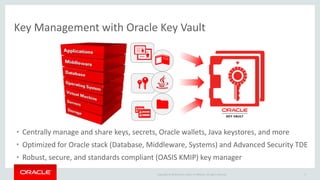
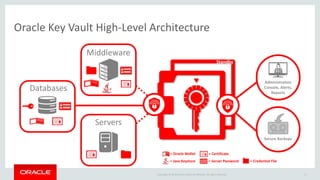
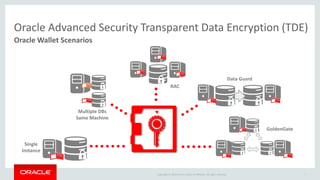
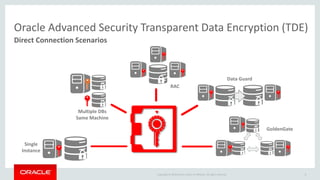
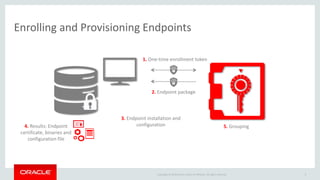
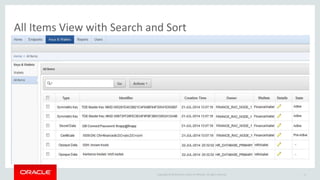
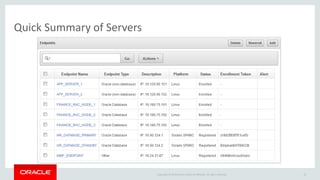
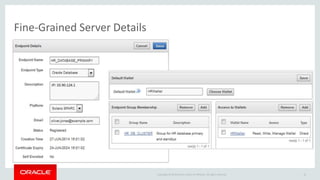
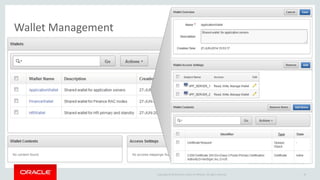
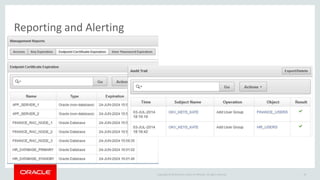
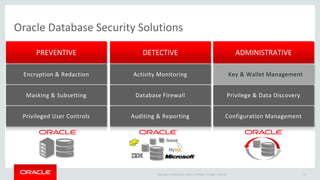
The document introduces Oracle Key Vault for centralized encryption key management. It discusses key management challenges around proliferation of keys, sharing keys, availability, and regulatory compliance. Oracle Key Vault provides a secure key manager that is optimized for Oracle software and compliant with standards. It allows centrally managing and sharing keys across databases, middleware, and systems. The appliance-based solution provides tools for enrollment, provisioning, user management, reporting, and wallet administration.