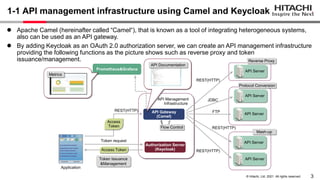
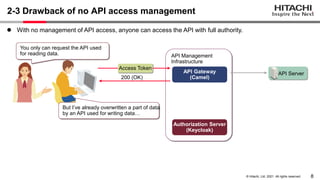
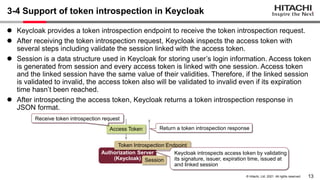
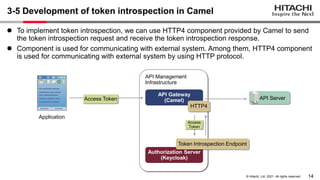
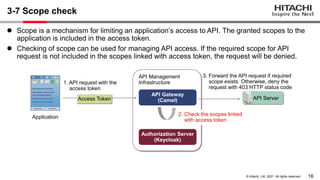
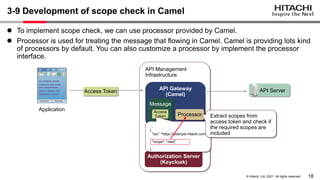
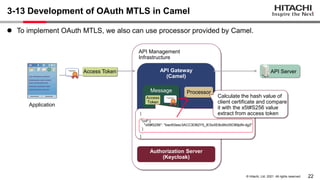
The document discusses the integration of Apache Camel and Keycloak to create a high-security API management infrastructure. It highlights security vulnerabilities such as minimal access token validation and lack of access management, and suggests enhancements through Keycloak features like token introspection, scope checks, and OAuth MTLS to mitigate these issues. The conclusion emphasizes that while the combined approach can improve security, it is essential to address the identified drawbacks.