The document presents 'Oblivm', a programming framework for secure multi-party computation that simplifies cryptographic programming by utilizing improved garbled circuit protocols. It supports various data types and optimization techniques, providing a reusable environment for developing cryptographic algorithms and applications in data mining and graph algorithms. Key features include secure execution traces, efficient memory management methods, and support for extensive programming language functionality to enhance flexibility and usability.





![Standard Types
Variables or arrays are either of a secure or public type.
secure variables or arrays are secretly shared between two parties.
i.e. neither party sees the value.
public variables or arrays are seen by both parties.
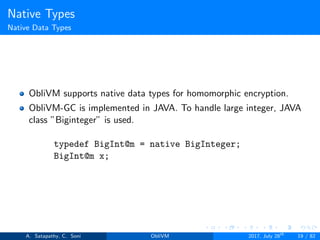
secure int10[public 1000] keys: Array contents are secret shared
but indices to array are public. No ORAM is used. 10 in int10
indicated 10 bits key value.
secure int10[secure 1000] keys: Array contents are secret shared
and indices to array are secure. Trivial ORAM is used. 10 in int10
indicated 10 bits key value.
public int10[public 1000] keys : Arrays contents are seen by
both parties.
A. Satapathy, C. Soni ObliVM 2017, July 28th
11 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-11-320.jpg)
![Standard Types
Figure 3.1: Data distribution of secure int10[public 4] P1 and
secure int10[public 4] P2 and their access
A. Satapathy, C. Soni ObliVM 2017, July 28th
12 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-12-320.jpg)
![Standard Types
Figure 3.2: Data distribution of secure int10[secure 4] P1 and
secure int10[secure 4] P2 and their access
A. Satapathy, C. Soni ObliVM 2017, July 28th
13 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-13-320.jpg)
![Generic Types
Generic Variable
ObliVM uses ’struct’ keyword to define composite data type.
It supports generic data type like C++ template.
Suppose a binary tree with public key value but secret node data can
be defined using struct. node size is 1000.
struct KeyValueTable<T>{
secure int10[public 1000] keys;
T[public 1000] values;
};
Generic type T similar to template in C++. Data type T to be
secret-shared.
A. Satapathy, C. Soni ObliVM 2017, July 28th
15 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-15-320.jpg)
![Generic Types
Generic Constant
ObliVM supports generic constants to improve flexibility and
reusability of programming language. An example is given below.
struct TreeNode@m<T>{
public int@m key;
T value;
public int@m left, right;
};
struct Tree@m<T>{
TreeNode<T>[public (1<<m) - 1] nodes;
public int@m root;
};
@m is the generic constant. Here @m indicates m bits integer.
A. Satapathy, C. Soni ObliVM 2017, July 28th
16 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-16-320.jpg)
![Generic Types
Generic Function
ObliVM supports generic functions to bring modularity in program.
A generic function, to search the value associated with a given key in
previously defined binary tree is given below.
T Tree@m<T>.search(public int@m key){
public int@m now = this.root, tk;
T ret;
while (now != -1){
tk = this.nodes[now].key;
if (tk == key) {ret = this.nodes[now].value;}
if(tk <= key) {now = this.nodes[now].right;}
else {now = this.nodes[now].left}; }
return ret; }
A. Satapathy, C. Soni ObliVM 2017, July 28th
17 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-17-320.jpg)

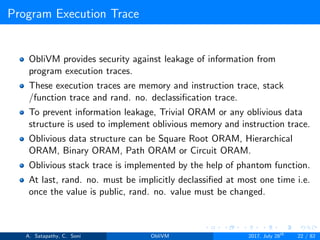
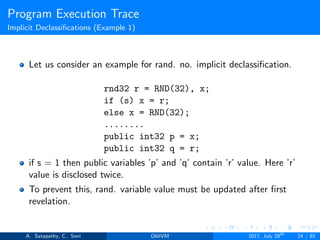

![Program Execution Trace
Stack/Function Trace
Let’s consider a native function implementation.
secure int32 prefixSum (public int32 n){
secure int32 ret = a[n];
a[n] = 0;
if (n != 0) ret + prefixSum (n - 1);
return ret;
}
If n != 0 is true, prefixSum will be executed which made function
trace unoblivious. To avoid this, phantom keyword is used.
A. Satapathy, C. Soni ObliVM 2017, July 28th
27 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-27-320.jpg)
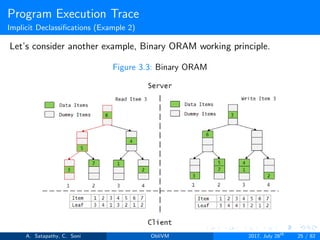
![Program Execution Trace
Phantom Function
phantom secure int32 prefixSum (public int32 n){
secure int32 ret = a[n];
a[n] = 0;
if (n != 0) ret + prefixSum (n - 1);
return ret;
}
Here prefixSum is a phantom function. function prefixSum will be
called, even if ’n != 0’ is false.
If condition is true, ’0’ will be assigned to ’a’. If condition is false,
value of ’a’ will not change i.e the previous value is retained.
Both cases, same amount of memory traces are generated.
A. Satapathy, C. Soni ObliVM 2017, July 28th
29 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-29-320.jpg)

![Loop Coalescing
The process of converting nested loops to a single loop is called loop
coalescing. It is used for code optimization.
It gains performance on certain architecture. It reduces higher
dimensional loop to a single dimension.
for (i = 0; i < N; i++) {
for (j = 0; j < M;
j++) {
a[i][j]=b[i][j];
}
}
for (ij = 0; i < MN; ij++)
{
i = ij / M;
j = ij % M;
a[i][j]=b[i][j];
}
A. Satapathy, C. Soni ObliVM 2017, July 28th
32 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-32-320.jpg)
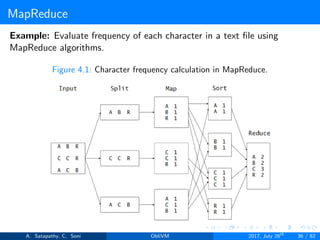
![MapReduce
MapReduce algorithm has two functions. MAP and REDUCE.
MAP under MAPPER class, takes input and tokenizes it.
REDUCE under REDUCER class, finds matching pairs and reduce
them.
Algorithm (Map)
Given: int K[ ] = {ki}i ∈ [n]. ki ∈ domain ’D’
1: function MAP(int K[ ])
2: Initialize C ← Φ
3: for i = 1 to n do:
4: C ← C (ki, 1)
5: end for
6: return C
7: end function
A. Satapathy, C. Soni ObliVM 2017, July 28th
34 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-34-320.jpg)
![MapReduce
Algorithm (Reduce)
Given: (k1, v1), (k2, v2), (k3, v3), ....,(kj, vj).
1: Initialize int Z[ ] ← 0, t ← 0.
2: for i = 1 to j do:
3: if ki = k do:
4: Z[t] ← vi.
5: t ← t + 1
6: function REDUCE(int k, int Z[ ])
7: Initialize Sum ← 0, n ← |Z[ ]|
8: for i = 1 to n do:
9: Sum ← Sum + Z[i]
10: return Sum
11: end function
A. Satapathy, C. Soni ObliVM 2017, July 28th
35 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-35-320.jpg)



![MapReduce
Oblivious MapReduce
Pair<K,V>[public n] MapReduce@m@n<I,K,V>(I[public m]
data, Pair<K,V> map(I), V reduce(K,V,V), V initialVal,
int2 cmp(K, K)) {
public int32 i;
Pair<K,V>[public m] d2;
for (i = 0; i<m; i++)
d2[i] = map(data[i])
sort@m<K,V>(d2, 1, cmp);
K key = d2[0].k;
V val = initialVal;
Pair<int1, Pair<K,V>>[public m] res;
for (i = 0; i<m; i++) {
res[i].v.k = key;
res[i].v.v = val;
if (cmp(key, d2[i+1].k)) == 0 {
A. Satapathy, C. Soni ObliVM 2017, July 28th
41 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-41-320.jpg)
![MapReduce
Oblivious MapReduce
res[i].k.val = 1; }
else {
res[i].k.val = 0;
key = d2[i+1].k;
val = initialVal; }
val = reduce(key, val, d2[i+1].v); }
res[m-1].k.val = 0;
res[m-1]v.k = key;
res[m-1].v.v = val;
sort@m<int1, Pair<K,V>>(res, 1, zeroOneCmp);
Pair<K,V>[public n] top;
for (i = 0; i < n; i = i+1)
top[i] = res[i].v;
return top; }
A. Satapathy, C. Soni ObliVM 2017, July 28th
42 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-42-320.jpg)

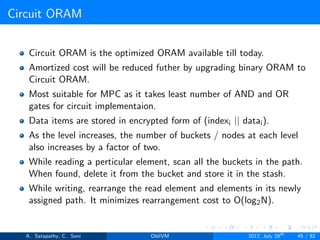
![Circuit ORAM
#define BUCSIZE 3
#define STASHSIZE 33
struct Block@n<T> {
int@n id, pos;
T data; };
struct CircuitOram@n<T> {
dummy Block@n<T>[public 1<<n+1][public BUCSIZE]
buckets;
dummy Block@n<T>[public STASHSIZE] stash; };
phantom T CircuitOram@n<T>.readAndRemove (int@n id,
rnd@n pos) {
public int32 pubPos = pos;
public int32 i = (1 << n) + pubPos;
T res;
for (public int32 k = n; k>=0; k=k-1) {
for (public int32 j=0;j<BUCSIZE;j=j+1) {
A. Satapathy, C. Soni ObliVM 2017, July 28th
46 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-46-320.jpg)
![Circuit ORAM
if (buckets[i][j] != null &&
buckets[i][j].id == id){
res = buckets[i][j].data;
buckets[i][j] = null; } }
i = (i-1) / 2; }
for (public int32 i=0;i<STASHSIZE;i=i+1) {
if (stash[i]!=null && stash[i].id==id) {
res = stash[i].data;
stash[i] = null; } }
return res;}
A. Satapathy, C. Soni ObliVM 2017, July 28th
47 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-47-320.jpg)
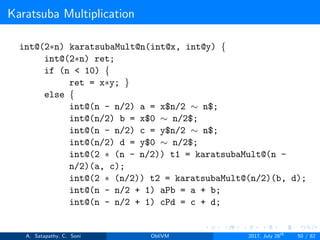

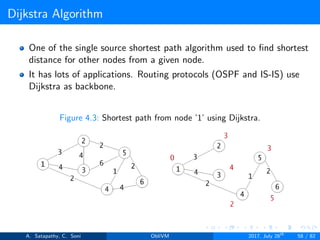
![Dijkstra Algorithm
Given Input Secrets: Source node ’s’, Adjacency list ’e’ and sum of out
degrees s[u].
1: Initialize dis = [∞, ∞, ∞, .....,∞] and dis[s] = 0
2: PQ.push(0, s)
3: while (!PQ.empty())
4: (dist, u) = PQ.deleteMin()
5: if (dist == dis[u])
6: dis[u] = -dis[u]
7: for (i = s[u]; i < s[u+1]; i++)
8: (u, v, w) = e[i]
9: newDist = dist + w
10: if (newDist < dis[v])
11: dis[v] = newDist
12: PQ.insert(newDist, v)
A. Satapathy, C. Soni ObliVM 2017, July 28th
59 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-59-320.jpg)
![Dijkstra Algorithm
Oblivious Dijkstra with Loop Coalescing
Input Secrets: Source ’s’, Adjacency list ’e’ and Sum of Out-degrees s[u].
1: Initialize dis = [∞, .....,∞] and dis[s] = 0, innerLoop = False
2: PQ.push(0, s)
3: for (i = 0 → 2V + E - 1)
4: (dist, u) = PQ.deleteMin()
5: if (dist == dis[u])
6: dis[u] = -dis[u], i = s[u], innerLoop = True
7: else
8: if i < s[u+1]
9: (u, v, w) = e[i], newDist = dist + w
10: if newDist < dis[v]
11: dis[v] = newDist, PQ.insert(newDist, v)
12: i = i + 1
13: else
14: innerLoop = False
A. Satapathy, C. Soni ObliVM 2017, July 28th
60 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-60-320.jpg)

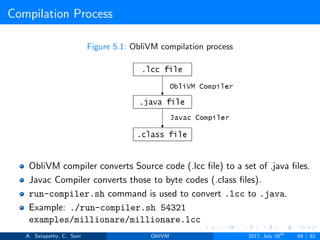
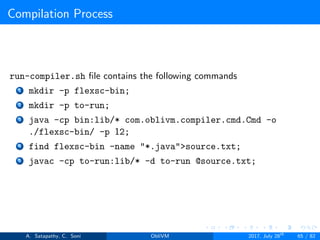
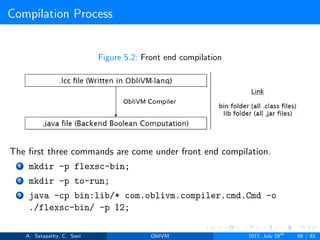
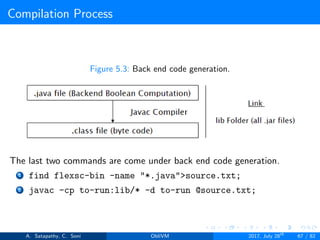


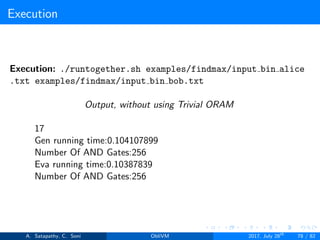
![Compilation
Find the maximum within set of numbers without using Trivial ORAM.
File location: examples/findmax3.lcc
1: package com.oblivm.backend.generated.findmax;
2: int main@n(int[public n] x, int y) {
3: int max = y;
4: for(public int i = 0; i<n; i = i + 1) {
5: if (x[i] > max) max = x[i];
6: }
7: return max;
8: }
Compilation: ./run-compiler.sh 54321 examples/findmax/
findmax3.lcc
A. Satapathy, C. Soni ObliVM 2017, July 28th
75 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-75-320.jpg)
![Compilation
Find the maximum within set of numbers using Trivial ORAM.
File location: examples/findmax2.lcc
1: package com.oblivm.backend.generated.findmax;
2: int main@n(int[n] x, int y) {
3: int max = y;
4: bfor (n) (int i = 0; i<n; i = i + 1) {
5: if (x[i] > max) max = x[i];
6: }
7: return max;
8: }
Compilation: ./run-compiler.sh 54321 examples/findmax/
findmax2.lcc
A. Satapathy, C. Soni ObliVM 2017, July 28th
76 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-76-320.jpg)

![References
C. Liu et al., ”ObliVM: A Programming Framework for Secure
Computation”, in IEEE Symposium on Security and Privacy (S&P),
2015.
”oblivm/ObliVMLang”, GitHub, 2017. [Online]. Available:
https://github.com/oblivm/ObliVMLang. [Accessed: 05- Jun- 2017].
A. Satapathy, C. Soni ObliVM 2017, July 28th
81 / 82](https://image.slidesharecdn.com/oblivm-180913163800/85/ObliVM-81-320.jpg)