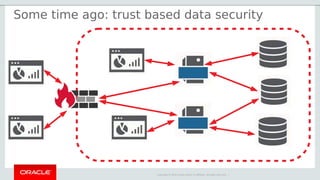
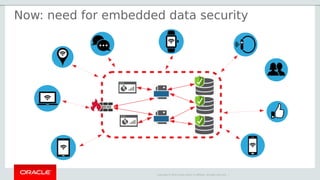
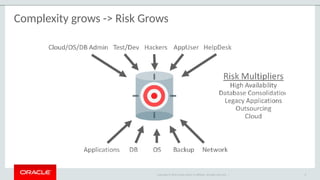
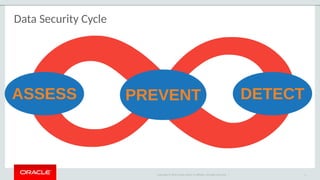
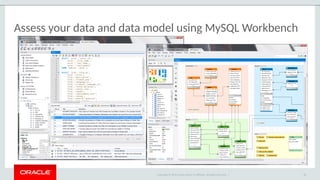
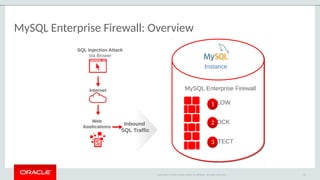
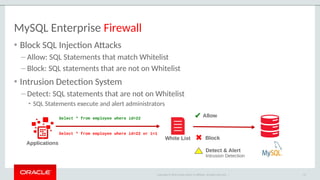
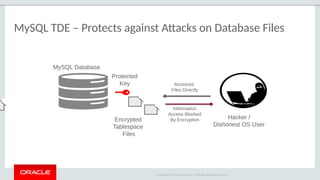
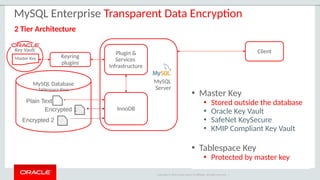
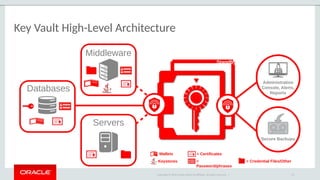
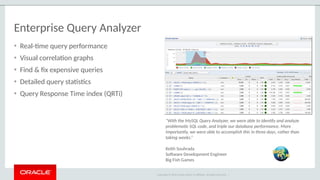
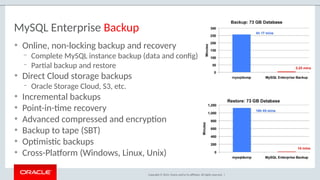
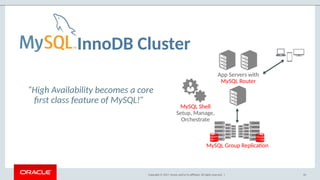
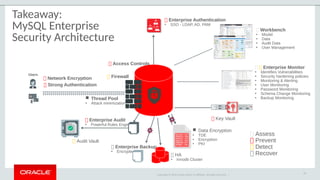
The document outlines the security features and capabilities of MySQL, including its role in data protection and compliance with GDPR regulations. It discusses various security measures such as transparent data encryption, SQL injection protection, and auditing for monitoring and preventing data breaches. The document also emphasizes the importance of integrated security management and the architectural design of MySQL for modern data security needs.