Embed presentation
Download to read offline
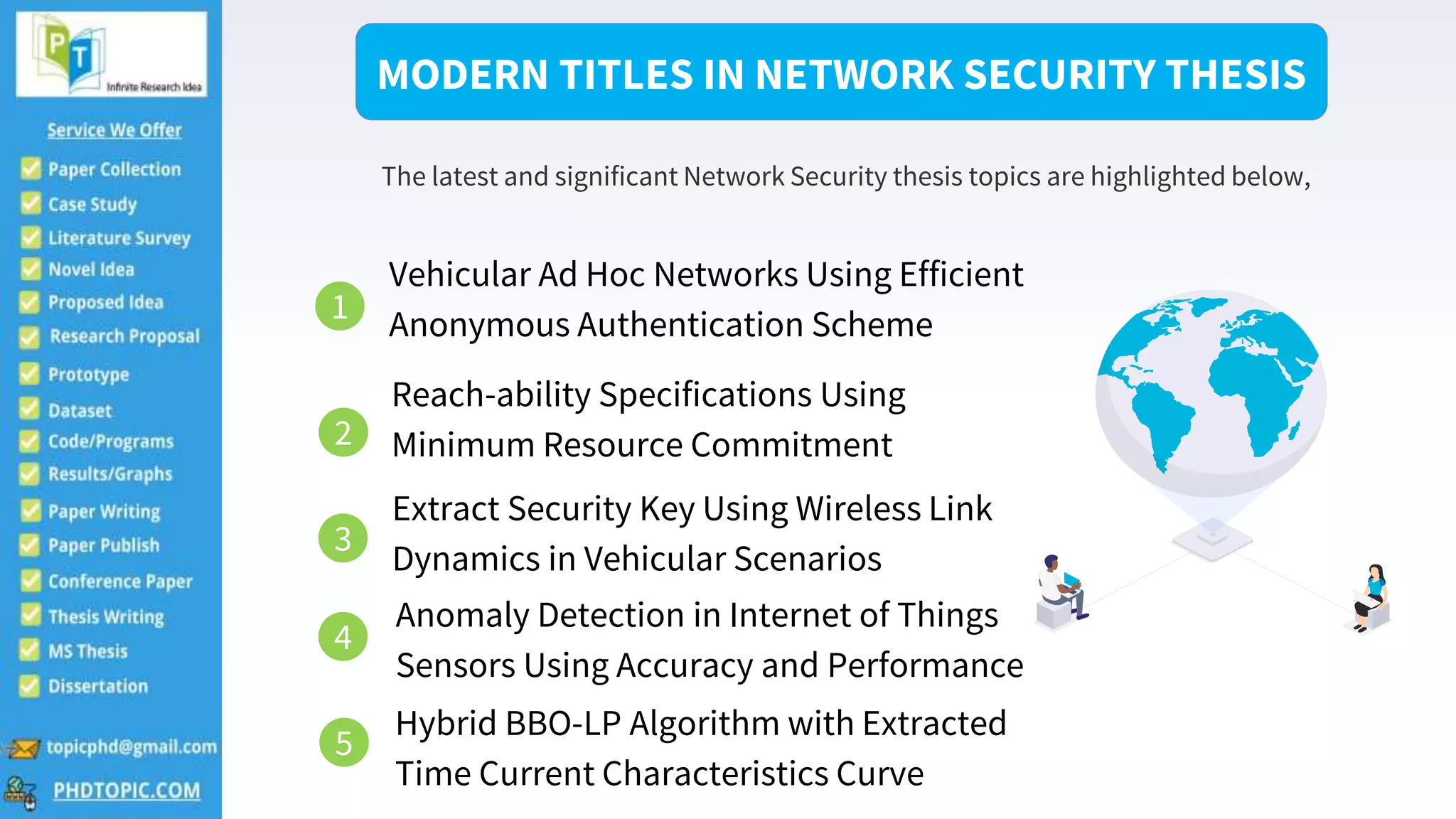
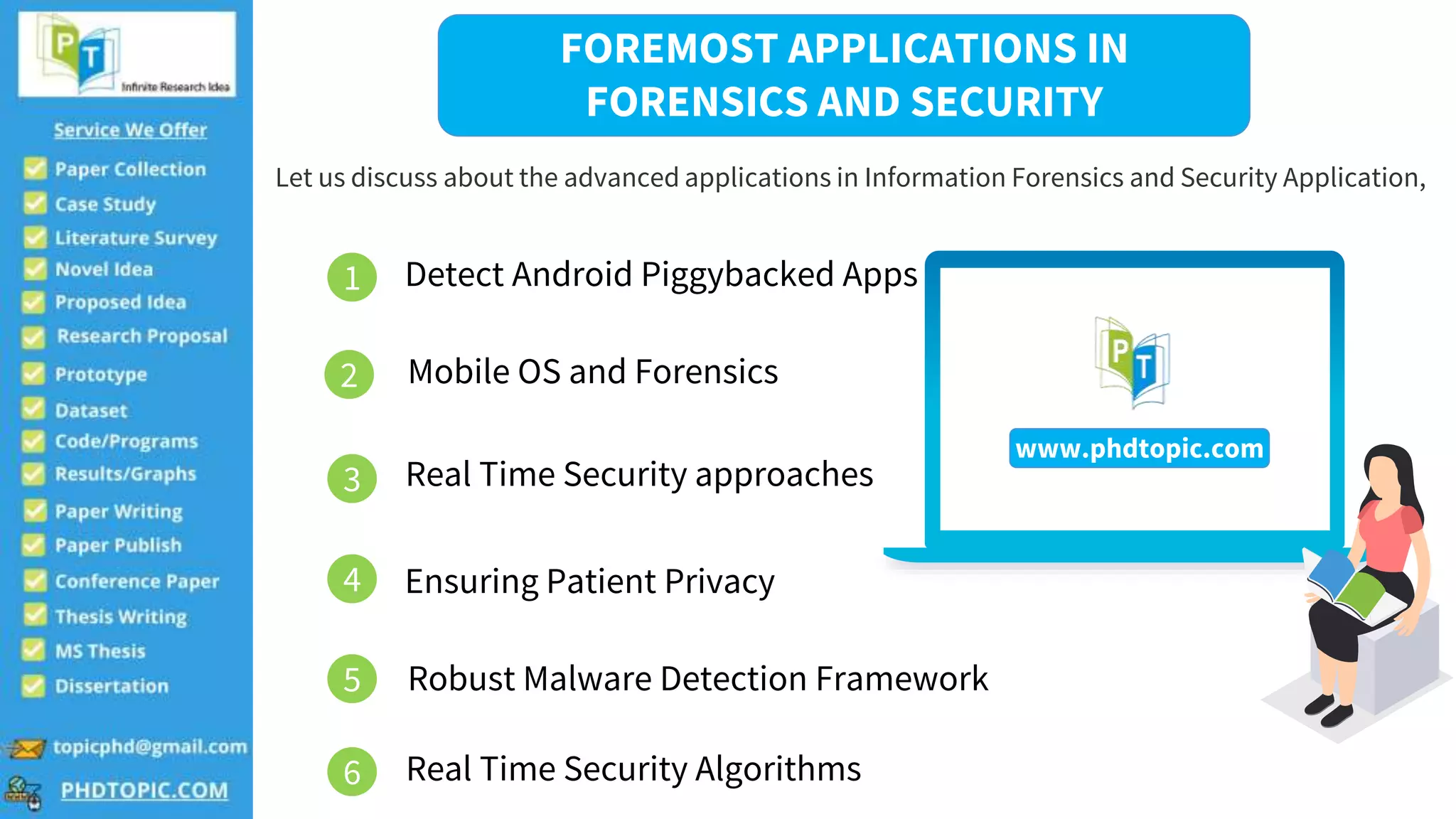
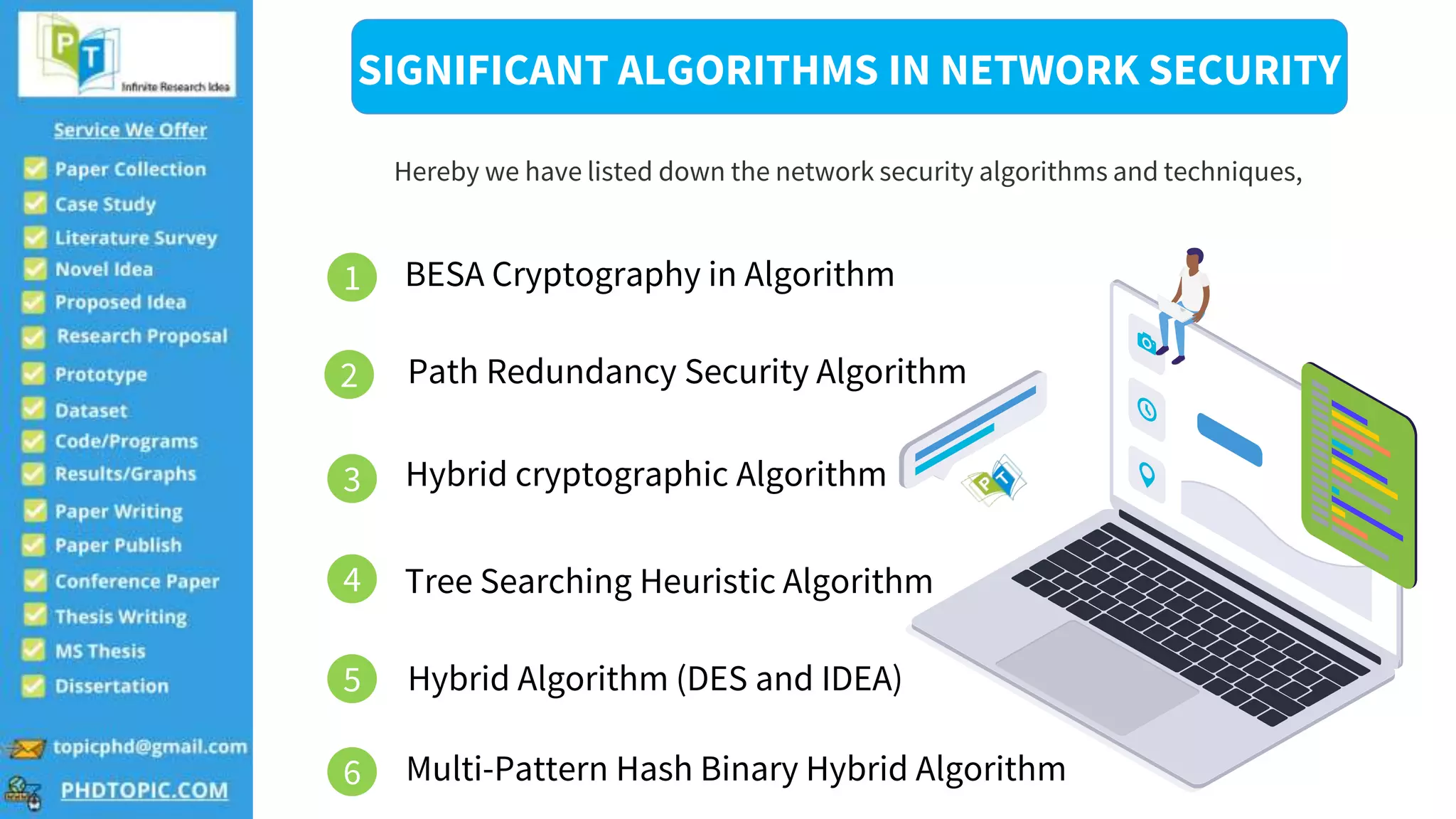


The document lists modern and significant thesis topics in network security, including vehicular ad hoc networks and anomaly detection in IoT sensors. It also highlights advanced applications in information forensics and various security algorithms such as hybrid cryptographic and multi-pattern hash algorithms. Contact information for further inquiries is provided at the end.




