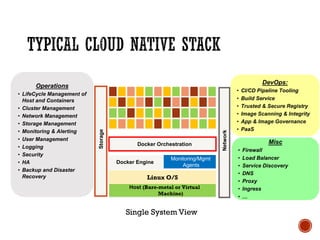
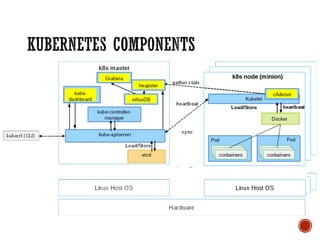
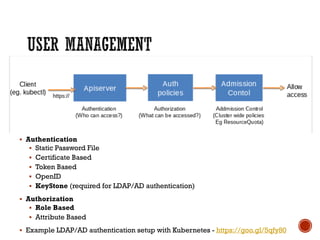
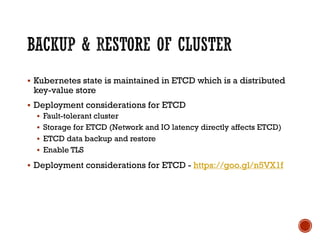
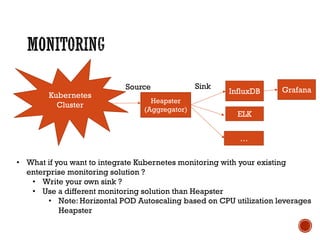
This document discusses best practices for setting up a Docker and Kubernetes environment. It covers topics like Docker storage drivers, Docker networking, Kubernetes authentication and authorization, exposing services, integrating logging and monitoring. The key recommendations are to use OverlayFS or Devicemapper storage, Calico networking, Kubernetes security policies, namespaces and RBAC, and Ingress for exposing services. ETCD backup and fault tolerance is also important.