The document discusses concepts related to concurrent and distributed systems, focusing on mutual exclusion and interactions between threads, including volatile variables, deadlocks, busy waiting, and synchronization mechanisms like mutexes and condition variables. It outlines various algorithms for mutual exclusion, such as Dekker’s and Peterson’s algorithms, and explores more advanced synchronization constructs like monitors and semaphores. Additionally, it addresses challenges like race conditions, starvation, and the readers-writers problem, while also mentioning task management and execution through executors in Java.
![Concurrent and Distributed Systems (Bechini)
MUTUAL EXCLUSION
Volatile: any write to a volatile variable establishes a happensbefore relationship with subsequent reads of
that same variable. This means that changes to a volatile variable are always visible to other threads. What's
more, it also means that when a thread reads a volatile variable, it sees not just the latest change to the
volatile, but also the side effects of the code that led up the change.
Reads and writes are atomic for all variables declared volatile (including long and double variables).
Mutual Exclusion desired properties:
1. ME guaranteed in any case
2. A process out of the Critical Section MUST NOT prevent any other to access
3. No deadlock
4. No busy waiting
5. No starvation
Deadlock: a situation in which two or more competing actions are each waiting for the other to finish, and thus
neither ever does.
A deadlockers situation can arise if all of the following conditions hold simultaneously in a system:[1]
1. Mutual Exclusion: At least one resource must be held in a nonshareable mode.[1]
Only one process
can use the resource at any given instant of time.
2. Hold and Wait or Resource Holding: A process is currently holding at least one resource and
requesting additional resources which are being held by other processes.
3. No Preemption: a resource can be released only voluntarily by the process holding it.
4. Circular Wait: A process must be waiting for a resource which is being held by another process, which
in turn is waiting for the first process to release the resource. In general, there is a set of waiting
processes, P = {P1, P2, ..., PN}, such that P1 is waiting for a resource held by P2, P2 is waiting for a
resource held by P3 and so on until PN is waiting for a resource held by P1.[1][7]
These four conditions are known as the Coffman conditions from their first description in a 1971 article by
Edward G. Coffman, Jr.[7]
Unfulfillment of any of these conditions is enough to preclude a deadlock from
occurring.
Busy waiting: In software engineering, busywaiting or spinning is a technique in which a process
repeatedly checks to see if a condition is true, such as whether keyboard input or a lock is available. In
lowlevel programming, busywaits may actually be desirable. It may not be desirable or practical to implement
interruptdriven processing for every hardware device, particularly those that are seldom accessed.
Sleeping lock: as opposite to a spinning lock, this technique puts a thread waiting for accessing a resource in
sleeping/ready mode. So, a thread is paused and its execution stops. The CPU can perform a context switch
and can keep working on another process/thread. This saves some CPU time (cycles) that would be wasted by](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-1-320.jpg)
![a spinning lock implementation. Anyway, also sleeping locks have a time overhead that should be taken into
account when evaluating which solution to adopt.
Starvation: a process is perpetually denied necessary resources to proceeds its work.[1]
Starvation may be
caused by errors in a scheduling or mutual exclusion algorithm, but can also be caused by resource leaks, and
can be intentionally caused via a denialofservice attack such as a fork bomb.
Race Condition: (or race hazard) is the behavior of an electronic, software or other system where the output
is dependent on the sequence or timing of other uncontrollable events. It becomes a bug when events do not
happen in the order the programmer intended. The term originates with the idea of two signals racing each
other to influence the output first. Race conditions arise in software when an application depends on the
sequence or timing of processes or threads for it to operate properly.
Dekker’s alg.: the first known correct solution to the mutual exclusion problem in concurrent programming.
Dekker's algorithm guarantees mutual exclusion, freedom from deadlock, and freedom from starvation.
One advantage of this algorithm is that it doesn't require special Testandset (atomic read/modify/write)
instructions and is therefore highly portable between languages and machine architectures. One disadvantage
is that it is limited to two processes and makes use of busy waiting instead of process suspension. (The use of
busy waiting suggests that processes should spend a minimum of time inside the critical section.)
This algorithm won't work on SMP machines equipped with these CPUs without the use of memory barriers.](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-2-320.jpg)
![Peterson’s alg.: a concurrent programming algorithm for mutual exclusion that allows two processes to share
a singleuse resource without conflict, using only shared memory for communication.
The algorithm uses two variables, flag and turn. A flag[n] value of true indicates that the process n wants to
enter the critical section. Entrance to the critical section is granted for process P0 if P1 does not want to enter
its critical section or if P1 has given priority to P0 by setting turn to 0.
The algorithm does satisfy the three essential criteria to solve the critical section problem, provided that
changes to the variables turn, flag[0], and flag[1] propagate immediately and atomically. The while condition
works even with preemption.[1]
Filter alg.: generalization to N>2 of Peterson’s alg
HW support to ME: an operation (or set of operations) is atomic, linearizable, indivisible or uninterruptible
if it appears to the rest of the system to occur instantaneously. Atomicity is a guarantee of isolation from
concurrent processes. Additionally, atomic operations commonly have a succeedorfail definition — they
either successfully change the state of the system, or have no apparent effect.
● Test_and_Set: reads a variable’s value, copies it to store the old value, modifies it with the new value
and writes the old value returning it. Maurice Herlihy (1991) proved that testandset has a finite
consensus number, in contrast to the compareandswap operation. The testandset operation can
solve the waitfree consensus problem for no more than two concurrent processes.[1]
However, more](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-3-320.jpg)
![than two decades before Herlihy's proof, IBM had already replaced Testandset by
Compareandswap, which is a more general solution to this problem. It may suffer of starvation. (from
notes: in a multiprocessor system it is not enough alone to guarantee ME, it is such that interrupts must
be disabled).
● Compare_and_Swap (CAS): an atomic instruction used in multithreading to achieve synchronization.
It compares the contents of a memory location to a given value and, only if they are the same, modifies
the contents of that memory location to a given new value. This is done as a single atomic operation. It
might suffer starvation. On servergrade multiprocessor architectures of the 2010s, compareandswap
is relatively cheap relative to a simple load that is not served from cache. A 2013 paper points out that a
CAS is only 1.15 times more expensive that a noncached load on Intel Xeon (WestmereEX) and 1.35
times on AMD Opteron (MagnyCours).[6]
As of 2013, most multiprocessor architectures support CAS in
hardware. As of 2013, the compareandswap operation is the most popular synchronization primitive
for implementing both lockbased and nonblocking concurrent data structures.[4]](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-4-320.jpg)
![● Fetch_and_Add: a special instruction that atomically modifies the contents of a memory location. It
fetches (copies) the old value of the parameter, adds to the parameter the value given by the second
parameter and returns the old value. Maurice Herlihy (1991) proved that fetchandadd has a finite
consensus number, in contrast to the compareandswap operation. The fetchandadd operation can
solve the waitfree consensus problem for no more than two concurrent processes.[1]](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-5-320.jpg)






![Deadlock with nested monitors: suppose two nested monitors, where a thread first waits on a CV and then
enters its monitor and waits on a nested CV. Now, if another thread, a second one, wants to enter the first
monitor, it might happen that: the first thread signalled on the outer CV and signal got lost, or the inner thread
still has to signal on the outer CV. In any case, the thread waiting outside will never be able to enter the
monitor because the inner thread will always be blocked on the internal CV that will never receive any signal.
So, this situation leads to a deadlock.
Deadlock with executor and monitor (Thread Starving Deadlock): suppose to have an Executor with a
thread pool whose size is N. Suppose that all the threads encounter the same CV and they all wait on it. If
there is no other thread available in the pool, then no one will be able to wake up the waiting threads, thus
resulting in a deadlock.
Waitforgraph: a directed graph used for deadlock detection in operating systems and relational database
systems.
See Coffman.
Memory barrier: a type of barrier instruction that causes a central processing unit (CPU) or compiler to
enforce an ordering constraint on memory operations issued before and after the barrier instruction; necessary
because most modern CPUs employ performance optimizations that can result in outoforder execution.
Java Memory Model (See Java Memory Model paper):
● Program order rule: actions in a thread are performed in their coding order.
● Monitor lock rule: an unlock to a monitor happensbefore any subsequent lock on the same.
● Volatile variable rule: a write to a v. variable happensbefore any subsequent read to the same var.;
the same holds for atomic var.s.
● Thread start rule: a call to Thread.start happensbefore any action in the started thread.
● Thread termination rule: any action in a thread happensbefore any other thread detects that it has
terminated, either by a successfully return from Thread.join or Thread.isAlive returning false.
● Interruption rule: a call to interrupt for a thread happensbefore the interrupted thread detects the
interrupt.
● Finalizer rule: the end of a constructor for an object happensbefore the start of its finalizer.
● Transitivity: if A happensbefore B, B happensbefore C, then A happensbefore C.
Performance
With Java, in order to perform accurate performance measurements it is important to exactly know how the
code is run by the JVM. An important component is the Just In Time (JIT) compilation engine: this module
performs dynamic compilation during the execution of a program – at run time – rather than prior to
execution.[1]
Most often this consists of translation to machine code, which is then executed directly, but can
also refer to translation to another format. It allows adaptive optimization such as dynamic recompilation – thus
in theory JIT compilation can yield faster execution than static compilation. Interpretation and JIT compilation](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-12-320.jpg)

![○ Lock coarsening: whenever the JVM observes that a thread moves from a waiting queue to
another one (because of a locks chain) always in the same sequential order, then it collapse all
the CSs into a single one, thus merging the locks into a single one. This leads to performance
improvements in terms of waiting time, so improving the throughput.
○ Lock elision: if a CS is always executed by the same thread, then it is not necessary to protect
it with a lock: so the JVM removes it.
● Lock granularity: when the shared data structure is wide, it is important to put locks only where
needed, and not on the entire data structure. For example, an hashMap could be so wide that threads
concurrently would access it on different parts, thus not violating any ME constraint. So, locking the
entire table would be penalizing the performance of our software. A solution is to have more locks to
distribute on the overall data structure. Suppose: , then number of Locks and N table size NL = =
. NL should be dimensioned so that the conflict probability is minimized.ocks distribution N % N L = L
● Nonblocking algorithms: if failure or suspension of any thread cannot cause failure or suspension of
another thread[1]
(use of volatile and atomic variables).
○ Waitfree: the strongest nonblocking guarantee of progress, combining guaranteed
systemwide throughput with starvationfreedom. An algorithm is waitfree if every operation has
a bound on the number of steps the algorithm will take before the operation completes.[11]
○ Lockfree: allows individual threads to starve but guarantees systemwide throughput. An
algorithm is lockfree if it satisfies that when the program threads are run sufficiently long at
least one of the threads makes progress (for some sensible definition of progress). All waitfree
algorithms are lockfree. An algorithm is lock free if every operation has a bound on the number
of steps before one of the threads operating on a data structure completes its operation.[11]
○ Obstructionfree: the weakest natural nonblocking progress guarantee. An algorithm is
obstructionfree if at any point, a single thread executed in isolation (i.e., with all obstructing
threads suspended) for a bounded number of steps will complete its operation.[11]
All lockfree
algorithms are obstructionfree.
See Treiber's stack and Michael and Scott's queue. These two algorithms are a nonblocking implementation
of a stack and a queue respectively. Both are based on the use of AtomicReference variables, that make it
possible to deal with threads synchronization. They result with better performance when used in such
programs that suffer from high contention rates. Basically, they implement a spinning solution to deal with
concurrent modification on the stack pointer and the head and tail references in the queue. Thus, whenever a
thread tries to modify one of them has to be sure (see the if statements) that it is actually modifying what it is
expecting to modify (note the use of compareAndSet). If such a check fails, then go back (spin) and try again
from the beginning.
JAVA: Nested Classes (oracle reference)
A nested class is a member of its enclosing class. Nonstatic nested classes (inner classes) have access to
other members of the enclosing class, even if they are declared private. Static nested classes do not have
access to other members of the enclosing class. As a member of the OuterClass, a nested class can be
declared private, public, protected, or package private. (Recall that outer classes can only be declared public
or package private.)](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-14-320.jpg)





![TIME AND GLOBAL STATES
Clocks, events and process states
We define an event to be the occurrence of a single action that a process carries out as it executes – a
communication action or a statetransforming action. The sequence of events within a single process pi can be
placed in a single, total ordering, which we denote by the relation ➝i between the events. That is, e ➝i e' if and
only if the event e occurs before e’ at pi. This ordering is well defined, whether or not the process is
multithreaded, since we have assumed that the process executes on a single processor. Now we can define
the history of process pi to be the series of events that take place within it, ordered as we have described by
the relation ➝i:
history(pi) hi = < ei
0
ei1
e2
… >
The operating system reads the node’s hardware clock value, Hi(t) , scales it and adds an offset so as to
produce a software clock Ci(t) = α Hi(t) + β that approximately measures real, physical time t for process pi . In
other words, when the real time in an absolute frame of reference is t, Ci(t) is the reading on the software clock.
Successive events will correspond to different timestamps only if the clock resolution – the period between
updates of the clock value – is smaller than the time interval between successive events.
SKEW between computer clocks in a distributed system Network: The instantaneous difference between the
readings of any two clocks is called their skew.
Clock DRIFT: which means that they count time at different rates, and so diverge.
Clock's DRIFT RATE: change in the offset between the clock and a nominal perfect reference clock per unit of
time measured by the reference clock.
UTC (Coordinated Universal Time): is based on atomic time, but a socalled ‘leap second’ is inserted – or,
more rarely, deleted – occasionally to keep it in step with astronomical time. UTC signals are synchronized and
broadcast regularly from landbased radio stations and satellites covering many parts of the world.
Synchronizing Physical Clocks
Synchronization in a synchronous system: In general, for a synchronous system, the optimum bound that
can be achieved on clock skew when synchronizing N clocks is u * (1 – 1 / N) [Lundelius and Lynch 1984], u =
max min, the max and min time that a transmission of a message can observe in a synchronous system.
Cristian’s method for synchronizing clocks: use of a time server, connected to a device that receives
signals from a source of UTC, to synchronize computers externally. There is no upper bound on message
transmission delays in an asynchronous system, the roundtrip times for messages exchanged between pairs
of processes are often reasonably short – a small fraction of a second. He describes the algorithm as
probabilistic: the method achieves synchronization only if the observed roundtrip times between client and
server are sufficiently short compared with the required accuracy. A simple estimate of the time to which p](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-20-320.jpg)
![should set its clock is t + Tround / 2 , which assumes that the elapsed time is split equally before and after S
placed t in mt(=message for timestamp sinc.). This is normally a reasonably accurate assumption, unless the
two messages are transmitted over different networks.
Discussion: Cristian’s method suffers from the problem associated with all services implemented by a single
server: that the single time server might fail and thus render synchronization temporarily impossible. Cristian
suggested, for this reason, that time should be provided by a group of synchronized time servers, each with a
receiver for UTC time signals. Dolev et al. [1986] showed that if f is the number of faulty clocks out of a total of
N, then we must have N = 3f if the other, correct, clocks are still to be able to achieve agreement.
Berkeley's Algorithm: an algorithm for internal synchronization developed for collections of computers
running Berkeley UNIX. A coordinator computer is chosen to act as the master. Unlike in Cristian’s protocol,
this computer periodically polls the other computers whose clocks are to be synchronized, called slaves. The
slaves send back their clock values to it. The master estimates their local clock times by observing the
roundtrip times (similarly to Cristian’s technique), and it averages the values obtained (including its own
clock’s reading). The balance of probabilities is that this average cancels out the individual clocks’ tendencies
to run fast or slow. The accuracy of the protocol depends upon a nominal maximum roundtrip time between
the master and the slaves.
The master takes a FAULTTOLERANT AVERAGE. That is, a subset is chosen of clocks that do not differ
from one another by more than a specified amount, and the average is taken of readings from only these
clocks.
NTP: Cristian’s method and the Berkeley algorithm are intended primarily for use within
intranets. NTP’s chief design aims and features are as follows:
● To provide a service enabling clients across the Internet to be synchronized accurately to UTC:
Although large and variable message delays are encountered in Internet communication, NTP employs
statistical techniques for the filtering of timing data and it discriminates between the quality of timing
data from different servers.
● To provide a reliable service that can survive lengthy losses of connectivity: There are redundant
servers and redundant paths between the servers. The servers can reconfigure so as to continue to
provide the service if one of them becomes unreachable.
● To enable clients to resynchronize sufficiently frequently to offset the rates of drift found in most
computers: The service is designed to scale to large numbers of clients and servers.
● To provide protection against interference with the time service, whether malicious or accidental: The
time service uses authentication techniques to check that timing data originate from the claimed trusted
sources. It also validates the return addresses of messages sent to it.
Logical Time and Logical Clocks
As Lamport [1978] pointed out, since we cannot synchronize clocks perfectly across a distributed system, we
cannot in general use physical time to find out the order of any arbitrary pair of events occurring within it. Two
simple and intuitively obvious points:](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-21-320.jpg)
![● If two events occurred at the same process pi (i = 1, 2,...N), then they occurred in the order in which pi
observes them – this is the order ➝i that we defined above.
● Whenever a message is sent between processes, the event of sending the message occurred before
the event of receiving the message.
Lamport called the partial ordering obtained by generalizing these two relationships the happenedbefore
relation. It is also sometimes known as the relation of causal ordering or potential causal ordering.
The sequence of events need not be unique.
For example, a ↛e and e ↛a, since they occur at different processes, and there is no chain of messages
intervening between them. We say that events such as a and e that are not ordered by ➝ are concurrent and
write this a || e .
Logical clocks: Lamport [1978] invented a simple mechanism by which the happenedbefore ordering can be
captured numerically, called a logical clock. A Lamport logical clock is a monotonically increasing software
counter, whose value need bear no particular relationship to any physical clock. Each process pi keeps its own
logical clock, Li , which it uses to apply socalled Lamport timestamps to events. We denote the timestamp of
event e at pi by Li(e) , and by L(e) we denote the timestamp of event e at whatever process it occurred at.
To capture the happenedbefore relation ➝, processes update their logical clocks and transmit the values of
their logical clocks in messages as follows:
● LC1: Li is incremented before each event is issued at process pi : Li := Li + 1.
● LC2:
(a) When a process pi sends a message m, it piggybacks on m the value t = Li.
(b) On receiving (m, t), a process pj computes Lj := max(Lj ,t) and then applies LC1 before timestamping
the event receive(m).](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-22-320.jpg)
![Note: e➝ e’ ⇒ L(e) < L(e’) .
The converse is not true. If L(e) < L(e’) , then we cannot infer that e ➝ e’.
Totally ordered logical clocks: Some pairs of distinct events, generated by different processes, have
numerically identical Lamport timestamps. We can create a total order on the set of events – that is, one for
which all pairs of distinct events are ordered – by taking into account the identifiers of the processes at which
events occur.
We define the global logical timestamps for these events to be (Ti, i) and (Tj, j) , respectively. (Ti, i) < (Tj, j) if
and only if either Ti < Tj , or Ti = Tj and i < j .
Vector clocks: Mattern [1989] and Fidge [1991] developed vector clocks to overcome the shortcoming of
Lamport’s clocks: the fact that from L(e) < L(e’) we cannot conclude that e ➝ e’.
A vector clock for a system of N processes is an array of N integers. Each process keeps its own vector clock,
Vi , which it uses to timestamp local events. There are simple rules for updating the clocks:
For a vector clock Vi, Vi(i) is the number of events that pi has timestamped, and Vi(j) (j ≠ i) is the number of
events that have occurred at pj that have potentially affected pi. (Process pj may have timestamped more
events by this point, but no information has flowed to pi about them in messages as yet.)](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-23-320.jpg)


![● asymmetrical direct naming: the receiver can receive messages from any process.
Indirect comm. (indirect naming): uses intermediaries called channels or mailboxes
● symmetrical indirect naming: both the sender and receiver name the corresponding channel.
● asymmetrical indirect naming: the receiver can receive messages from any channel.
Request/Reply protocol: a requestor sends a request message to a replier system which receives and
processes the request, ultimately returning a message in response. This is a simple, but powerful messaging
pattern which allows two applications to have a twoway conversation with one another over a channel. This
pattern is especially common in clientserver architectures.[1]
For simplicity, this pattern is typically implemented in a purely synchronous fashion, as in web service calls
over HTTP, which holds a connection open and waits until the response is delivered or the timeout period
expires. However, request–response may also be implemented asynchronously, with a response being
returned at some unknown later time. This is often referred to as "sync over async", or "sync/async", and is
common in enterprise application integration (EAI) implementations where slow aggregations, timeintensive
functions, or human workflow must be performed before a response can be constructed and delivered.
Marshalling and Unmarshalling: The information stored in running programs is represented as data
structures, whereas the information in messages consists of sequences of bytes. Irrespective of the form of
communication used, the data structures must be flattened (converted to a sequence of bytes) before](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-27-320.jpg)

![by concatenating the Internet address of its host computer and the port number of the process that created it
with the time of its creation and a local object number. The local object number is incremented each time an
object is created in that process.
The last field of the remote object reference shown in Figure 4.13 contains some information about the
interface of the remote object, for example, the interface name. This information is relevant to any process that
receives a remote object reference as an argument or as the result of a remote invocation, because it needs to
know about the methods offered by the remote object.
Idempotent op.s: an operation that will produce the same results if executed once or multiple times.[7]
In the
case of methods or subroutine calls with side effects, for instance, it means that the modified state remains the
same after the first call. In functional programming, though, an idempotent function is one that has the property
f(f(x)) = f(x) for any value x.[8]
This is a very useful property in many situations, as it means that an operation can be repeated or retried as
often as necessary without causing unintended effects. With nonidempotent operations, the algorithm may
have to keep track of whether the operation was already performed or not.
In the HyperText Transfer Protocol (HTTP), idempotence and safety are the major attributes that separate
HTTP verbs. Of the major HTTP verbs, GET, PUT, and DELETE are idempotent (if implemented according to
the standard), but POST is not.[9]
Remote Procedure Call (RPC)
Requestreply protocols provide relatively lowlevel support for requesting the execution of a remote operation,
and also provide direct support for RPC and RMI.
RPC allows client programs to call procedures transparently in server programs running in separate processes
and generally in different computers from the client.
RPC has the goal of making the programming of distributed systems look similar, if not identical, to
conventional programming – that is, achieving a high level of distribution transparency. This unification is
achieved in a very simple manner, by extending the abstraction of a procedure call to distributed environments.
In particular, in RPC, procedures on remote machines can be called as if they are procedures in the local
address space. The underlying RPC system then hides important aspects of distribution, including the
encoding and decoding of parameters and results, the passing of messages and the preserving of the required
semantics for the procedure call.
Three issues that are important in understanding this concept:
● programming with interfaces (the style of programming): in order to control the possible interactions
between modules, an explicit interface is defined for each module; as long as its interface remains the
same, the implementation may be changed without affecting the users of the module.](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-29-320.jpg)









![In order to enter the CS, a process must hold the token granting the access. The token keeps moving around
the ring until a process requires it. Then it holds until completes and exits the CS. At this point, the token is
released and passed again to the next process.
Pro: easy to implement, easy to adapt to N CSs, to exit the CS a process observes no delay.
Cons: continuous bandwidth consumption, to enter the CS a process might experience from 0 to N messages
delay, synchronization delay goes from 1 to N messages.
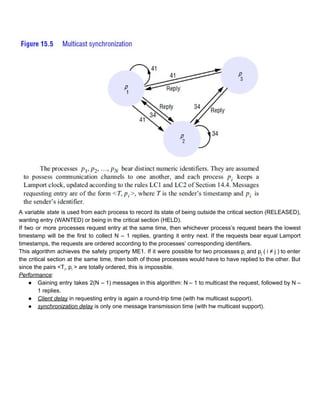
RICARTAGRAWALA (Multicast and logical blocks, [1981]): mutual exclusion between N peer processes
based upon multicast. Processes that require entry to a critical section multicast a request message, and can
enter it only when all the other processes have replied to this message.](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-40-320.jpg)

![Elections
An algorithm for choosing a unique process to play a particular role is called an election algorithm. It is
essential that all the processes agree on the choice.
At any point in time, a process pi is either a participant – meaning that it is engaged in some run of the election
algorithm – or a nonparticipant – meaning that it is not currently engaged in any election. Our requirements
are that, during any particular run of the algorithm:
E1: (safety) A participant process pi has electedi = 丄 or electedi = P, where P is chosen as the
noncrashed process at the end of the run with the largest identifier.
E2: (liveness) All processes pi participate and eventually either set electedi ≠丄 – or crash.
The algorithm of Chang and Roberts [1979] (A ringbased election algorithm): suitable for a collection of
processes arranged in a logical ring. Each process pi has a communication channel to the next process in the
ring, p(i + 1)mod N , and all messages are sent clockwise around the ring. We assume that no failures occur, and
that the system is asynchronous. The goal of this algorithm is to elect a single process called the coordinator,
which is the process with the largest identifier. Initially, every process is marked as a nonparticipant in an
election. Any process can begin an election. It proceeds by marking itself as a participant, placing its identifier
in an election message and sending it to its clockwise neighbour. When a process receives an election
message, it compares the identifier in the message with its own. If the arrived identifier is greater, then it](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-43-320.jpg)


![fail only by crashing. The processes are members of groups, which are the destinations of messages sent with
the multicast operation.
The operation multicast(g, m) sends the message m to all members of the group g of processes.
Correspondingly, there is an operation deliver(m) that delivers a message sent by multicast to the calling
process. We use the term deliver rather than receive to make clear that a multicast message is not always
handed to the application layer inside the process as soon as it is received at the process’s node.
Every message m carries the unique identifier of the process sender(m) that sent it, and the unique destination
group identifier group(m). We assume that processes do not lie about the origin or destinations of messages.
BASIC MULTICAST: a basic multicast primitive that guarantees, unlike IP multicast, that a correct process will
eventually deliver the message, as long as the multicaster does not crash. We call the primitive Bmulticast
and its corresponding basic delivery primitive Bdeliver. We allow processes to belong to several groups, and
each
message is destined for some particular group. A straightforward way to implement Bmulticast is to use a
reliable onetoone send operation.
RELIABLE MULTICAST: a reliable multicast with corresponding operations Rmulticast and Rdeliver.
Properties analogous to integrity and validity are clearly highly desirable in reliable multicast delivery, but we
add another: a requirement that all correct processes in the group must receive a message if any of them
does.
A reliable multicast is one that satisfies the following properties:
● Integrity: A correct process p delivers a message m at most once. Furthermore, p ∈ group(m) and m
was supplied to a multicast operation by sender(m). (As with onetoone communication, messages can
always be distinguished by a sequence number relative to their sender.)
● Validity: If a correct process multicasts message m, then it will eventually deliver m.
● Agreement: If a correct process delivers message m, then all other correct processes in group(m) will
eventually deliver m.
Performance:
● Message complexity O(g2
)
● Round complexity O(2) = O(1)
CONSENSUS: the problem is for processes to agree on a value after one or more of the processes has
proposed what that value should be. In mutual exclusion, the processes agree on which process can enter the
critical section. In an election, the processes agree on which is the elected process. In totally ordered multicast,
the processes agree on the order of message delivery. Three related agreement problems exist: Byzantine
generals, interactive consistency and totally ordered multicast. We go on to examine under what
circumstances the problems can be solved, and to sketch some solutions. In particular, we discuss the
wellknown impossibility result of Fischer et al. [1985], which states that in an asynchronous system a
collection of processes containing only one faulty process cannot be guaranteed to reach consensus.
Our system model includes a collection of processes pi ( i = 1, 2, …, N ) communicating by message passing.
An important requirement that applies in many practical situations is for consensus to be reached even in the
presence of faults. We assume, as before, that communication is reliable but that processes may fail. In this](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-46-320.jpg)

![property of a reliable multicast. Every process receives the same set of proposed values, and every process
evaluates the same function of those values. So they must all agree, and if every process proposed the same
value, then they all decide on this value.
If processes can fail in arbitrary (Byzantine) ways, then faulty processes can in principle communicate random
values to the others. This may seem unlikely in practice, but it is not beyond the bounds of possibility for a
process with a bug to fail in this way. Moreover, the fault may not be accidental, but the result of mischievous
or malevolent operation. Someone could deliberately make a process send different values to different peers in
an attempt to thwart the others, which are trying to reach consensus. In case of inconsistency, correct
processes must compare what they have received with what other processes claim to have received.
The Byzantine generals problem: In the informal statement of the Byzantine generals problem [Lamport et al.
1982], three or more generals are to agree to attack or to retreat. One, the commander, issues the order. The
others, lieutenants to the commander, must decide whether to attack or retreat. But one or more of the
generals may be ‘treacherous’ – that is, faulty. If the commander is treacherous, he proposes attacking to one
general and retreating to another. If a lieutenant is treacherous, he tells one of his peers that the commander
told him to attack and another that they are to retreat. The Byzantine generals problem differs from consensus
in that a distinguished process supplies a value that the others are to agree upon, instead of each of them
proposing a value. The requirements are:
● Termination: Eventually each correct process sets its decision variable.
● Agreement: The decision value of all correct processes is the same: if pi and pj are correct and have
entered the decided state, then di = dj ( i, j = 1, 2, … , N ).
● Integrity: If the commander is correct, then all correct processes decide on the value that the
commander proposed.
Note that, for the Byzantine generals problem, integrity implies agreement when the commander is correct; but
the commander need not be correct.
Consensus in a synchronous system: here is described an algorithm to solve consensus in a synchronous
system, although it is based on a modified form of the integrity requirement. The algorithm uses only a basic
multicast protocol. It assumes that up to f of the N processes exhibit crash failures.
To reach consensus, each correct process collects proposed values from the other processes. The algorithm
proceeds in f + 1 rounds, in each of which the correct processes Bmulticast the values between themselves.
Their modified form of the integrity requirement applies to the proposed values of all processes, not just the
correct ones: if all processes, whether correct or not, proposed the same value, then any correct process in the
decided state would chose that value. Given that the algorithm assumes crash failures at worst, the proposed
values of correct and noncorrect processes would not be expected to differ, at least not on the basis of
failures. The revised form of integrity enables the convenient use of the minimum function to choose a decision
value from those proposed.
After f + 1 rounds, each process chooses the minimum value it has received as its decision value. To check the
correctness of the algorithm, we must show that each process arrives at the same set of values at the end of
the final round.
Assume, to the contrary, that two processes differ in their final set of values. Without loss of generality, some
correct process pi possesses a value v that another correct process pj ( i ≠ j ) does not possess. The only
explanation for pi possessing a proposed value v at the end that pj does not possess is that any third process,](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-48-320.jpg)
![pk , say, that managed to send v to pi crashed before v could be delivered to pj. In turn, any process sending v
in the previous round must have crashed, to explain why pk possesses v in that round but pj did not receive it.
Proceeding in this way, we have to posit at least one crash in each of the preceding rounds. But we have
assumed that at most f crashes can occur, and there are f + 1 rounds. We have arrived at a contradiction.
It turns out that any algorithm to reach consensus despite up to f crash failures requires at least f + 1
rounds of message exchanges, no matter how it is constructed [Dolev and Strong 1983]. This lower
bound also applies in the case of Byzantine failures [Fischer and Lynch 1982].
The Byzantine generals problem in a synchronous system: here we assume that processes can exhibit
arbitrary failures. That is, a faulty process may send any message with any value at any time; and it may omit
to send any message. Up to f of the N processes may be faulty. Correct processes can detect the absence of a
message through a timeout; but they cannot conclude that the sender has crashed, since it may be silent for
some time and then send messages again.
We assume that the communication channels between pairs of processes are private. Our default assumption
of channel reliability means that no faulty process can inject messages into the communication channel
between correct processes.
Lamport et al. [1982] considered the case of three processes that send unsigned messages to one another.
They showed that there is no solution that guarantees to meet the conditions of the Byzantine generals
problem if one process is allowed to fail. They generalized this result to show that no solution exists if N ≤ 3f.
They went on to give an algorithm that solves the Byzantine generals problem in a synchronous system if N ≥
3f + 1 , for unsigned (they call them ‘oral’) messages.](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-49-320.jpg)


![Impossibility in asynchronous systems: The algorithms seen so far assume that message exchanges take
place in rounds, and that processes are entitled to time out and assume that a faulty process has not sent
them a message within the round, because the maximum delay has been exceeded.
Fischer et al. [1985] proved that no algorithm can guarantee to reach consensus in an asynchronous system,
even with one process crash failure (FLP restriction). In an asynchronous system, processes can respond to
messages at arbitrary times, so a crashed process is indistinguishable from a slow one. Their proof involves
showing that there is always some continuation of the processes’ execution that avoids consensus being
reached. Note the word ‘guarantee’ in the statement of the impossibility result. The result does not mean that
processes can never reach distributed consensus in an asynchronous system if one is faulty. It allows that
consensus can be reached with some probability greater than zero, confirming what we know in practice.
Three techniques exist for working around the impossibility result:
● fault masking: avoid the impossibility result altogether by masking any process failures that occur; if a
process crashes, then it is restarted. The process places sufficient information in persistent storage at
critical points in its program so that if it should crash and be restarted, it will find sufficient data to be
able to continue correctly with its interrupted task. In other words, it will behave like a process that is
correct, but that sometimes takes a long time to perform a processing step.
● failure detectors: processes can agree to deem a process that has not responded for more than a
bounded time to have failed. An unresponsive process may not really have failed, but the remaining
processes act as if it had done. They make the failure ‘failsilent’ by discarding any subsequent
messages that they do in fact receive from a ‘failed’ process. In other words, we have effectively turned
an asynchronous system into a synchronous one. This technique is used in the ISIS system [Birman
1993].
● randomizing aspects of the processes’ behaviour: The result of Fischer et al. [1985] depends on
what we can consider to be an ‘adversary’. This is a ‘character’ (actually, just a collection of random
events) who can exploit the phenomena of asynchronous systems so as to foil the processes’ attempts
to reach consensus. The adversary manipulates the network to delay messages so that they arrive at
just the wrong time, and similarly it slows down or speeds up the processes just enough so that they
are in the ‘wrong’ state when they receive a message. This technique that addresses the impossibility
result is to introduce an element of chance in the processes’ behaviour, so that the adversary cannot
exercise its thwarting strategy effectively. Consensus might still not be reached in some cases, but this
method enables processes to reach consensus in a finite expected time.
Technologies for Cloud Computing (Lettieri)
HW assisted Virtualization
Popek and Goldberg’s 1974 paper establishes three essential characteristics for system software to be
considered a VMM:
1. Fidelity. Software on the VMM executes identically to its execution on hardware, barring timing effects.
2. Performance. An overwhelming majority of guest instructions are executed by the hardware without
the intervention of the VMM.](https://image.slidesharecdn.com/review-concurrentanddistributedsystems-150728205427-lva1-app6892/85/Notes-about-concurrent-and-distributed-systems-x86-virtualization-52-320.jpg)


