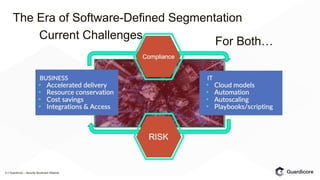
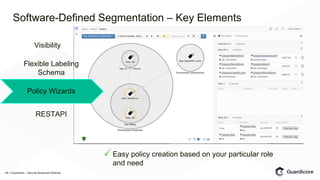
The Guardicore webinar discusses software-defined segmentation, highlighting its necessity due to challenges with traditional segmentation methods, particularly in terms of visibility and management. It outlines rollout steps for software-defined segmentation and emphasizes its advantages over older techniques, including numerous use cases like compliance and protection of sensitive data. Key elements for successful implementation include broad platform support, policy granularity, and real-time visibility.