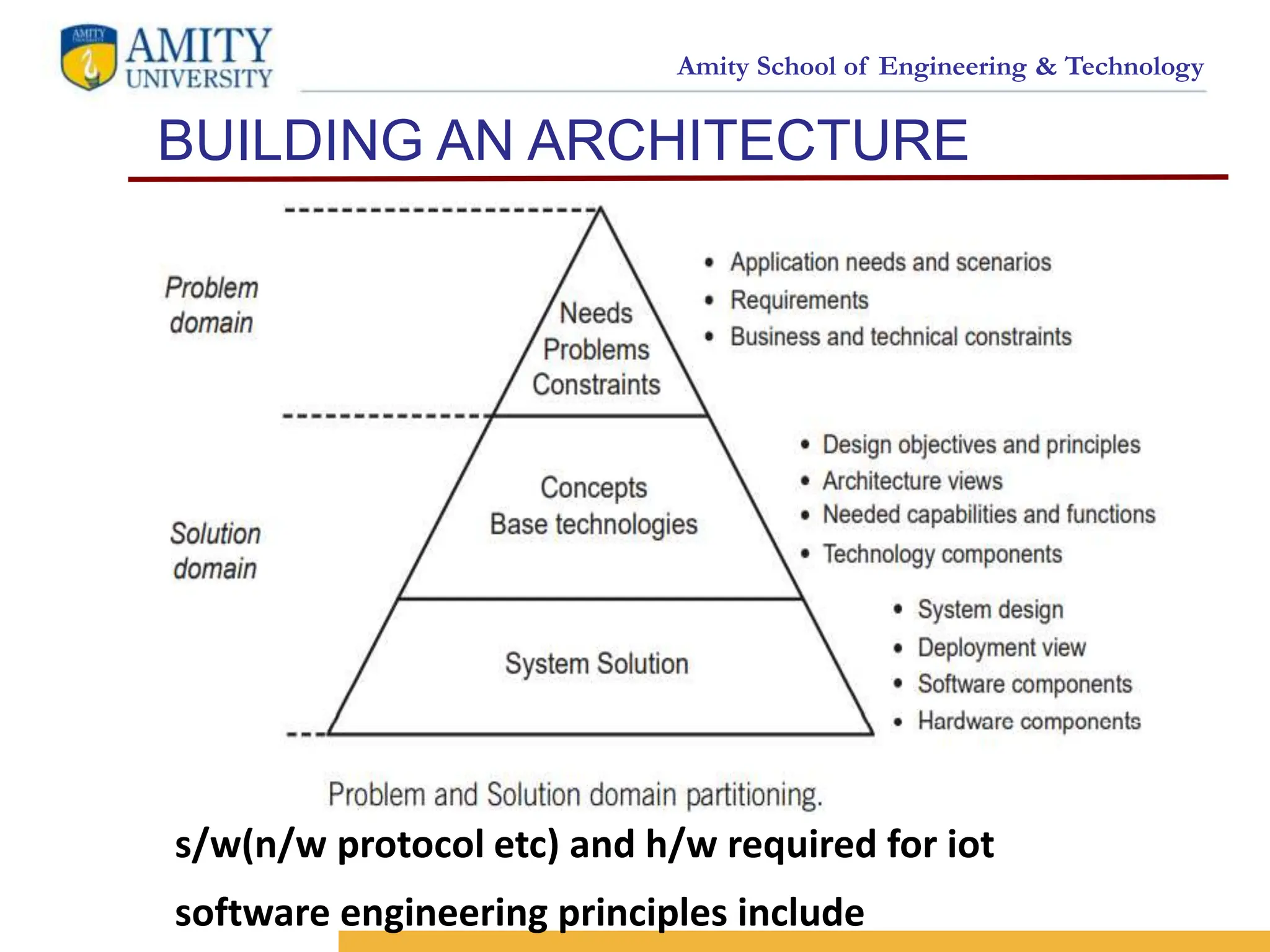
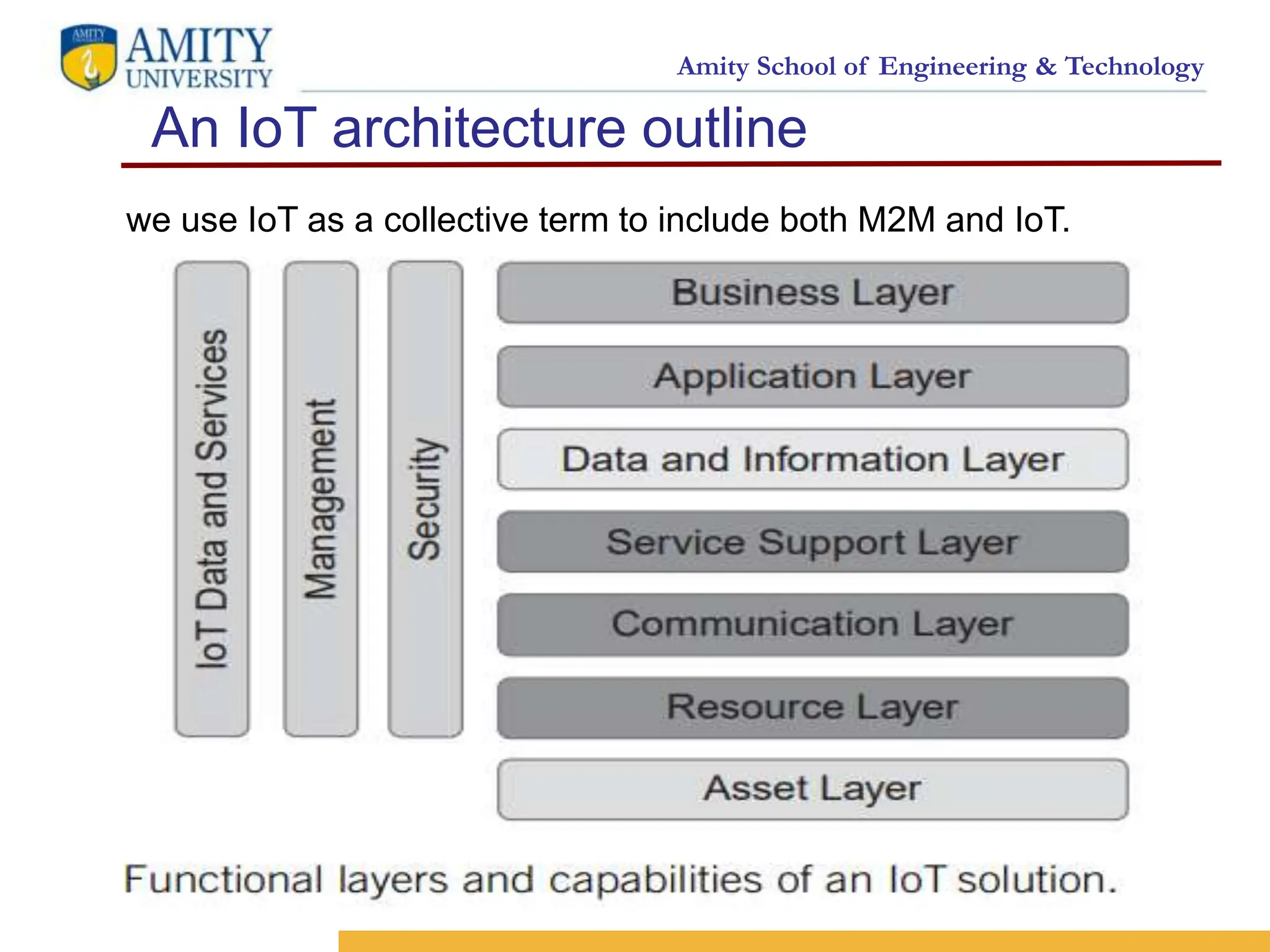
The document outlines an architecture for the Internet of Things (IoT). It discusses building an architecture by establishing objectives and design principles. Some key design principles are reusability, open service-oriented capabilities, security, trust, scalability and evolvability. The document then presents an IoT architecture outline consisting of layers including an asset layer, resource layer, communication layer, service support layer, data and information layer, application layer and business layer. It also discusses functional groups that cross the layers for management, security and data/services processing.