Quantifying Information Leaks using Reliability Analysis
•
0 likes•183 views
Report
Share
Report
Share
Download to read offline
Recommended
Quantifying Information Leaks using Reliability Analysis

Presentation at the International SPIN Symposium on Model Checking of Software 2014. Full paper is here:
http://dl.acm.org/citation.cfm?id=2632367
Quantifying Information Leaks via Model Counting Modulo Theories

The 41st CREST Open Workshop - Software Engineering And Computer Science Using Information
http://crest.cs.ucl.ac.uk/cow/the_41st_cow_27_and_28_april_2015/
Recommended
Quantifying Information Leaks using Reliability Analysis

Presentation at the International SPIN Symposium on Model Checking of Software 2014. Full paper is here:
http://dl.acm.org/citation.cfm?id=2632367
Quantifying Information Leaks via Model Counting Modulo Theories

The 41st CREST Open Workshop - Software Engineering And Computer Science Using Information
http://crest.cs.ucl.ac.uk/cow/the_41st_cow_27_and_28_april_2015/
MapReduce for Parallel Trace Validation of LTL Properties

We present an algorithm for the automated verification of Linear Temporal Logic formulae on event traces using an increasingly popular cloud computing framework called MapReduce. The algorithm can process multiple, arbitrary fragments of the trace in parallel, and compute its final result through a cycle of runs of MapReduce instances. Compared to classical, single-instance solutions, a proof-of-concept implementation shows through experimental evaluation how the algorithm reduces by as much as 90% the number of operations that must be performed linearly, resulting in a commensurate speed gain.
An introduction to lattice-based cryptography

Due to the imminent threat of quantum computers, which may break all currently deployed cryptographic schemes in the near future, research in the field of cryptography has increasingly shifted to "post-quantum" cryptographic primitives, which attempt to offer security even in the age of large-scale quantum computers. Lattice-based solutions are leading candidates among post-quantum cryptosystems, due to their efficiency, versatility, and simplicity. These slides explain the basic ideas behind lattice-based cryptography, using visuals whenever possible for ease of understanding.
Runtime Monitoring of Stream Logic Formulae (Talk @ FPS 2015)

We introduce a formal notation for the processing of event traces called Stream Logic (SL). A monitor evaluates a Boolean condition over an input trace, while a filter outputs events from an input trace depending on some monitor's verdict; both constructs can be freely composed. We show how all operators of Linear Temporal Logic, as well as the parametric slicing of an input trace, can be written as Stream Logic constructs.
matlab code of shifting and folding of two sequences

matlab code of shifting and folding of two sequences
I am trying to figure out why my code won't work. It keeps telling me that my...

I am trying to figure out why my code won't work. It keeps telling me that my vectors are not the same length but they are! My code is right there:
Thanks!
% 2.23 Problem
%Brackets for output, () for the inputs
function[V]=cylinder(r,L)
h=1:.1:L;
%The function file has outputs and inputs, the inputs are the values you
%want inputted in and the outputs are what you get out of it.
for P=1:length(h);
h=1:.1:L;
V(P)=(r.^2*acos((r-h(P))/(r))-(r-h(P))
Tech Talks @NSU: DLang: возможности языка и его применение

http://techtalks.nsu.ru
Видеозапись: http://www.youtube.com/watch?v=sfBrMhAxvFk
5 ноября 2013. DLang: возможности языка и его применение(Николай Толстокулаков, Ixtens)
"Николай Толстокулаков (Ixtens) рассказывает об истории, синтаксисе и фичах языка D."
Лекция прочитана в рамках проекта Tech Talks @NSU – серии открытых лекций о разработке ПО и карьере в IT, проводимых в Новосибирском государственном университете.
Подробности: http://techtalks.nsu.ru
Sigma Protocols and Zero Knowledge

Slides from talk on "Sigma Protocols and Zero Knowledge" at Saint-Petersburg Cryptography Developers Meetup
Model-counting Approaches For Nonlinear Numerical Constraints

Presentation at NASA Formal Methods Symposium 2017
All-Solution Satisfiability Modulo Theories: applications, algorithms and ben...

Presentation at the 10th International Conference on Availability, Reliability and Security (ARES 2015)
More Related Content
What's hot
MapReduce for Parallel Trace Validation of LTL Properties

We present an algorithm for the automated verification of Linear Temporal Logic formulae on event traces using an increasingly popular cloud computing framework called MapReduce. The algorithm can process multiple, arbitrary fragments of the trace in parallel, and compute its final result through a cycle of runs of MapReduce instances. Compared to classical, single-instance solutions, a proof-of-concept implementation shows through experimental evaluation how the algorithm reduces by as much as 90% the number of operations that must be performed linearly, resulting in a commensurate speed gain.
An introduction to lattice-based cryptography

Due to the imminent threat of quantum computers, which may break all currently deployed cryptographic schemes in the near future, research in the field of cryptography has increasingly shifted to "post-quantum" cryptographic primitives, which attempt to offer security even in the age of large-scale quantum computers. Lattice-based solutions are leading candidates among post-quantum cryptosystems, due to their efficiency, versatility, and simplicity. These slides explain the basic ideas behind lattice-based cryptography, using visuals whenever possible for ease of understanding.
Runtime Monitoring of Stream Logic Formulae (Talk @ FPS 2015)

We introduce a formal notation for the processing of event traces called Stream Logic (SL). A monitor evaluates a Boolean condition over an input trace, while a filter outputs events from an input trace depending on some monitor's verdict; both constructs can be freely composed. We show how all operators of Linear Temporal Logic, as well as the parametric slicing of an input trace, can be written as Stream Logic constructs.
matlab code of shifting and folding of two sequences

matlab code of shifting and folding of two sequences
I am trying to figure out why my code won't work. It keeps telling me that my...

I am trying to figure out why my code won't work. It keeps telling me that my vectors are not the same length but they are! My code is right there:
Thanks!
% 2.23 Problem
%Brackets for output, () for the inputs
function[V]=cylinder(r,L)
h=1:.1:L;
%The function file has outputs and inputs, the inputs are the values you
%want inputted in and the outputs are what you get out of it.
for P=1:length(h);
h=1:.1:L;
V(P)=(r.^2*acos((r-h(P))/(r))-(r-h(P))
Tech Talks @NSU: DLang: возможности языка и его применение

http://techtalks.nsu.ru
Видеозапись: http://www.youtube.com/watch?v=sfBrMhAxvFk
5 ноября 2013. DLang: возможности языка и его применение(Николай Толстокулаков, Ixtens)
"Николай Толстокулаков (Ixtens) рассказывает об истории, синтаксисе и фичах языка D."
Лекция прочитана в рамках проекта Tech Talks @NSU – серии открытых лекций о разработке ПО и карьере в IT, проводимых в Новосибирском государственном университете.
Подробности: http://techtalks.nsu.ru
Sigma Protocols and Zero Knowledge

Slides from talk on "Sigma Protocols and Zero Knowledge" at Saint-Petersburg Cryptography Developers Meetup
What's hot (20)
MapReduce for Parallel Trace Validation of LTL Properties

MapReduce for Parallel Trace Validation of LTL Properties
Runtime Monitoring of Stream Logic Formulae (Talk @ FPS 2015)

Runtime Monitoring of Stream Logic Formulae (Talk @ FPS 2015)
matlab code of shifting and folding of two sequences

matlab code of shifting and folding of two sequences
I am trying to figure out why my code won't work. It keeps telling me that my...

I am trying to figure out why my code won't work. It keeps telling me that my...
Tech Talks @NSU: DLang: возможности языка и его применение

Tech Talks @NSU: DLang: возможности языка и его применение
More from Quoc-Sang Phan
Model-counting Approaches For Nonlinear Numerical Constraints

Presentation at NASA Formal Methods Symposium 2017
All-Solution Satisfiability Modulo Theories: applications, algorithms and ben...

Presentation at the 10th International Conference on Availability, Reliability and Security (ARES 2015)
Towards an SMT-based approach for Quantitative Information Flow

Presentation at the Dagstuhl Seminar on Quantitative Security Analysis. Full paper is here:
http://dl.acm.org/citation.cfm?id=2590328
Self-composition by Symbolic Execution

Presentation at the ICCSW 2013 workshop. Full paper is here:
http://drops.dagstuhl.de/opus/volltexte/2013/4277/
Symbolic Quantitative Information Flow

Presentation at the Java PathFinder workshop 2012. Full paper is here:
http://dl.acm.org/citation.cfm?id=2382791
More from Quoc-Sang Phan (7)
Model-counting Approaches For Nonlinear Numerical Constraints

Model-counting Approaches For Nonlinear Numerical Constraints
All-Solution Satisfiability Modulo Theories: applications, algorithms and ben...

All-Solution Satisfiability Modulo Theories: applications, algorithms and ben...
Towards an SMT-based approach for Quantitative Information Flow

Towards an SMT-based approach for Quantitative Information Flow
Recently uploaded
Astronomy Update- Curiosity’s exploration of Mars _ Local Briefs _ leadertele...

Article written for leader telegram
Comparative structure of adrenal gland in vertebrates

Adrenal gland comparative structures in vertebrates
Multi-source connectivity as the driver of solar wind variability in the heli...

The ambient solar wind that flls the heliosphere originates from multiple
sources in the solar corona and is highly structured. It is often described
as high-speed, relatively homogeneous, plasma streams from coronal
holes and slow-speed, highly variable, streams whose source regions are
under debate. A key goal of ESA/NASA’s Solar Orbiter mission is to identify
solar wind sources and understand what drives the complexity seen in the
heliosphere. By combining magnetic feld modelling and spectroscopic
techniques with high-resolution observations and measurements, we show
that the solar wind variability detected in situ by Solar Orbiter in March
2022 is driven by spatio-temporal changes in the magnetic connectivity to
multiple sources in the solar atmosphere. The magnetic feld footpoints
connected to the spacecraft moved from the boundaries of a coronal hole
to one active region (12961) and then across to another region (12957). This
is refected in the in situ measurements, which show the transition from fast
to highly Alfvénic then to slow solar wind that is disrupted by the arrival of
a coronal mass ejection. Our results describe solar wind variability at 0.5 au
but are applicable to near-Earth observatories.
Comparing Evolved Extractive Text Summary Scores of Bidirectional Encoder Rep...

Comparing Evolved Extractive Text Summary Scores of Bidirectional Encoder Rep...University of Maribor
Slides from:
11th International Conference on Electrical, Electronics and Computer Engineering (IcETRAN), Niš, 3-6 June 2024
Track: Artificial Intelligence
https://www.etran.rs/2024/en/home-english/Deep Behavioral Phenotyping in Systems Neuroscience for Functional Atlasing a...

Functional Magnetic Resonance Imaging (fMRI) provides means to characterize brain activations in response to behavior. However, cognitive neuroscience has been limited to group-level effects referring to the performance of specific tasks. To obtain the functional profile of elementary cognitive mechanisms, the combination of brain responses to many tasks is required. Yet, to date, both structural atlases and parcellation-based activations do not fully account for cognitive function and still present several limitations. Further, they do not adapt overall to individual characteristics. In this talk, I will give an account of deep-behavioral phenotyping strategies, namely data-driven methods in large task-fMRI datasets, to optimize functional brain-data collection and improve inference of effects-of-interest related to mental processes. Key to this approach is the employment of fast multi-functional paradigms rich on features that can be well parametrized and, consequently, facilitate the creation of psycho-physiological constructs to be modelled with imaging data. Particular emphasis will be given to music stimuli when studying high-order cognitive mechanisms, due to their ecological nature and quality to enable complex behavior compounded by discrete entities. I will also discuss how deep-behavioral phenotyping and individualized models applied to neuroimaging data can better account for the subject-specific organization of domain-general cognitive systems in the human brain. Finally, the accumulation of functional brain signatures brings the possibility to clarify relationships among tasks and create a univocal link between brain systems and mental functions through: (1) the development of ontologies proposing an organization of cognitive processes; and (2) brain-network taxonomies describing functional specialization. To this end, tools to improve commensurability in cognitive science are necessary, such as public repositories, ontology-based platforms and automated meta-analysis tools. I will thus discuss some brain-atlasing resources currently under development, and their applicability in cognitive as well as clinical neuroscience.
Nutraceutical market, scope and growth: Herbal drug technology

As consumer awareness of health and wellness rises, the nutraceutical market—which includes goods like functional meals, drinks, and dietary supplements that provide health advantages beyond basic nutrition—is growing significantly. As healthcare expenses rise, the population ages, and people want natural and preventative health solutions more and more, this industry is increasing quickly. Further driving market expansion are product formulation innovations and the use of cutting-edge technology for customized nutrition. With its worldwide reach, the nutraceutical industry is expected to keep growing and provide significant chances for research and investment in a number of categories, including vitamins, minerals, probiotics, and herbal supplements.
Cancer cell metabolism: special Reference to Lactate Pathway

Normal Cell Metabolism:
Cellular respiration describes the series of steps that cells use to break down sugar and other chemicals to get the energy we need to function.
Energy is stored in the bonds of glucose and when glucose is broken down, much of that energy is released.
Cell utilize energy in the form of ATP.
The first step of respiration is called glycolysis. In a series of steps, glycolysis breaks glucose into two smaller molecules - a chemical called pyruvate. A small amount of ATP is formed during this process.
Most healthy cells continue the breakdown in a second process, called the Kreb's cycle. The Kreb's cycle allows cells to “burn” the pyruvates made in glycolysis to get more ATP.
The last step in the breakdown of glucose is called oxidative phosphorylation (Ox-Phos).
It takes place in specialized cell structures called mitochondria. This process produces a large amount of ATP. Importantly, cells need oxygen to complete oxidative phosphorylation.
If a cell completes only glycolysis, only 2 molecules of ATP are made per glucose. However, if the cell completes the entire respiration process (glycolysis - Kreb's - oxidative phosphorylation), about 36 molecules of ATP are created, giving it much more energy to use.
IN CANCER CELL:
Unlike healthy cells that "burn" the entire molecule of sugar to capture a large amount of energy as ATP, cancer cells are wasteful.
Cancer cells only partially break down sugar molecules. They overuse the first step of respiration, glycolysis. They frequently do not complete the second step, oxidative phosphorylation.
This results in only 2 molecules of ATP per each glucose molecule instead of the 36 or so ATPs healthy cells gain. As a result, cancer cells need to use a lot more sugar molecules to get enough energy to survive.
Unlike healthy cells that "burn" the entire molecule of sugar to capture a large amount of energy as ATP, cancer cells are wasteful.
Cancer cells only partially break down sugar molecules. They overuse the first step of respiration, glycolysis. They frequently do not complete the second step, oxidative phosphorylation.
This results in only 2 molecules of ATP per each glucose molecule instead of the 36 or so ATPs healthy cells gain. As a result, cancer cells need to use a lot more sugar molecules to get enough energy to survive.
introduction to WARBERG PHENOMENA:
WARBURG EFFECT Usually, cancer cells are highly glycolytic (glucose addiction) and take up more glucose than do normal cells from outside.
Otto Heinrich Warburg (; 8 October 1883 – 1 August 1970) In 1931 was awarded the Nobel Prize in Physiology for his "discovery of the nature and mode of action of the respiratory enzyme.
WARNBURG EFFECT : cancer cells under aerobic (well-oxygenated) conditions to metabolize glucose to lactate (aerobic glycolysis) is known as the Warburg effect. Warburg made the observation that tumor slices consume glucose and secrete lactate at a higher rate than normal tissues.
extra-chromosomal-inheritance[1].pptx.pdfpdf![extra-chromosomal-inheritance[1].pptx.pdfpdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![extra-chromosomal-inheritance[1].pptx.pdfpdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Slide 1: Title Slide
Extrachromosomal Inheritance
Slide 2: Introduction to Extrachromosomal Inheritance
Definition: Extrachromosomal inheritance refers to the transmission of genetic material that is not found within the nucleus.
Key Components: Involves genes located in mitochondria, chloroplasts, and plasmids.
Slide 3: Mitochondrial Inheritance
Mitochondria: Organelles responsible for energy production.
Mitochondrial DNA (mtDNA): Circular DNA molecule found in mitochondria.
Inheritance Pattern: Maternally inherited, meaning it is passed from mothers to all their offspring.
Diseases: Examples include Leber’s hereditary optic neuropathy (LHON) and mitochondrial myopathy.
Slide 4: Chloroplast Inheritance
Chloroplasts: Organelles responsible for photosynthesis in plants.
Chloroplast DNA (cpDNA): Circular DNA molecule found in chloroplasts.
Inheritance Pattern: Often maternally inherited in most plants, but can vary in some species.
Examples: Variegation in plants, where leaf color patterns are determined by chloroplast DNA.
Slide 5: Plasmid Inheritance
Plasmids: Small, circular DNA molecules found in bacteria and some eukaryotes.
Features: Can carry antibiotic resistance genes and can be transferred between cells through processes like conjugation.
Significance: Important in biotechnology for gene cloning and genetic engineering.
Slide 6: Mechanisms of Extrachromosomal Inheritance
Non-Mendelian Patterns: Do not follow Mendel’s laws of inheritance.
Cytoplasmic Segregation: During cell division, organelles like mitochondria and chloroplasts are randomly distributed to daughter cells.
Heteroplasmy: Presence of more than one type of organellar genome within a cell, leading to variation in expression.
Slide 7: Examples of Extrachromosomal Inheritance
Four O’clock Plant (Mirabilis jalapa): Shows variegated leaves due to different cpDNA in leaf cells.
Petite Mutants in Yeast: Result from mutations in mitochondrial DNA affecting respiration.
Slide 8: Importance of Extrachromosomal Inheritance
Evolution: Provides insight into the evolution of eukaryotic cells.
Medicine: Understanding mitochondrial inheritance helps in diagnosing and treating mitochondrial diseases.
Agriculture: Chloroplast inheritance can be used in plant breeding and genetic modification.
Slide 9: Recent Research and Advances
Gene Editing: Techniques like CRISPR-Cas9 are being used to edit mitochondrial and chloroplast DNA.
Therapies: Development of mitochondrial replacement therapy (MRT) for preventing mitochondrial diseases.
Slide 10: Conclusion
Summary: Extrachromosomal inheritance involves the transmission of genetic material outside the nucleus and plays a crucial role in genetics, medicine, and biotechnology.
Future Directions: Continued research and technological advancements hold promise for new treatments and applications.
Slide 11: Questions and Discussion
Invite Audience: Open the floor for any questions or further discussion on the topic.
Nucleic Acid-its structural and functional complexity.

This presentation explores a brief idea about the structural and functional attributes of nucleotides, the structure and function of genetic materials along with the impact of UV rays and pH upon them.
Richard's aventures in two entangled wonderlands

Since the loophole-free Bell experiments of 2020 and the Nobel prizes in physics of 2022, critics of Bell's work have retreated to the fortress of super-determinism. Now, super-determinism is a derogatory word - it just means "determinism". Palmer, Hance and Hossenfelder argue that quantum mechanics and determinism are not incompatible, using a sophisticated mathematical construction based on a subtle thinning of allowed states and measurements in quantum mechanics, such that what is left appears to make Bell's argument fail, without altering the empirical predictions of quantum mechanics. I think however that it is a smoke screen, and the slogan "lost in math" comes to my mind. I will discuss some other recent disproofs of Bell's theorem using the language of causality based on causal graphs. Causal thinking is also central to law and justice. I will mention surprising connections to my work on serial killer nurse cases, in particular the Dutch case of Lucia de Berk and the current UK case of Lucy Letby.
insect taxonomy importance systematics and classification

documents provide information about insect classification and taxonomy of insect
Recently uploaded (20)
Astronomy Update- Curiosity’s exploration of Mars _ Local Briefs _ leadertele...

Astronomy Update- Curiosity’s exploration of Mars _ Local Briefs _ leadertele...
platelets- lifespan -Clot retraction-disorders.pptx

platelets- lifespan -Clot retraction-disorders.pptx
Lateral Ventricles.pdf very easy good diagrams comprehensive

Lateral Ventricles.pdf very easy good diagrams comprehensive
Comparative structure of adrenal gland in vertebrates

Comparative structure of adrenal gland in vertebrates
Multi-source connectivity as the driver of solar wind variability in the heli...

Multi-source connectivity as the driver of solar wind variability in the heli...
Comparing Evolved Extractive Text Summary Scores of Bidirectional Encoder Rep...

Comparing Evolved Extractive Text Summary Scores of Bidirectional Encoder Rep...
Deep Behavioral Phenotyping in Systems Neuroscience for Functional Atlasing a...

Deep Behavioral Phenotyping in Systems Neuroscience for Functional Atlasing a...
ESR_factors_affect-clinic significance-Pathysiology.pptx

ESR_factors_affect-clinic significance-Pathysiology.pptx
Mammalian Pineal Body Structure and Also Functions

Mammalian Pineal Body Structure and Also Functions
Nutraceutical market, scope and growth: Herbal drug technology

Nutraceutical market, scope and growth: Herbal drug technology
Cancer cell metabolism: special Reference to Lactate Pathway

Cancer cell metabolism: special Reference to Lactate Pathway
In silico drugs analogue design: novobiocin analogues.pptx

In silico drugs analogue design: novobiocin analogues.pptx
Circulatory system_ Laplace law. Ohms law.reynaults law,baro-chemo-receptors-...

Circulatory system_ Laplace law. Ohms law.reynaults law,baro-chemo-receptors-...
Nucleic Acid-its structural and functional complexity.

Nucleic Acid-its structural and functional complexity.
insect taxonomy importance systematics and classification

insect taxonomy importance systematics and classification
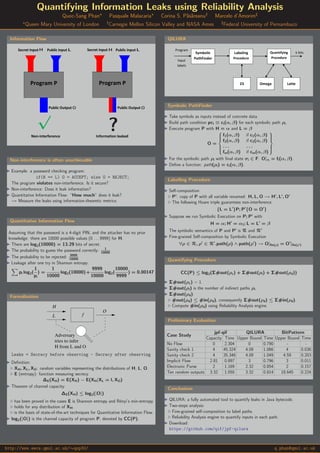
Quantifying Information Leaks using Reliability Analysis
- 1. Quantifying Information Leaks using Reliability Analysis Quoc-Sang Phan∗ Pasquale Malacaria∗ Corina S. P˘as˘areanu† Marcelo d’Amorim‡ ∗ Queen Mary University of London † Carnegie Mellon Silicon Valley and NASA Ames ‡ Federal University of Pernambuco Information Flow Secret Input Public input Program P Public Output Non-interference Public input Program P Secret Input Information leaked Public Output √ ? H HL L O O Non-interference is often unachievable Example: a password checking program: if(H == L) O = ACCEPT; else O = REJECT; The program violates non-interference. Is it secure? Non-interference: Does it leak information? Quantitative Information Flow: “How much” does it leak? → Measure the leaks using information-theoretic metrics. Quantitative Information Flow Assuming that the password is a 4-digit PIN, and the attacker has no prior knowledge: there are 10000 possible values (0 . . . 9999) for H. There are log2(10000) = 13.29 bits of secret. The probability to guess the password correctly: 1 10000 The probability to be rejected: 9999 10000 Leakage after one try in Shannon entropy: pi log2( 1 pi ) = 1 10000 log2(10000)+ 9999 10000 log2( 10000 9999 ) = 0.00147 Formalisation Adversary tries to infer H from L and O H L O f Leaks = Secrecy before observing - Secrecy after observing Definition: XH, XL, XO: random variables representing the distributions of H, L, O. E (entropy): function measuring secrecy. ∆E(XH) = E(XH) − E(XH|XL = l, XO) Theorem of channel capacity: ∆E(XH) ≤ log2(|O|) has been proved in the cases E is Shannon entropy and R´enyi’s min-entropy. holds for any distribution of XH. is the basis of state-of-the-art techniques for Quantitative Information Flow. log2(|O|) is the channel capacity of program P, denoted by CC(P). QILURA Program Symbolic PathFinder Labeling Procedure Z3 Omega Quantifying Procedure Latte Input labels k bits Symbolic PathFinder Take symbols as inputs instead of concrete data. Build path condition pci ≡ ci(α, β) for each symbolic path ρi. Execute program P with H = α and L = β O = f1(α, β) if c1(α, β) f2(α, β) if c2(α, β) . . . . . . fm(α, β) if cm(α, β) For the symbolic path ρi with final state σi ∈ F: O|σi = fi(α, β). Define a function: path(ρi) = ci(α, β). Labelling Procedure Self-composition P : copy of P with all variable renamed: H, L, O → H , L , O The following Hoare triple guarantees non-interference {L = L }P; P {O = O } Suppose we run Symbolic Execution on P; P with H = α; H = α1; L = L = β The symbolic semantics of P and P is R and R Fine-grained Self-composition by Symbolic Execution ∀ρ ∈ R, ρ ∈ R .path(ρ) ∧ path(ρ ) → O|fin(ρ) = O |fin(ρ ) Quantifying Procedure CC(P) ≤ log2(Σ#out(ρc) + Σ#out(ρi) + Σ#out(ρd)) Σ#out(ρc) = 1. Σ#out(ρi) is the number of indirect paths ρi. Σ#out(ρd): #out(ρd) ≤ #in(ρd), consequently Σ#out(ρd) ≤ Σ#in(ρd). Compute #in(ρd) using Reliability Analysis engine. Preliminary Evaluation Case Study jpf-qif QILURA BitPattern Capacity Time Upper Bound Time Upper Bound Time No Flow 0 2.304 0 0.790 - - Sanity check 1 4 45.324 4.09 1.066 4 0.036 Sanity check 2 4 35.346 4.09 1.049 4.59 0.203 Implicit Flow 2.81 0.897 3 0.796 3 0.011 Electronic Purse 2 1.169 2.32 0.854 2 0.157 Ten random outputs 3.32 1.050 3.32 0.814 18.645 0.224 Conclusions QILURA: a fully automated tool to quantify leaks in Java bytecode. Two-steps analysis: Fine-grained self-composition to label paths. Reliability Analysis engine to quantify inputs in each path. Download: https://github.com/qif/jpf-qilura http://www.eecs.qmul.ac.uk/∼qsp30/ q.phan@qmul.ac.uk
