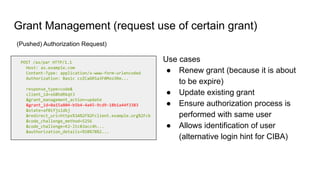
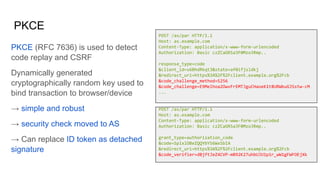
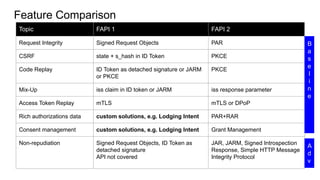
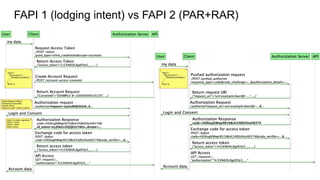
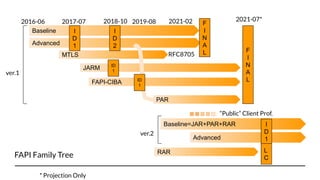
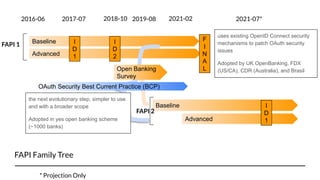
FAPI 1 and 2 are security and interoperability profiles for OAuth that address high security requirements. FAPI 1 patched OAuth security issues and added features like CIBA mode and conformance testing. FAPI 2 aims to be simpler to use with mechanisms like PAR and broader scope through features like RAR and grant management. While some ecosystems use FAPI 1, FAPI 2 covers additional authorization needs and fits better with OpenID Connect, though incremental adoption of FAPI 2 features with FAPI 1 is possible.




![Signed Requests
{
"scope":"openid consent:urn-amazingbank-0be7a3bb-33e6-4d73-b60a-9523aee6cc0d accounts",
"response_type":"code id_token",
"redirect_uri":"https://tpp.localhost/cb",
"code_challenge":"0q5idWeuyFAGeHHpawD3k4mjE7WzPhw6hOdKbnAQY7s",
"code_challenge_method":"S256",
"state":"19a1456013b8be71e6ce89916c9723e0642e1eb42a9360146cc84178f2bc928e",
"nonce":"8dedaf2c53f7ba7294825ca25e45aa544c3feda8fd4ac16220c216e973ad5fd7",
"claims":{
"id_token":{
"auth_time":{
"essential":true
},
"cpf":{
"values":[
"16386335767"
],
"essential":true
},
"given_name":{
"essential":true
},
"acr":{
"values":[
"brasil:openbanking:standard"
],
"essential":true
}
}
},
"max_age":300,
"iss":"clientIdFromAmazingBank",
"aud":"https://auth.amazingbank.com.br",
"client_id":"clientIdFromAmazingBank",
"jti":"_fj7iamgC1wDzh8KXaJ7XzJiEK_s25DhoDs7uAxpU-k",
"iat":1618672338,
"exp":1618672638,
"nbf":1618672338
}
● Protect integrity and
authenticity of request
● Request can also be
encrypted to protect
confidentiality
https://server.example.com/authorize?
response_type=code%20id_token
&client_id=s6BhdRkqt3
&redirect_uri=https%3A%2F%2Fclient.example.org%2Fcb&
&request=eyJhbGciOiJSU...zCYIb_NMXvtTIVc1jpspnTSD7xMbpL-2QgwUsAlMGzw](https://image.slidesharecdn.com/comprehensiveoverviewfapiandfapi2-210528080418/85/Comprehensive-overview-FAPI-1-and-2-6-320.jpg)





![Rich Authorization Requests (RAR)
enable fine-grained and complex consents
captured as JSON objects.
● Structure of authorization details can
be defined as needed (e.g. per
jurisdiction and AAP)
● Supports Multi-Consents
→ Can replace scopes + related
authorization data (e.g. in lodging intents)
[
{
"type":"payment_initiation",
"instructedAmount":{
"currency":"AUD",
"amount":"123.50"
},
"creditorName":"Merchant123",
"creditorAccount":{
"bsb":"123-456",
"accountNumber":"1234567890"
},
"paymentDescription":"INV123456 Description123"
}
]
[
{
"type":"brasil:openbanking:standard:data",
"permissions":[
"ACCOUNTS_READ"
],
"expirationDateTime":"2021-05-21T08:30:00Z",
"transactionFromDateTime":"2021-01-01T00:00:00Z",
"transactionToDateTime":"2021-02-01T23:59:59Z"
}
]](https://image.slidesharecdn.com/comprehensiveoverviewfapiandfapi2-210528080418/85/Comprehensive-overview-FAPI-1-and-2-13-320.jpg)

![Grant Management (request new grant id)
POST /as/par HTTP/1.1
Host: as.example.com
Content-Type: application/x-www-form-urlencoded
Authorization: Basic czZCaGRSa3F0Mzo3Rm...
response_type=code&
client_id=s6BhdRkqt3
&grant_management_action=create
&state=af0ifjsldkj
&redirect_uri=https%3A%2F%2Fclient.example.org%2Fcb
&code_challenge_method=S256
&code_challenge=K2-ltc83acc4h...
&authorization_details=%5B%7B%2...
HTTP/1.1 200 OK
Content-Type: application/json
Cache-Control: no-cache, no-store
{
"access_token": "2YotnFZFEjr1zCsicMWpAA",
"token_type": "example",
"expires_in": 3600,
"refresh_token": "tGzv3JOkF0XG5Qx2TlKWIA",
"grant_id":"0a15a804-b5b4-4a45-9cd9-18b1a44f3383",
"authorization_details": [...
]
}
(Pushed) Authorization Request) Token Response](https://image.slidesharecdn.com/comprehensiveoverviewfapiandfapi2-210528080418/85/Comprehensive-overview-FAPI-1-and-2-15-320.jpg)
![Grant Management (API)
GET /grants/0a15a804-b5b4-4a45-9cd9-18b1a44f3383
Host: as.example-bank.com
Authorization: Bearer 2YotnFZFEjr1zCsicMWpAA
HTTP/1.1 200 OK
Cache-Control: no-cache, no-store
Content-Type: application/json
{
"authorization_details":[...]
}
DELETE /grants/0a15a804-b5b4-4a45-9cd9-18b1a44f3383
Host: as.example-bank.com
Authorization: Bearer 2YotnFZFEjr1zCsicMWpAA
HTTP/1.1 204 No Content
Query Revoke](https://image.slidesharecdn.com/comprehensiveoverviewfapiandfapi2-210528080418/85/Comprehensive-overview-FAPI-1-and-2-16-320.jpg)