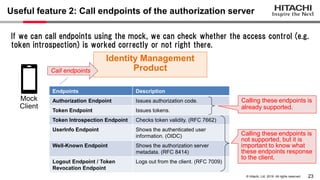
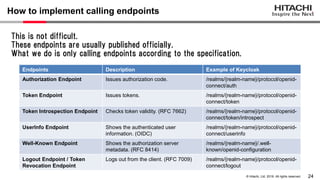
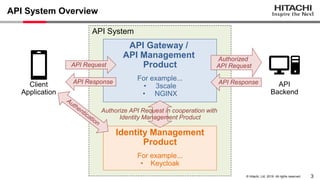
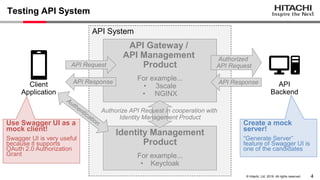
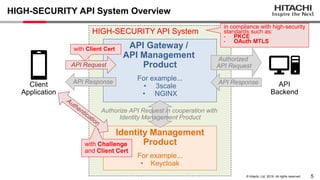
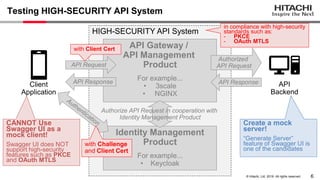
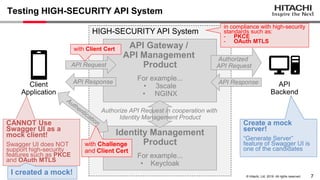
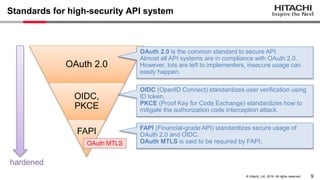
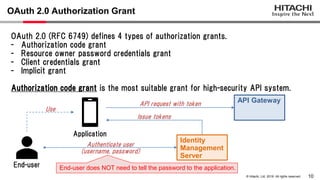
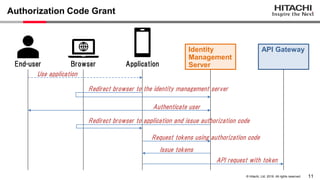
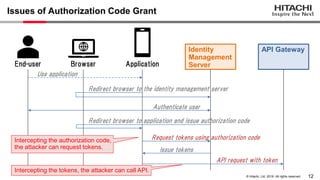
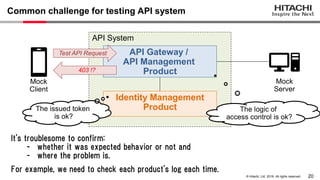
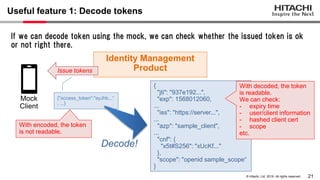
Yoshiyuki Tabata from Hitachi presented on API specifications and tools that help engineers construct high-security API systems. He discussed standards like OAuth 2.0, OIDC, PKCE, and OAuth MTLS. Useful features for testing include decoding tokens to check validity, and calling authorization server endpoints to validate access control. Implementing these features in mock servers and clients allows engineers to efficiently test if high-security requirements are met before production.






![22
© Hitachi, Ltd. 2019. All rights reserved.
How to implement decoding tokens
var accessTokenRegex = /^([^ .]+).([^ .]+).([^ .]+)[ ]*$/i;
var accessTokenResult = accessTokenRegex.exec(accessToken);
var payload = accessTokenResult[2];
var decodedPayload = decodeURIComponent(escape(atob(payload)));
var dataPayload = JSON.parse(decodedPayload);
In the access token, there are 2 kinds, "self-contained" and "reference/opaque" token.
The token we can decode is "self-contained" token and which format is JSON Web
Token (JWT).
# JWT = BASE64URL(Header).BASE64URL(Payload).BASE64URL(Signature)
Important information is included in "Payload", so extract it
using regex, and decode it.](https://image.slidesharecdn.com/apispecificationsconference2019yoshiyukitabatashare-220117123046/85/What-API-Specifications-and-Tools-Help-Engineers-to-Construct-a-High-Security-API-System-23-320.jpg)