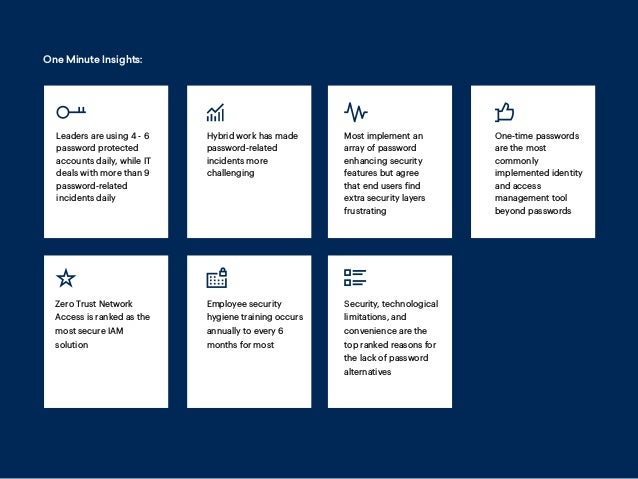
In 2022, IT teams report handling 4-6 password-protected accounts daily, with many facing over 9 password-related incidents, which have become more challenging due to hybrid work. Common security measures include minimum password complexity and regular resets, yet end users find added security layers frustrating, impacting their engagement. There is a growing belief that alternatives to passwords will emerge as technological, security, and convenience barriers are addressed.





![“Password management is one of [the] biggest pains even with
the self-service capabilities. In most cases end users are simply
lazy and unwilling to take responsibility.”
- VP, manufacturing industry, 10,000+ employees
“Passwords are a dying breed that will eventually be replaced.
Too many to remember ...”
- C-suite, software industry, 1,000 - 5,000 employees](https://image.slidesharecdn.com/gpi2022-05-17passwordin2022slideshowv1-220602073531-bcc9a1ee/95/Password-in-2022-7-638.jpg)











![“It's becoming quite burdensome because
everything we do these days requires a
password, not all systems accept special
characters and minimum complexity
requirements. It's impossible to remember
everything so we resort to writing things down
or using the same password for everything.”
- Director, software industry, 10,000+ employees
“With the amount and speed of
compute growing as fast as it is,
we need to start thinking
differently and come up with
better ways than a password.
What took years to crack, takes
minutes or seconds now.”
- VP, retail industry, 10,000+ employees
“[Password security has] improved over the years,
but the hackers have improved faster. The state
sponsored activity is most troubling and more
companies need to take that more seriously.”
- Director, manufacturing industry, 10,000+ employees
“Passwords have to go and
IAM technology is going to
replace passwords.”
- Director, 1,000 - 5,000 employees,
manufacturing industry](https://image.slidesharecdn.com/gpi2022-05-17passwordin2022slideshowv1-220602073531-bcc9a1ee/95/Password-in-2022-19-638.jpg)

