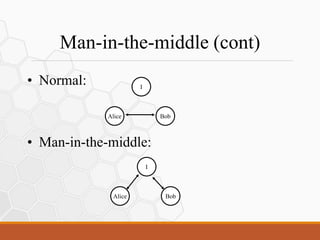
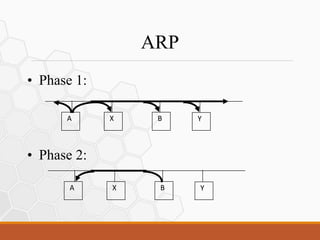
Network sniffing tools like Wireshark can capture network traffic containing usernames, passwords, emails and other data. ARP poisoning allows an attacker to intercept traffic by falsifying ARP entries and acting as a man-in-the-middle using tools like Cain and Abel, enabling the capture and modification of network traffic.