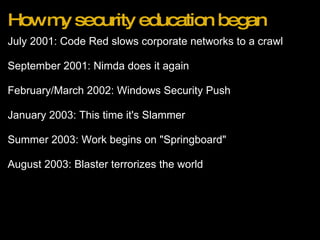
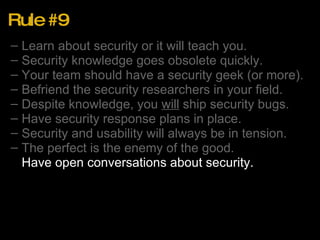
The document outlines 10 rules for developing software with security in mind. The rules are:
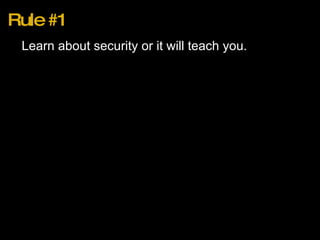
1. Learn about security or it will teach you the hard way through vulnerabilities.
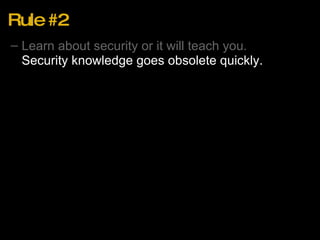
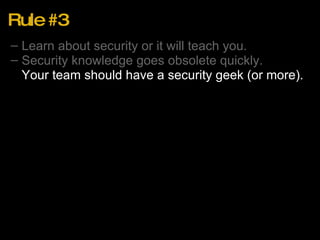
2. Security knowledge becomes obsolete quickly, so keep learning. Have a security expert on your team.
3. Befriend security researchers and let them test your software for vulnerabilities.
4. Expect to ship software with security bugs despite your best efforts.
5. Have security response plans to quickly address issues that arise.
6. Security and usability will always be in tension so aim for good, not perfect.
7. Have open conversations about security with users and researchers to build trust.
8. There may