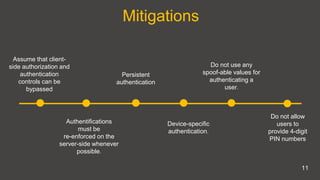
Poor authorization and authentication on mobile applications can allow unauthorized access. It occurs when things like long session timeouts, weak passwords, or hidden logout buttons are present. This exposes applications to technical impacts like being unable to identify users and business impacts like reputational damage from fraud or theft. Developers can detect these issues by testing account lockout policies, password strength, and attempting to bypass authentication. Prevention includes assuming client-side controls may be bypassed, enforcing authentication on the server-side, using persistent and device-specific authentication, and not allowing short or spoofable authentication values.