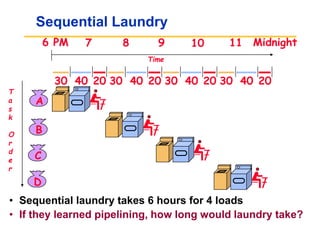
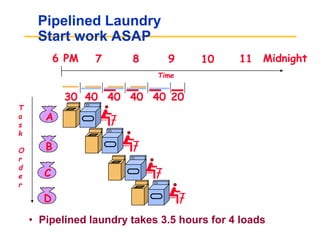
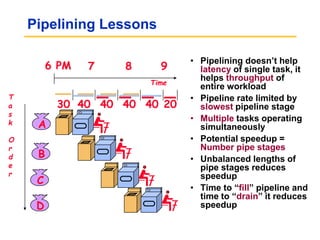
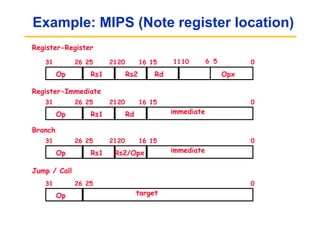
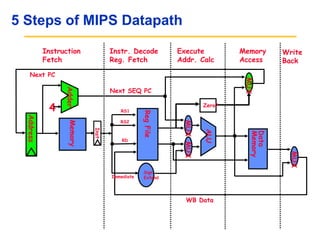
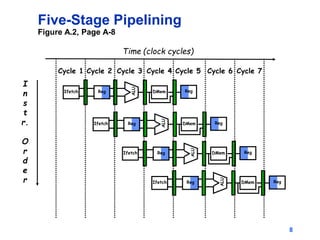
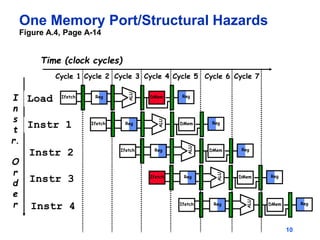
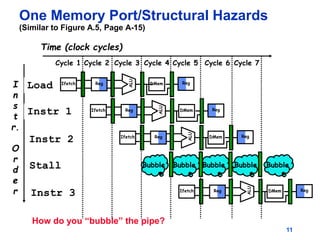
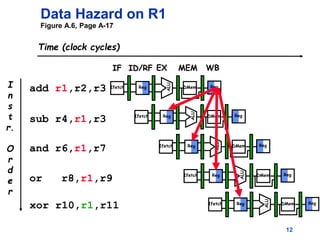
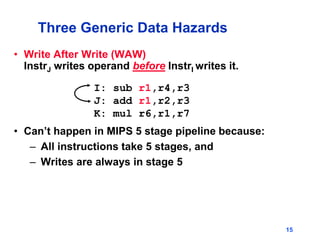
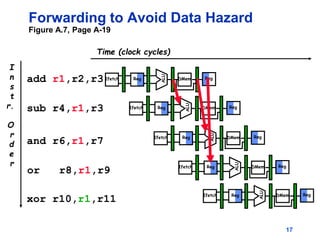
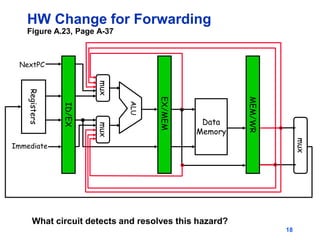
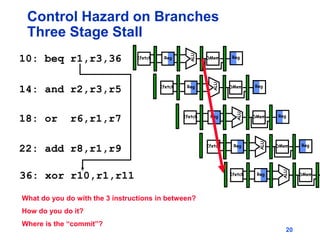
Pipelining allows tasks like laundry to be completed faster by overlapping the stages of multiple tasks. A sequential laundry process for 4 loads takes 6 hours, while a pipelined approach can finish in 3.5 hours by starting new loads as soon as previous loads enter new stages. Pipelining improves throughput but not latency of individual tasks. Hazards like structural issues from limited hardware resources, and data and control dependencies between instructions must be addressed through techniques like forwarding, stalling, and branch prediction to maintain pipeline efficiency.