaudit configuration file consists of three sections.
[output]
Logger settings you use server log or syslog.
[option]
Some misc. configurations.
[rule]
Filter rules.
For description, please read the README!](https://image.slidesharecdn.com/postgresqlsecurity-170321020308/85/PostgreSQL-Security-How-Do-We-Think-41-320.jpg)
![41Copyright©2017 NTT Corp. All Rights Reserved.
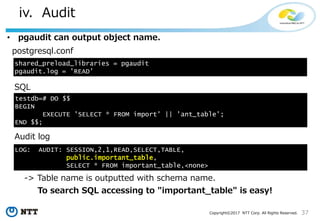
NTT pgaudit
• Restarting PostgreSQL is needed to change audit
settings.
$ vi $PGDATA/postgresql.conf
shared_preload_libraries = 'pgaudit'
pgaudit.config_file = '/path/to/pgaudit.conf'
NTT pgaudit has only two parameters in postgresql.conf
Other pgaduit parameters are in pgaudit.conf.
# login by auditor
$ vim /audit_conf/pgaudit.conf
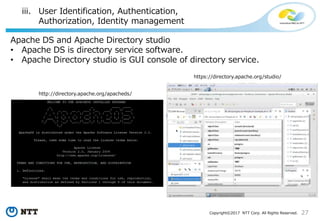
# some settings...
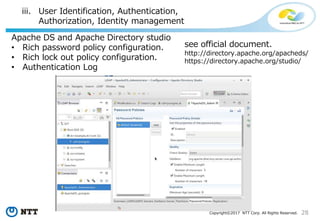
[output]
logger= 'serverlog‘
...
$ chmod +r /path/to/pgaudit.conf
$ ll /path/to/pgaudit.conf
-rw-rw-r--. 1 auditer auditer 384 11月 25 23:33 /path/to/pgaudit.conf
Only the auditor had better be able to edit pgaudit.conf
-> Superuser can not edit pgaudit.conf!](https://image.slidesharecdn.com/postgresqlsecurity-170321020308/85/PostgreSQL-Security-How-Do-We-Think-42-320.jpg)
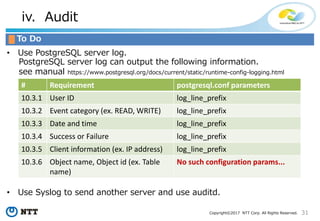
![42Copyright©2017 NTT Corp. All Rights Reserved.
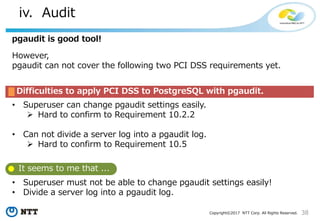
NTT pgaudit
• Divide a server log into an audit log.
NTT pgaudit can export to serverlog or syslog.
Parameters in [output] section
Parameter Description Remarks
logger Logger you use; serverlog or syslog -
pathlog Specifies the socket to which syslog listens Parameter for syslog
facility See man 3 syslog for value Parameter for syslog
priority See man 3 syslog for value Parameter for syslog
ident See man 3 syslog for value Parameter for syslog
option See man 3 syslog for value Parameter for syslog
server log
information for
operating
information for
auditing
auditer
operator
NTT pgaudit log](https://image.slidesharecdn.com/postgresqlsecurity-170321020308/85/PostgreSQL-Security-How-Do-We-Think-43-320.jpg)
![43Copyright©2017 NTT Corp. All Rights Reserved.
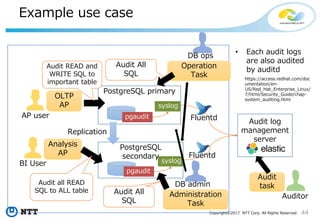
NTT pgaudit
• Rich Log filter.
NTT pgaudit has these filters. Parameters in [rule] section.
NTT pgaudit can have several [rule] sections.
Field name Description Sample setting
timestamp Timestamp range
timestamp = '09:00:00 - 10:00:00,
18:00:00 - 18:30:00
database Database name datebase = 'prodcut_db'
audit_role Role name audit_role ='superuser1'
class
Type of operation. Possible values are,
BACKUP, CONNECT, DDL, ERROR, FUNCTION, MISC, READ,
ROLE, WRITE, SYSTEM
class = 'READ, WRITE'
command_tag command_tag = 'CREATE, SELECT'
object_type
Type of object. Possible values are,
TABLE, INDEX, SEQUENCE, TOAST_VALUE, VIEW,
MATERIALIZED_VIEW, COMPOSITE_TYPE, FOREIGN_TABLE,
FUNCTION
object_type = 'TABLE, INDEX'
object_name Qualified object name
object_name =
'myschema.hoge_table'
application_name Connecting application name application_name = 'myapp'
remote_host Host name remote_host = 'ap_server'](https://image.slidesharecdn.com/postgresqlsecurity-170321020308/85/PostgreSQL-Security-How-Do-We-Think-44-320.jpg)


![51Copyright©2017 NTT Corp. All Rights Reserved.
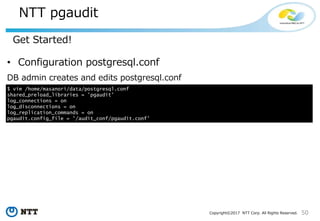
NTT pgaudit
Get Started!
• Configuration pgaudit.conf
$ vim /audit_conf/pgaudit.conf
# Where to log (e.g. log to serverlog).
[output]
logger= 'serverlog'
# Behavior of the PGAUDIT (e.g. setting log_catalog)
[option]
log_catalog = true
# Selection conditions of the Session-Audit-Logging.
[rule]
format = 'CONNECTION: %d,%u,"%connection_message"'
class = 'CONNECT'
[rule]
format = 'DML: %d,%u,%class,%command_tag,"%object_name","%command_text"'
class = 'READ,WRITE‘
$ chmod +r /audit_conf/pgaudit.conf
$ ll /audit_conf/pgaudit.conf
-rw-rw-r--. 1 auditer auditer 384 11月 25 23:33 /audit_conf/pgaudit.conf
Auditor creates and edits pgaudit.conf
-> DB admin can not edit pgaudit.conf!](https://image.slidesharecdn.com/postgresqlsecurity-170321020308/85/PostgreSQL-Security-How-Do-We-Think-52-320.jpg)
![52Copyright©2017 NTT Corp. All Rights Reserved.
NTT pgaudit
Get Started!
• Start PostgreSQL
$ /usr/local/pgsql_latest/bin/pg_ctl start -D /home/masanori/data
waiting for server to start....2016-11-25 23:36:53.469 JST [21880] LOG: log_catalog = 1
2016-11-25 23:36:53.469 JST [21880] LOG: log_level_string = (null)
2016-11-25 23:36:53.469 JST [21880] LOG: log_level = 15
2016-11-25 23:36:53.469 JST [21880] LOG: log_parameter = 0
2016-11-25 23:36:53.469 JST [21880] LOG: log_statement_once = 0
2016-11-25 23:36:53.469 JST [21880] LOG: log_for_test = 0
2016-11-25 23:36:53.469 JST [21880] LOG: role =
... skip ...
2016-11-25 23:36:53.469 JST [21880] LOG: Rule 0
2016-11-25 23:36:53.469 JST [21880] LOG: BMP class = 2
2016-11-25 23:36:53.469 JST [21880] LOG: Rule 1
2016-11-25 23:36:53.469 JST [21880] LOG: BMP class = 320
2016-11-25 23:36:53.469 JST [21880] LOG: pgaudit extension initialized
2016-11-25 23:36:53.489 JST [21881] LOG: database system was shut down at 2016-11-25 23:11:15 JST
2016-11-25 23:36:53.489 JST [21881] LOG: MultiXact member wraparound protections are now enabled
2016-11-25 23:36:53.492 JST [21880] LOG: database system is ready to accept connections
2016-11-25 23:36:53.493 JST [21887] LOG: logical replication launcher started
2016-11-25 23:36:53.493 JST [21885] LOG: autovacuum launcher started
After starting PostgreSQL, the audit setting is logged.](https://image.slidesharecdn.com/postgresqlsecurity-170321020308/85/PostgreSQL-Security-How-Do-We-Think-53-320.jpg)
![53Copyright©2017 NTT Corp. All Rights Reserved.
NTT pgaudit
Get Started!
• Access to PostgreSQL
$ /usr/local/pgsql_latest/bin/psql -p 5555 -d postgres
2016-11-25 23:40:24.276 JST [21909] LOG: AUDIT: SESSION,,,CONNECT,2016-11-25 23:40:24
JST,,,[local],[unknown],,0,00000,connection received: host=[local],,,,,
2016-11-25 23:40:24.276 JST [21909] LOG: connection received: host=[local]
2016-11-25 23:40:24.277 JST [21909] LOG: AUDIT: SESSION,,,CONNECT,2016-11-25 23:40:24
JST,postgres,Masanori,[local],[unknown],3/10,0,00000,connection authorized: user=Masanori database=postgres,,,,,
2016-11-25 23:40:24.277 JST [21909] LOG: connection authorized: user=Masanori database=postgres
connection logs is exported.](https://image.slidesharecdn.com/postgresqlsecurity-170321020308/85/PostgreSQL-Security-How-Do-We-Think-54-320.jpg)