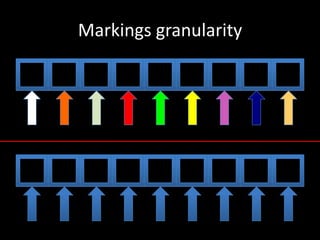
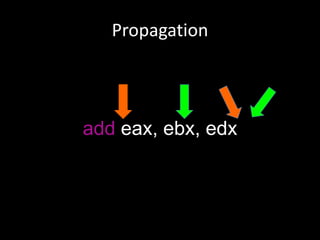
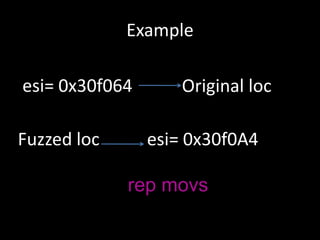
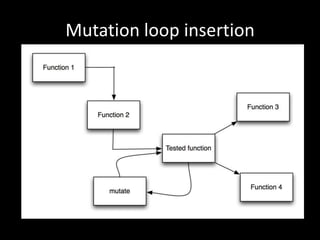
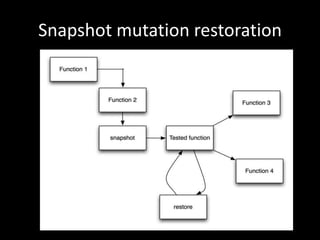
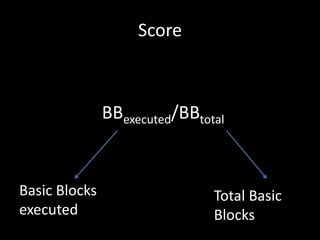
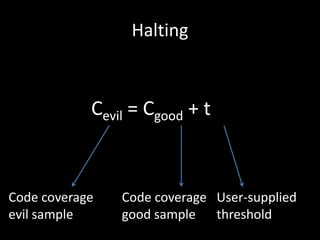
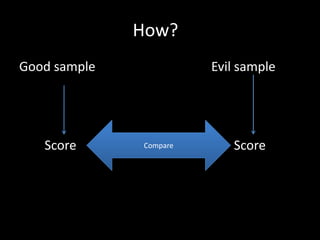
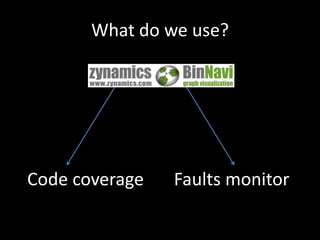
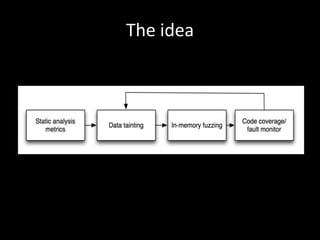
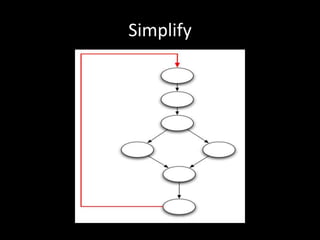
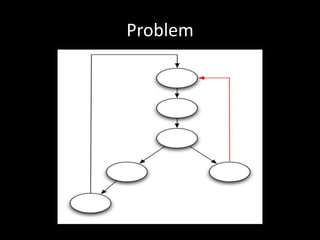
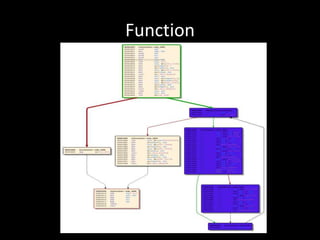
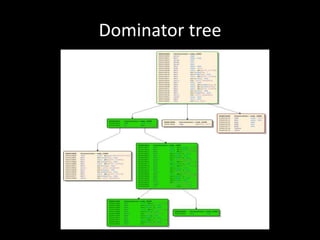
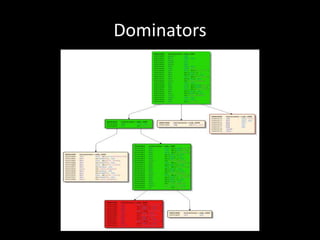
The document discusses various fuzzing techniques including dumb fuzzing, smart fuzzing, evolutionary fuzzing, using cyclomatic complexity as a filter, detecting implicit loops with dominator trees, performing in-memory fuzzing by mutating memory locations and restoring snapshots, and comparing code coverage of good and mutated samples to determine when halting criteria is met. The speaker hopes to convey an understanding of these ideas through pictures rather than traditional presentation elements. Questions from the audience are also discussed.























![ExampleTaint SourceTaint markmovl0x4[eax], ebx](https://image.slidesharecdn.com/0knowfuzz-bh-100210153540-phpapp01/85/0-knowledge-fuzzing-38-320.jpg)