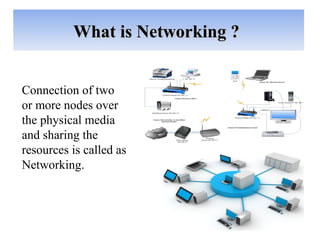
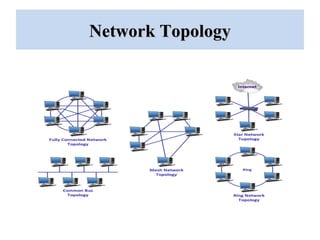
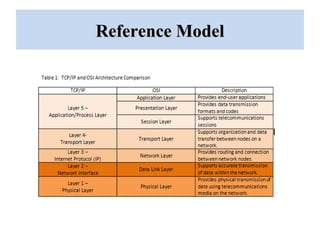
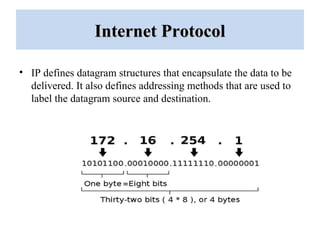
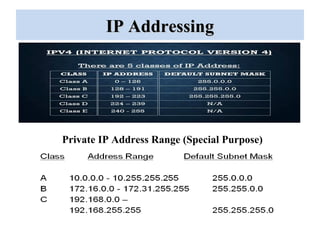
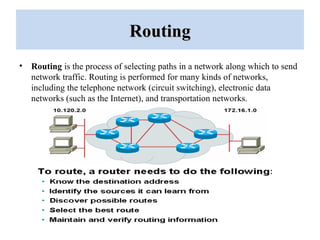
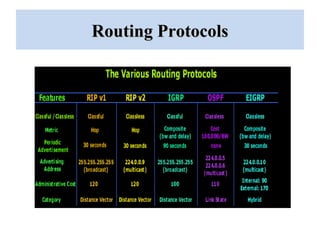
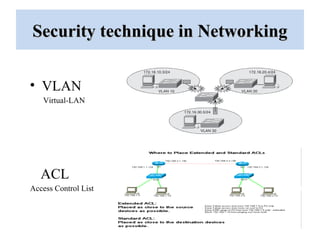
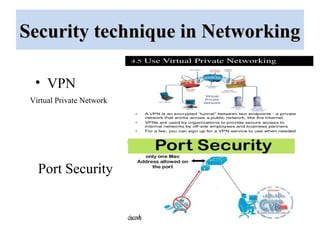
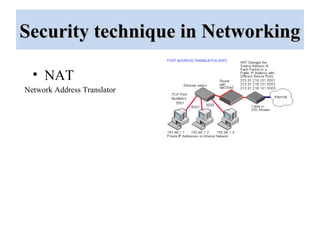
The document outlines a project on 'network security policy for campus' conducted at Bhai Gurdas Institute of Engineering and Technology, detailing components and networking techniques used. It describes the project's aim to understand campus networking and its implementation, including various networking devices and protocols. Additionally, it highlights future prospects for advancements in networking technology.