The document appears to be a portfolio for various computer information systems courses completed by Scott Manuel, including introductory and intermediate business computing, networking, web development, digital forensics, and server administration courses. It includes course descriptions, objectives, and exhibits demonstrating skills and assignments for each course. The portfolio documents the educational experience and qualifications gained in these courses for the area of network technology, digital forensics, and advanced data recovery.











![9
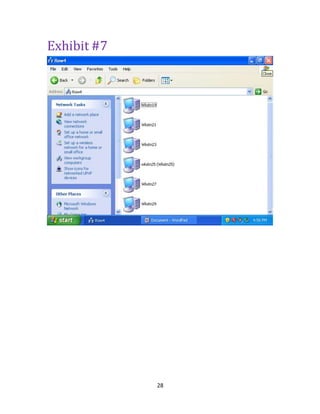
Exhibit #2
User FREDERIC SCOTT
Course _A+ HARDWARE SUPPORT II _2421B233
Test Final Exam R1
Started 3/15/13 12:51 PM
Submitted 3/15/13 2:04 PM
Status Needs Grading
Score Grade not available.
Time
Elapsed
1 hour, 13 minutes.
Instructions This test covers the study guide for the final exam
good luck to all, thanks for being a great class ......Steve
Question 1
Needs Grading
1. Your sister brings you her computer, she states it worked yesterday but after she worked on
it the CPU fan spins but nothing else. Please tell me the procedure to find out what is wrong
Answer
Selected Answer: Ask what the problem is.
Ask what it started to do before they felt it started acting up
Ask what they completely did in their attempt to correct the
problem
Ask what they want to have done to it to correct the problem and
give a solution
Correct Answer:
I am looking for a understanding of this important skill
Response
Feedback:
[None Given]
Question 2
Needs Grading
List two reasons why a person would want to have a dual boot system and
two draw backs to having a dual boot system
Answer
Selected Answer: 1.) Want to learn a new OS 2.)Want more Access
1.) Increasing a complexity of things 2.)Not efficient
Correct Answer:](https://image.slidesharecdn.com/8b7d68e5-80bb-43bf-be81-ee64c2cd42ce-151203180747-lva1-app6891/85/portfolio-12-320.jpg)
![10
the need to support 2 OS
to learn a new OS
Response Feedback: [None Given]
Question 3
Needs Grading
You are building a computer from scratch. You have a motherboard, memory, hard drive,
CD-Rom and a new case. Please tell me the procedure to build this system.
Answer
Selected
Answer:
Install the motherboard in the proper place in the new case making
sure it is connected with the fan for the CPU to the power source...
install the memory into the proper slot on the motherboard... Install
the hard drive into a lower section of the new case and then connect it
to the motherboard in the proper slot that is specified for it...install the
CD Rom into slot of the case and then connect it to the hard drive as
well the slot specified on the motherboard... Connect the case power
source to power and to a monitor... Turn on see what is there...
Correct
Answer: I am looking for a understanding of this procedure
Response
Feedback:
[None Given]
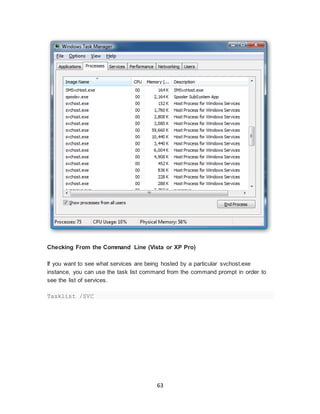
Question 4
Needs Grading
Please List four things you would look for when doing a site survey
Answer
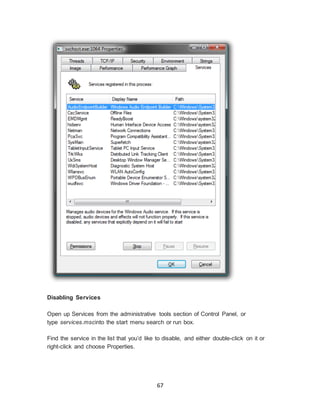
Selected Answer: 1.) Talk with the person and see what are their needs
2.) See what they need to do and where it is going
3.) What Required
4.) Power, Servers, Amplifiers, Chairs, Desk space
Correct Answer: [None]
Response Feedback: [None Given]](https://image.slidesharecdn.com/8b7d68e5-80bb-43bf-be81-ee64c2cd42ce-151203180747-lva1-app6891/85/portfolio-13-320.jpg)
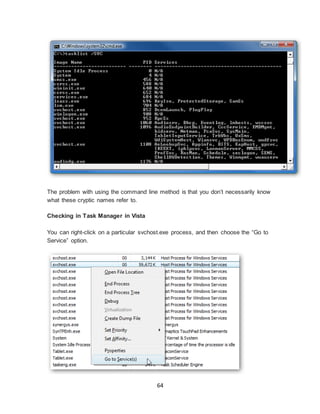
![11
Question 5
Needs Grading
Please list three typical needs of the small business
Answer
Selected Answer: 1.) Network Connection - Internet
2.) Reliable Operating System
3.) Printing
Correct Answer: [None]
Response Feedback: [None Given]
Question 6
Needs Grading
Please list 4 things to make your Laptop last a long time
Answer
Selected Answer: 1.) Keep Power Supply narrow edge down
2.) Do not leave it on all the time
3.) Needs to be on a stand
4.) Needs to be on a hard surface
Correct Answer: [None]
Response Feedback: [None Given]
Question 7
4 out of 4 points
When designing a backup plan for a small business, the main things you
should consider are
Answer
Selected
Answer:
d.
A. What are you going to back up to? What gets backed up?
How often? By who?
Correct
Answer:
d.
A. What are you going to back up to? What gets backed up?
How often? By who?
Question 8](https://image.slidesharecdn.com/8b7d68e5-80bb-43bf-be81-ee64c2cd42ce-151203180747-lva1-app6891/85/portfolio-14-320.jpg)


































![54
Exhibit #14
Created By Access Data® FTK® Imager 3.1.0.1514
Case Information:
Acquired using: ADI3.1.0.1514
Case Number: CIS273FINAL
Evidence Number:
Unique Description:
Examiner:
Notes:
--------------------------------------------------------------
Information for D:UsersDigitalForensicsDesktopCIS273FINAL.ad1:
[Custom Content Sources]
Dickinson.E01: Partition 1 [2996MB]: NONAME [NTFS]|[root]|System
Volume Information|*(Wildcard, Consider Case, Include Subdirectories)
Dickinson.E01: Partition 1 [2996MB]: NONAME
[NTFS]|[root]|WINDOWS|Prefetch|*(Wildcard, Consider Case, Include
Subdirectories)
Dickinson.E01: Partition 1 [2996MB]: NONAME
[NTFS]|[root]|WINDOWS|system32|config|*(Wildcard, Consider Case,
Include Subdirectories)
Dickinson.E01: Partition 1 [2996MB]: NONAME [NTFS]|[root]|Documents
and Settings|*(Wildcard, Consider Case, Include Subdirectories)](https://image.slidesharecdn.com/8b7d68e5-80bb-43bf-be81-ee64c2cd42ce-151203180747-lva1-app6891/85/portfolio-57-320.jpg)
![55
Dickinson.E01: Partition 1 [2996MB]: NONAME
[NTFS]|[root]|RECYCLER|*(Wildcard, Consider Case, Include
Subdirectories)
[Computed Hashes]
MD5 checksum: 6014256d0ebb225a655d021ef1218b82
SHA1 checksum: 129c27f8a4e47e96d042d4a63b1d1c9fcbc02ada
Image information:
Acquisition started: Sat May 30 11:32:46 2015
Acquisition finished: Sat May 30 11:33:12 2015
Segment list:
D:UsersDigitalForensicsDesktopCIS273FINAL.ad1](https://image.slidesharecdn.com/8b7d68e5-80bb-43bf-be81-ee64c2cd42ce-151203180747-lva1-app6891/85/portfolio-58-320.jpg)