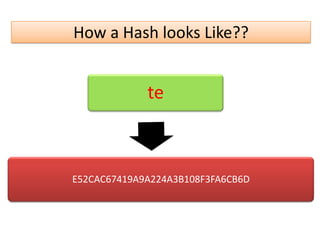
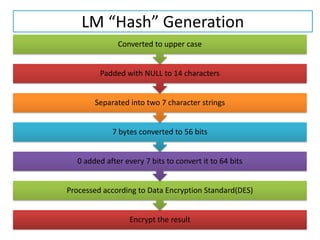
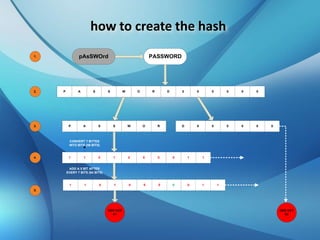
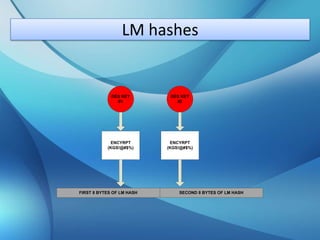
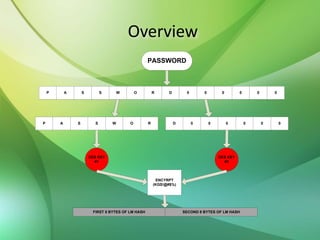
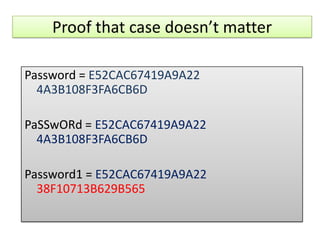
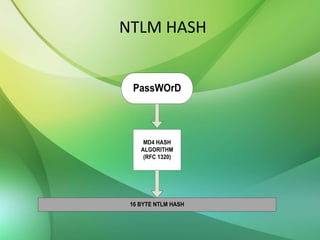
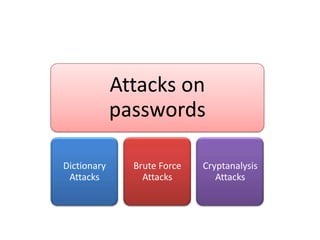
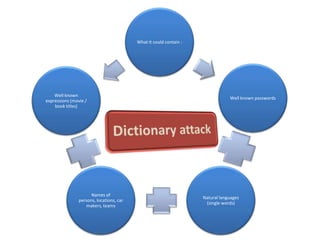
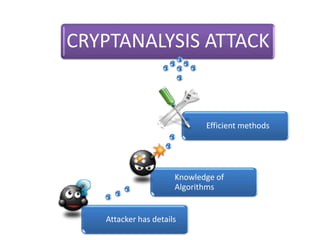
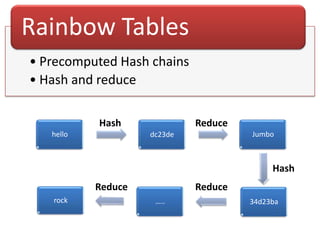
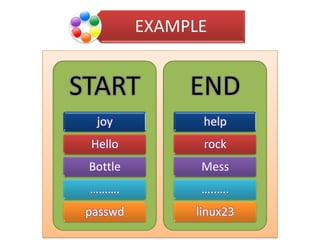
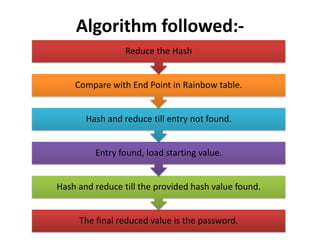
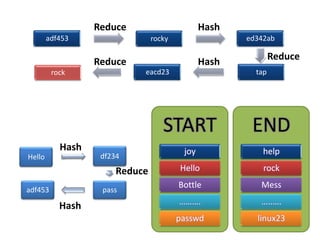
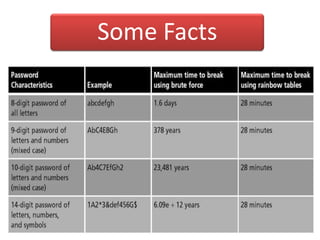
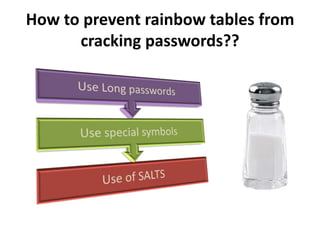
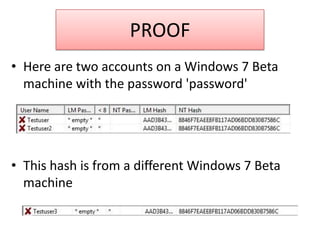
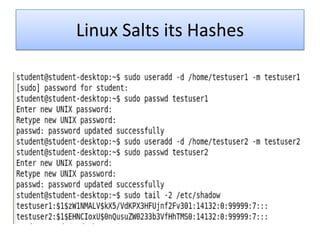
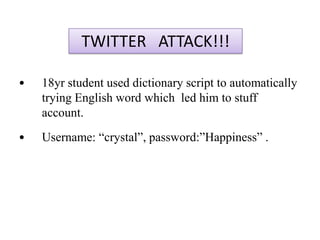
The document explains the concepts of password hashing in Windows systems, detailing the differences between LM and NTLM hashes. It highlights the security vulnerabilities of LM hashes, the implementation of NTLM hashes using the MD4 algorithm, and the significance of salting in preventing rainbow table attacks. Additionally, it discusses various types of brute force attacks and provides examples of real-world password cracking incidents.