Embed presentation
Download to read offline

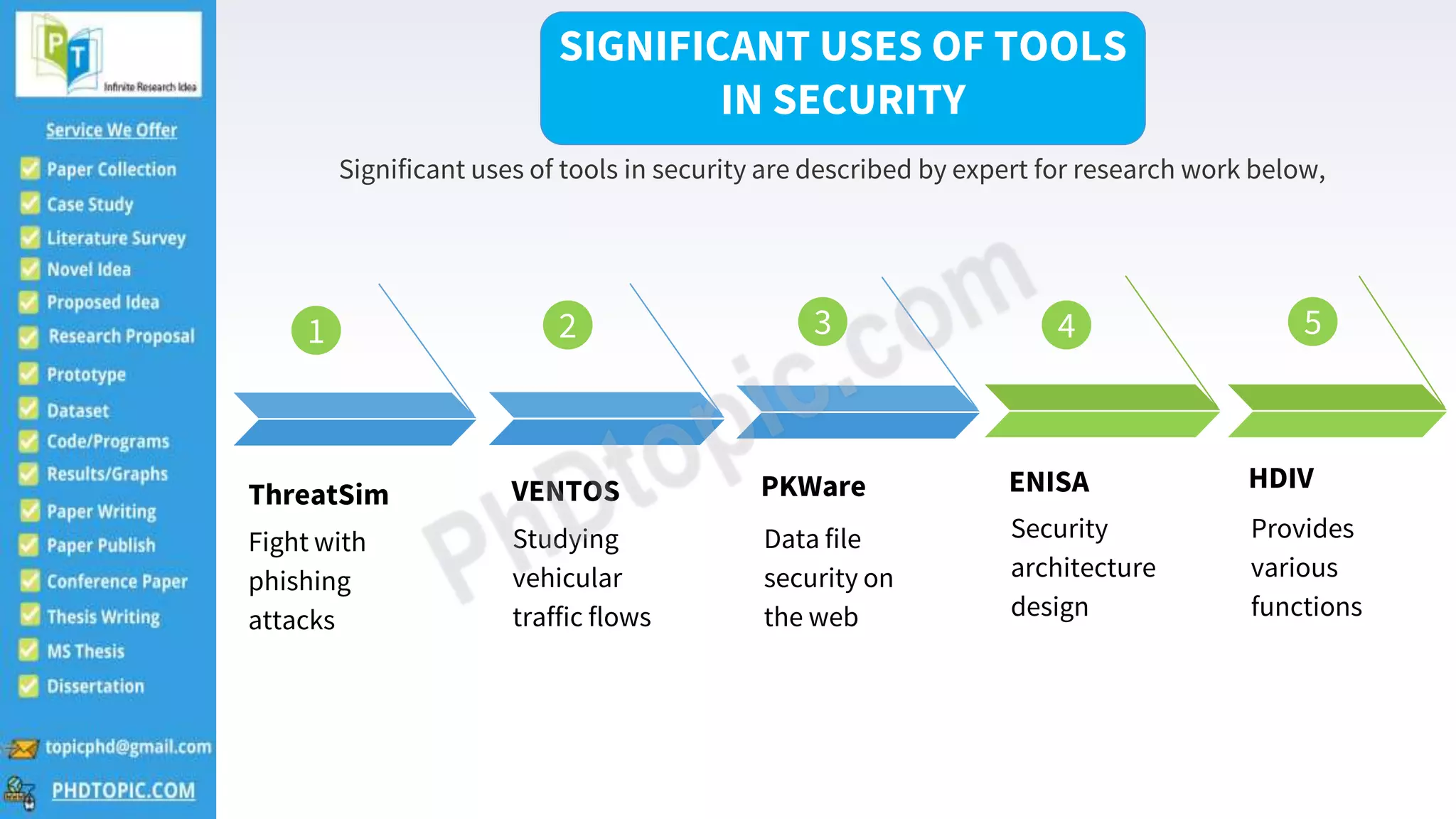
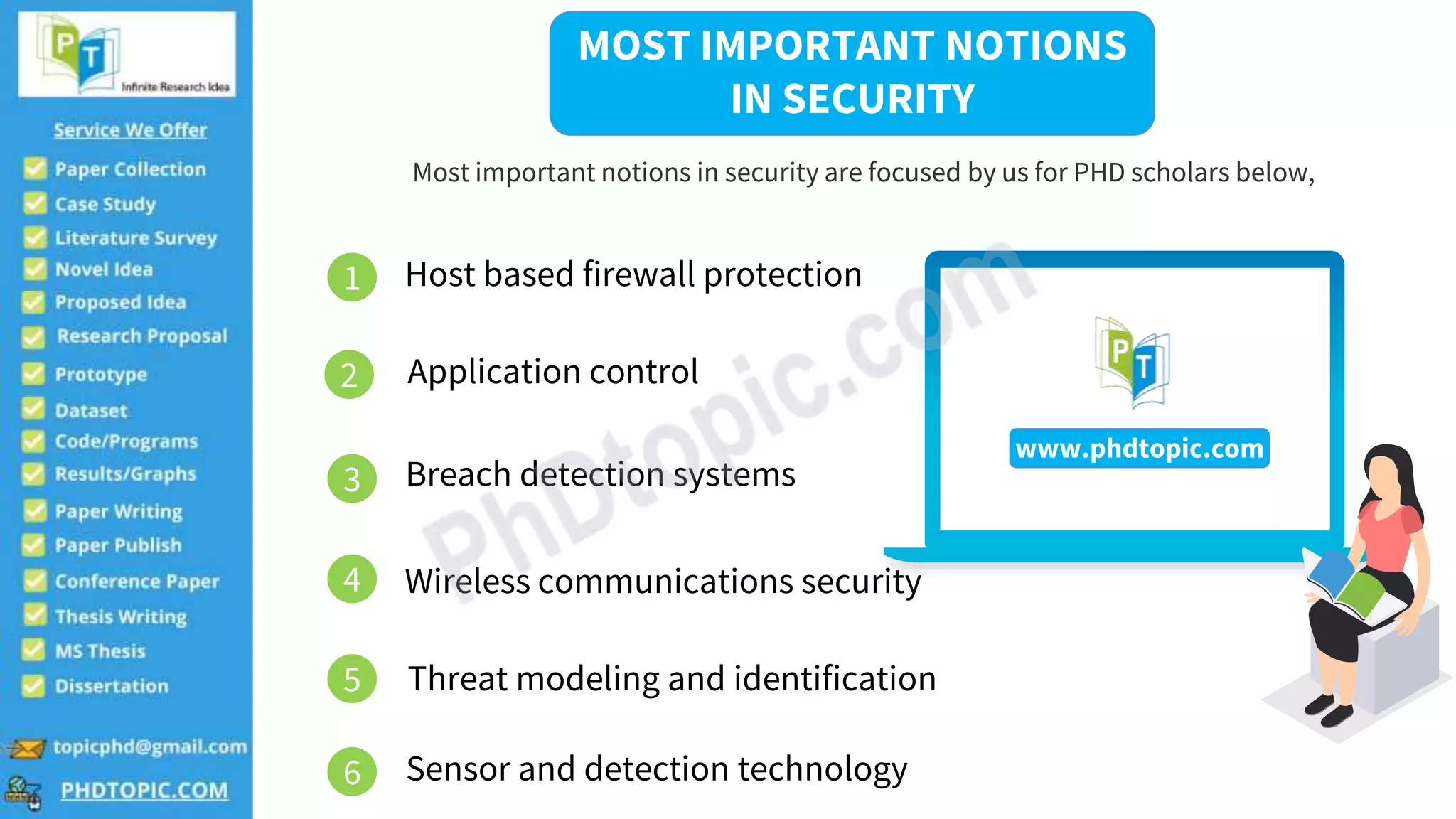
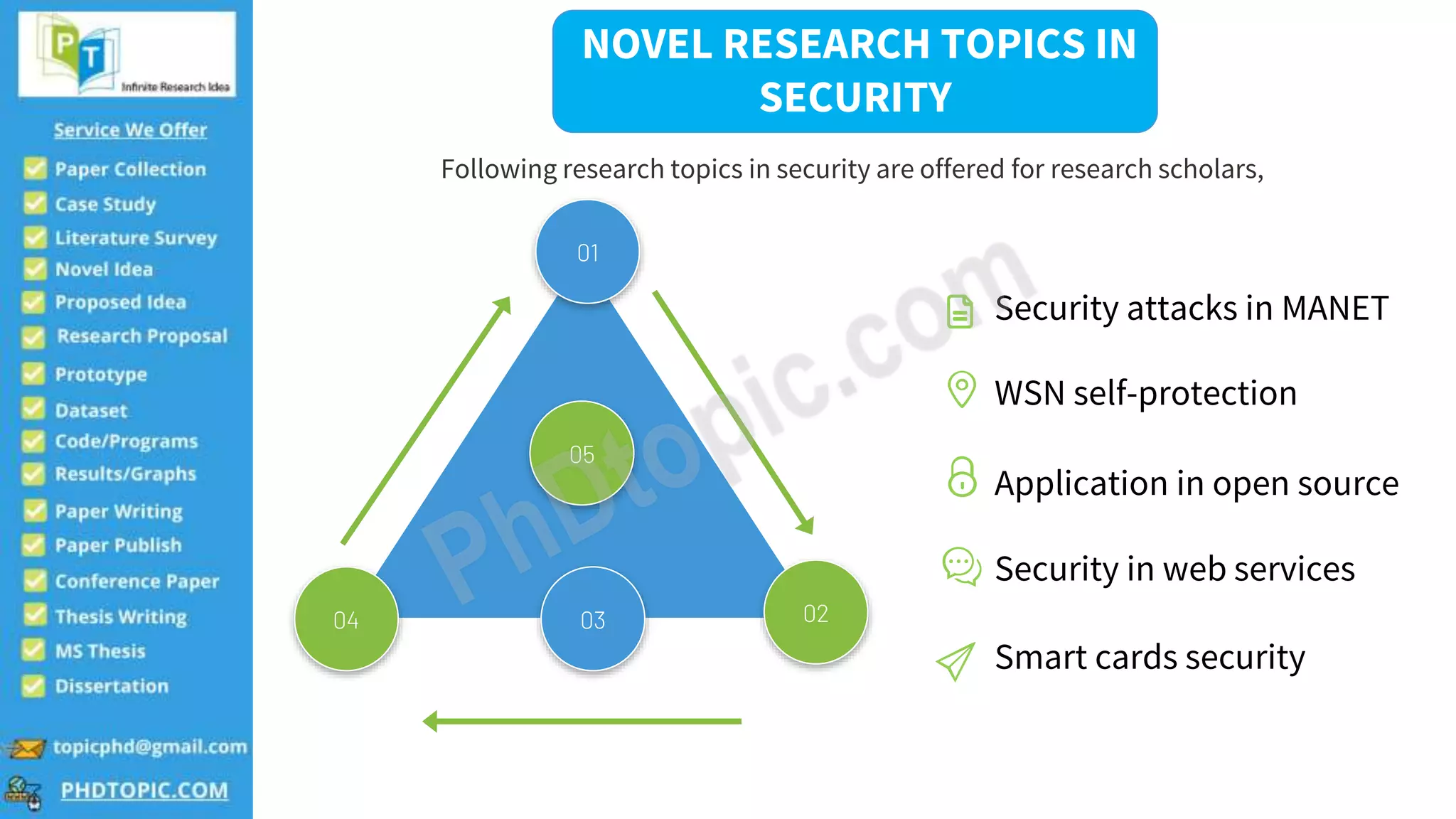


The document provides guidance for PhD scholars in the field of security, outlining various tools and important concepts such as host-based firewall protection and wireless communications security. It also suggests novel research topics like security attacks in mobile ad-hoc networks and applications in open-source security. Contact information for further inquiries is included.




