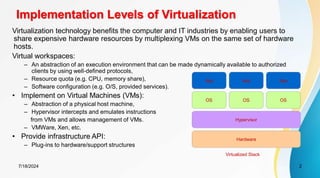
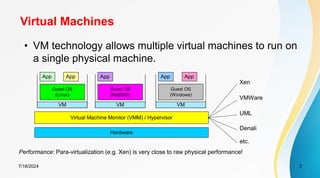
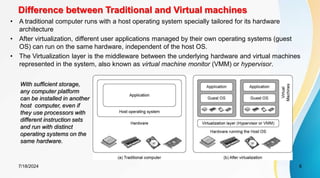
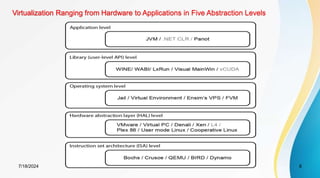
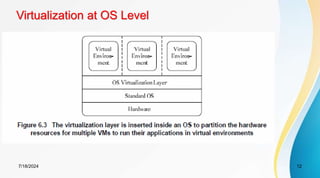
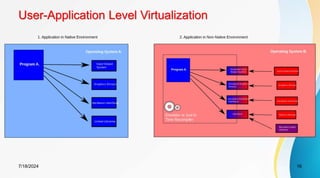
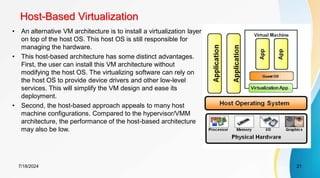
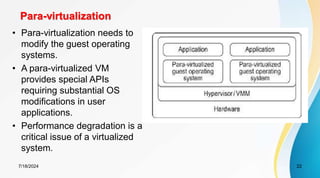
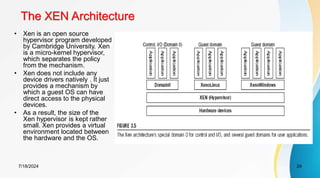
The document discusses cloud virtualization and the architecture of virtual machines (VMs), detailing different implementation levels and the advantages of virtualization technology, such as enhanced resource sharing, easier machine management, and cost-efficiency through cloud computing. It also contrasts traditional machines with virtualized systems, outlining the middleware role of hypervisors, and highlights various virtualization strategies including hardware, operating system, and application-level virtualization. Additionally, the document touches on PelicanHPC, a method for setting up high-performance computing clusters without altering existing systems.