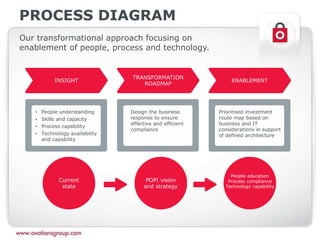
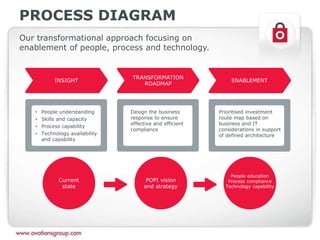
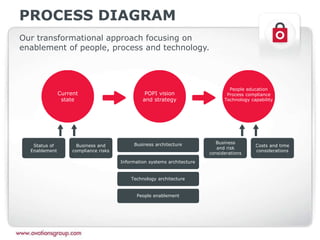
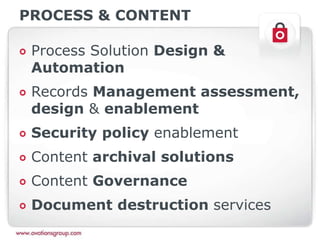
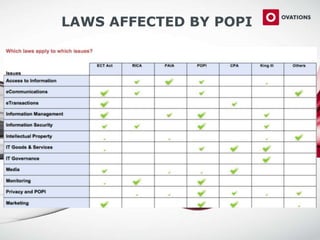
This document discusses the Protection of Personal Information (POPI) Act in South Africa and how it will impact companies. It provides an overview of POPI, explaining that it establishes conditions for lawful processing of personal information, including collection, processing limitations, data security, and rights of the data subject. The document also outlines an approach for companies to become compliant with POPI through transforming people, processes, and technology using insight, roadmapping, and enablement. Offerings are provided around strategy, training, change management, data management, and processes.