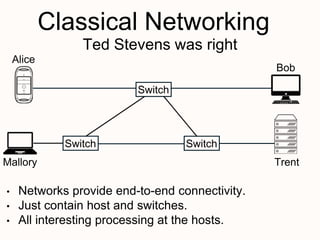
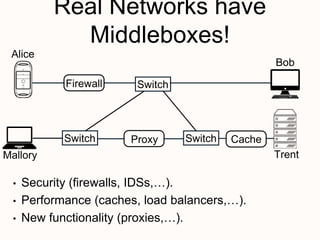
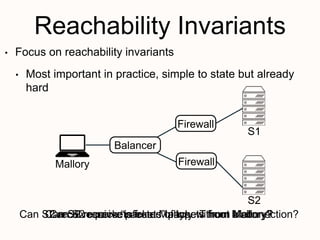
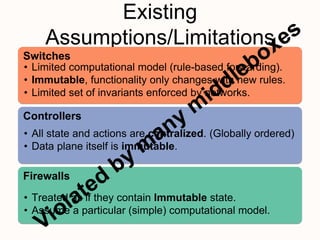
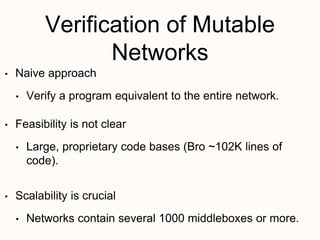
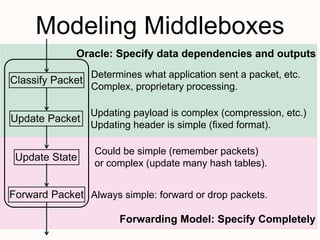
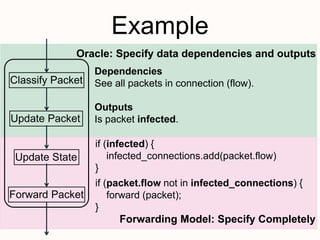
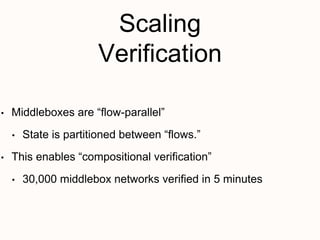
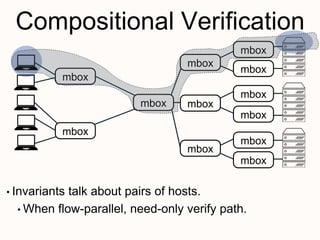
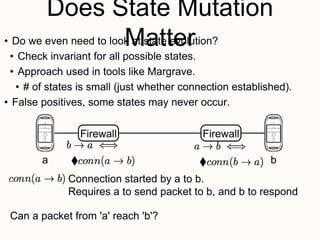
New techniques are needed to verify networks that contain mutable middleboxes with evolving state. Modeling the behavior and data dependencies of middleboxes is challenging but important to capture their functionality. A scalable approach is to leverage the flow-parallel nature of middleboxes and use compositional verification to check connectivity properties between pairs of hosts by only analyzing the path between them. Specifying middleboxes at the right level of abstraction is also key to make verification tractable.