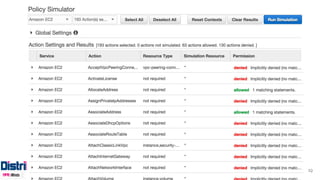
The document discusses policy-based access control (PBAC), emphasizing its declarative specification of access rules and modularization for better governance. It illustrates different approaches to implementing access control, from straightforward code rules to more advanced PBAC systems that allow central definition and updates of rules at runtime. The document identifies research challenges and concludes that while PBAC presents new opportunities for access management, there are still technological hurdles to overcome.






![Basic approach: rules in code
[....]
if (! (“manager” in user.roles
and doc.owner == user
and 8h00 < now() < 17h00 )) {
[...]
}
+ straightforward
+ you can encode almost
anything
- access rules are code
- no separation of concerns
- no modularity leads to audit challenge
- what if rules change?
▪ update application code
▪ updates all over the place
8](https://image.slidesharecdn.com/policy-basedaccesscontrol-160622102013/85/Policy-based-access-control-8-320.jpg)
![More advanced approach: modularization
@authz(user, “read”, result)
public Document getDoc(docId) { [...] }
+ central definition of rules
+ easier to audit
- access rules are code
- IT is still in charge
- no separation of concerns
- what if rules change?
▪ update application code
▪ updates all over the place
9
public boolean authz(
subject, action, resource) {
if (! (“manager” in user.roles and …)) { [...] }](https://image.slidesharecdn.com/policy-basedaccesscontrol-160622102013/85/Policy-based-access-control-9-320.jpg)
![Most advanced approach: policy-based
@authz(user, “read”, result)
public Document getDoc(docId) { [...] }
Policy
Decision
Point
Policy
+ central authorization logic
+ central definition of rules
+ easy to audit
+ access rules independent artifacts
+ clear separation of concerns
+ rule updates at run-time
10](https://image.slidesharecdn.com/policy-basedaccesscontrol-160622102013/85/Policy-based-access-control-10-320.jpg)