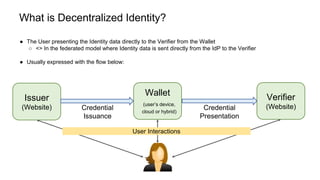
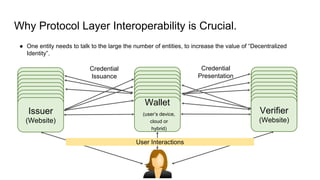
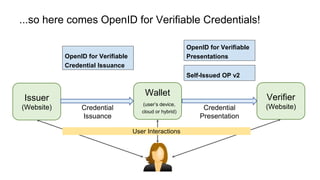
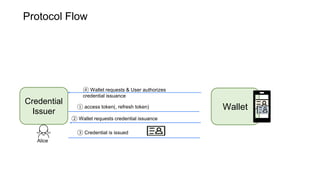
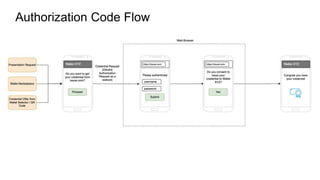
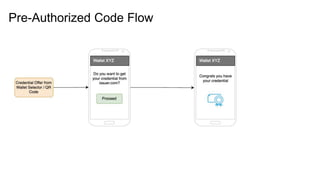
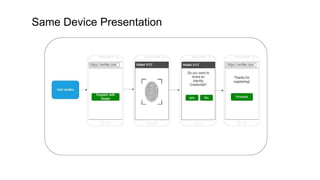
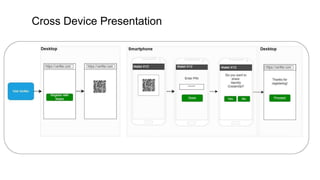
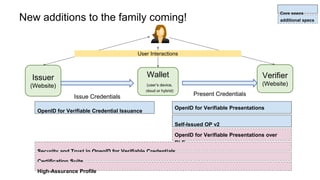
The document outlines how to establish interoperable decentralized identity systems using OpenID for verifiable credentials, emphasizing the benefits of privacy, security, and efficient verification processes. It discusses challenges, such as the diversity of protocols and trust establishment, and presents solutions like utilizing existing protocols and designing format-agnostic approaches. Additionally, it highlights the adoption of OpenID for various applications and encourages implementers to actively engage with the specifications for practical use cases.