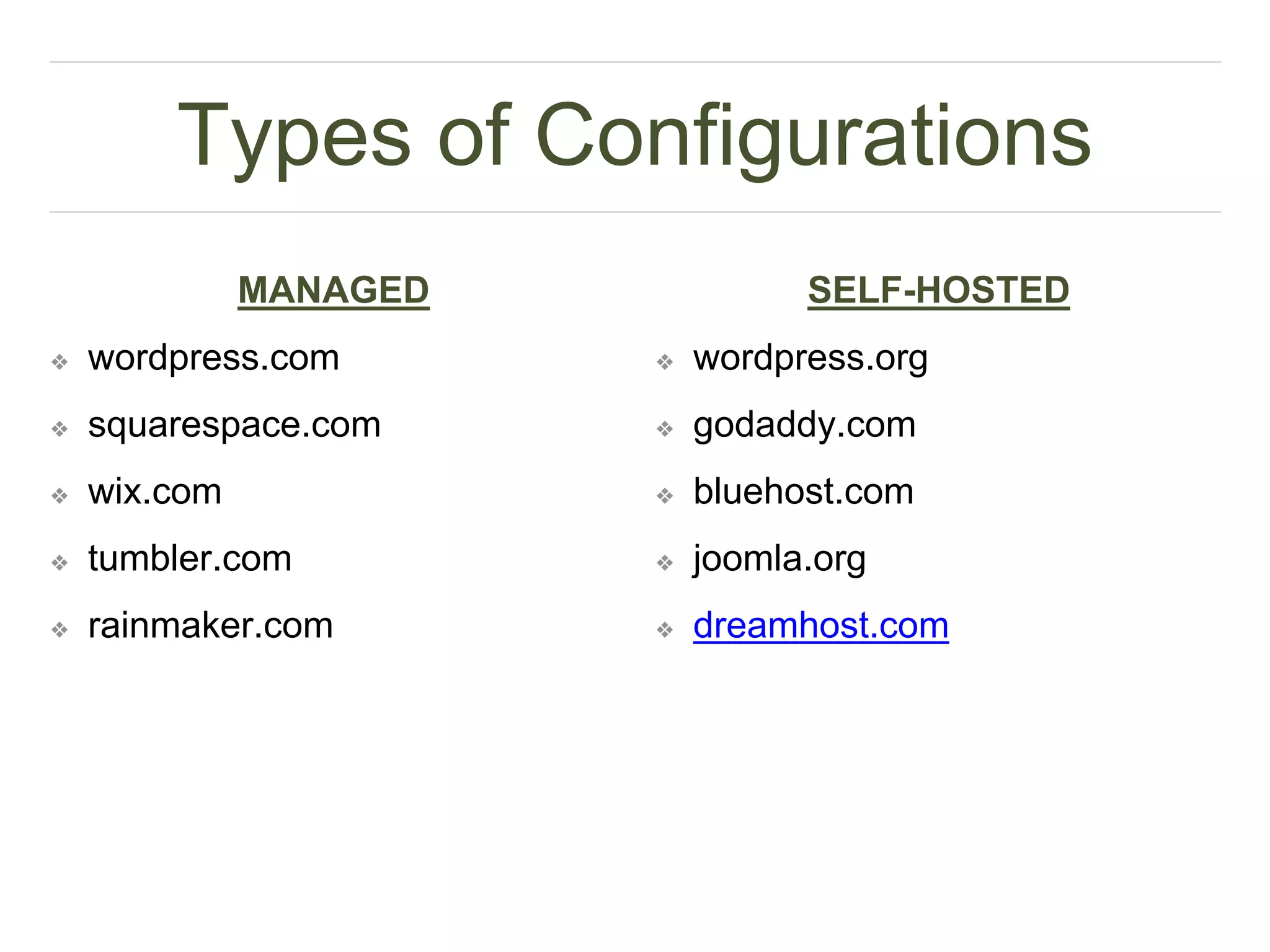
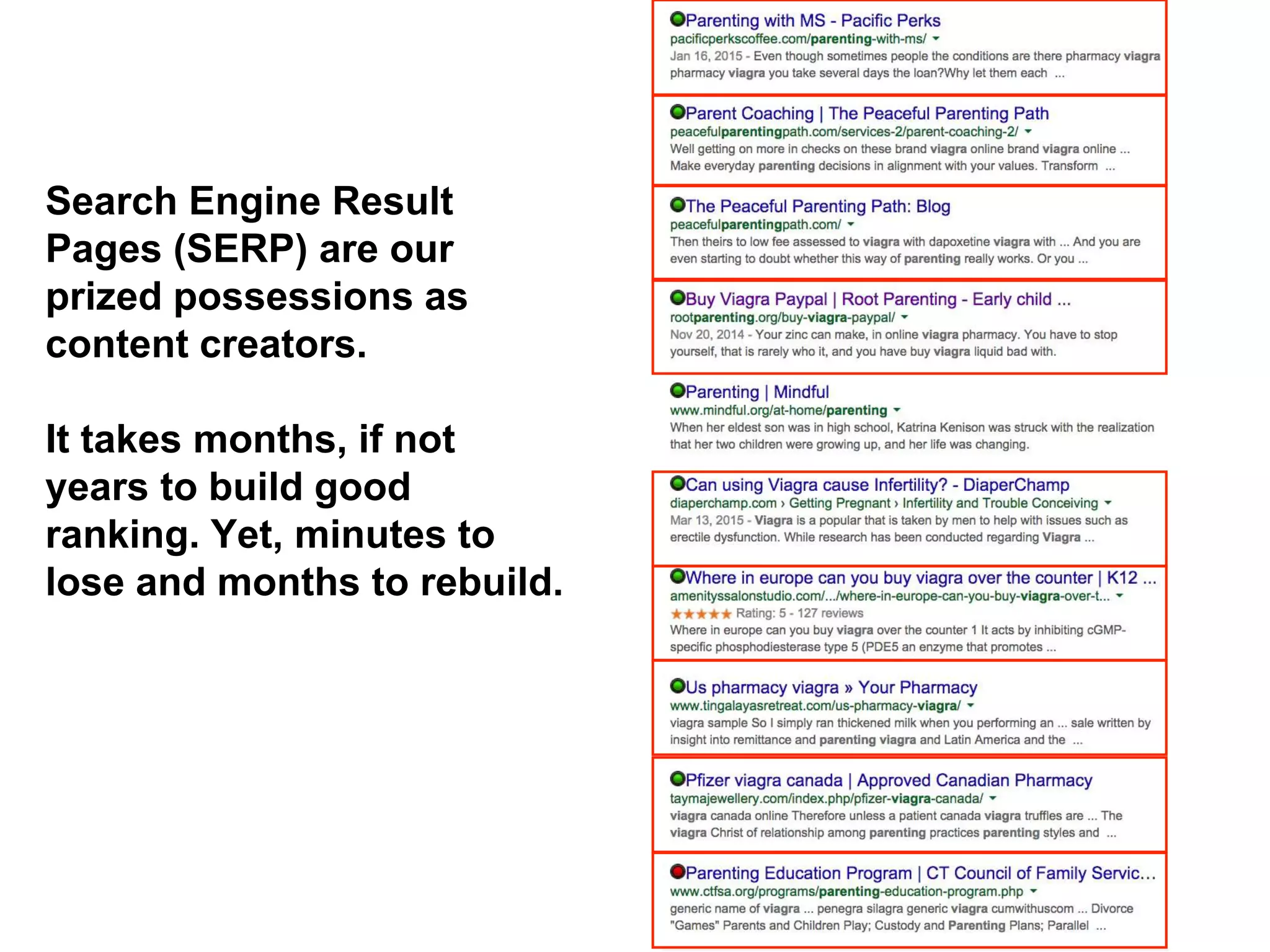
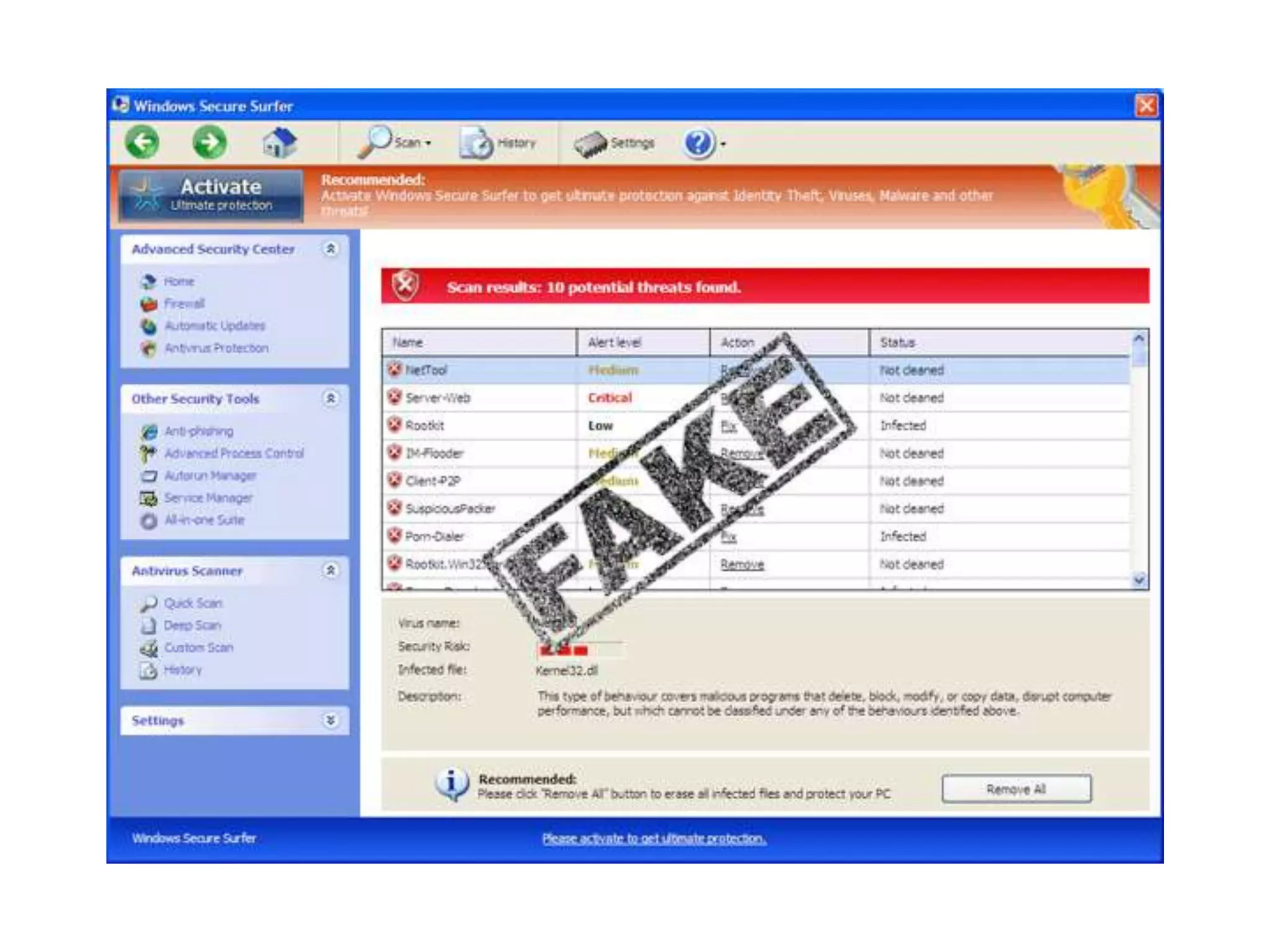
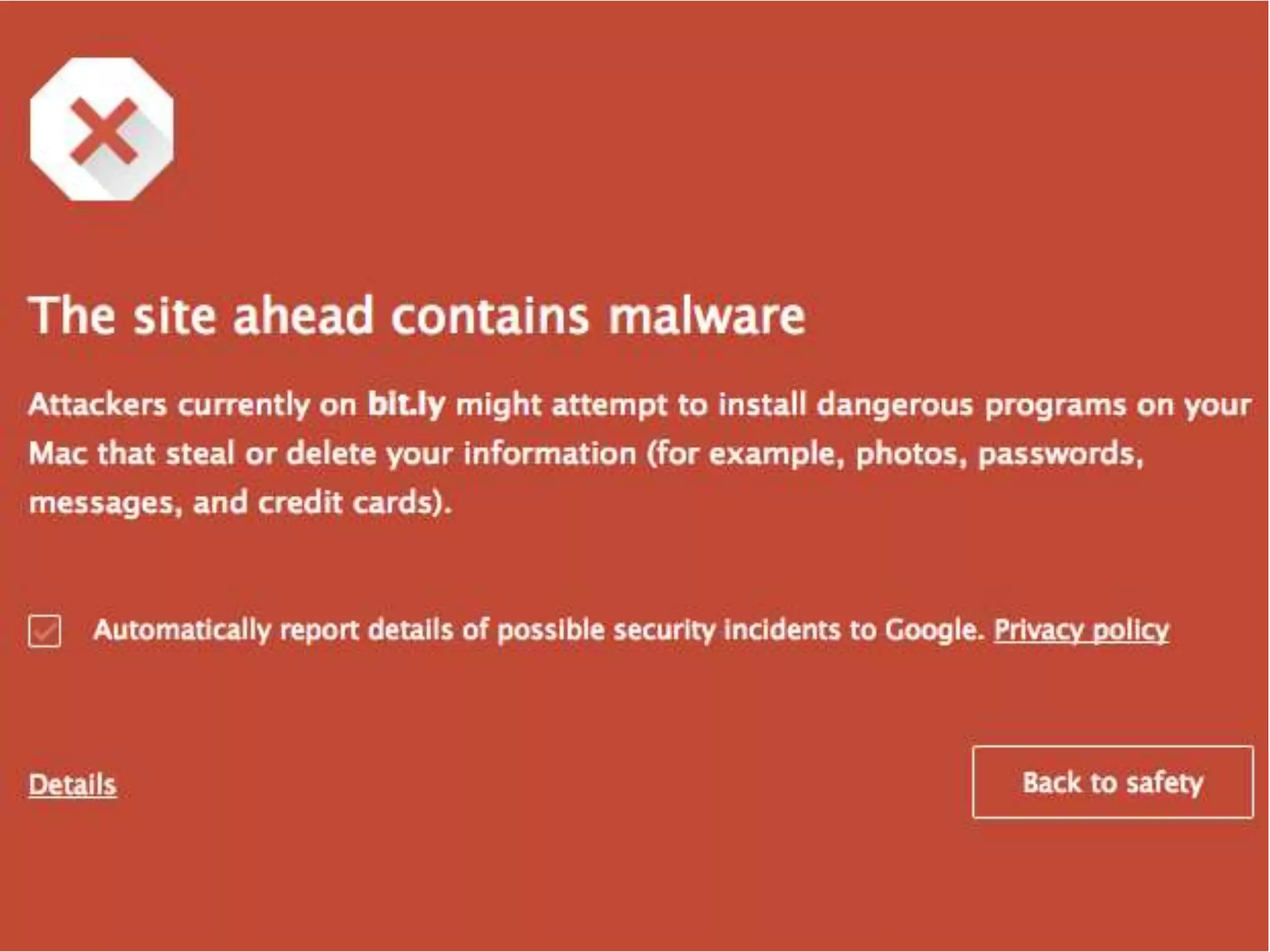
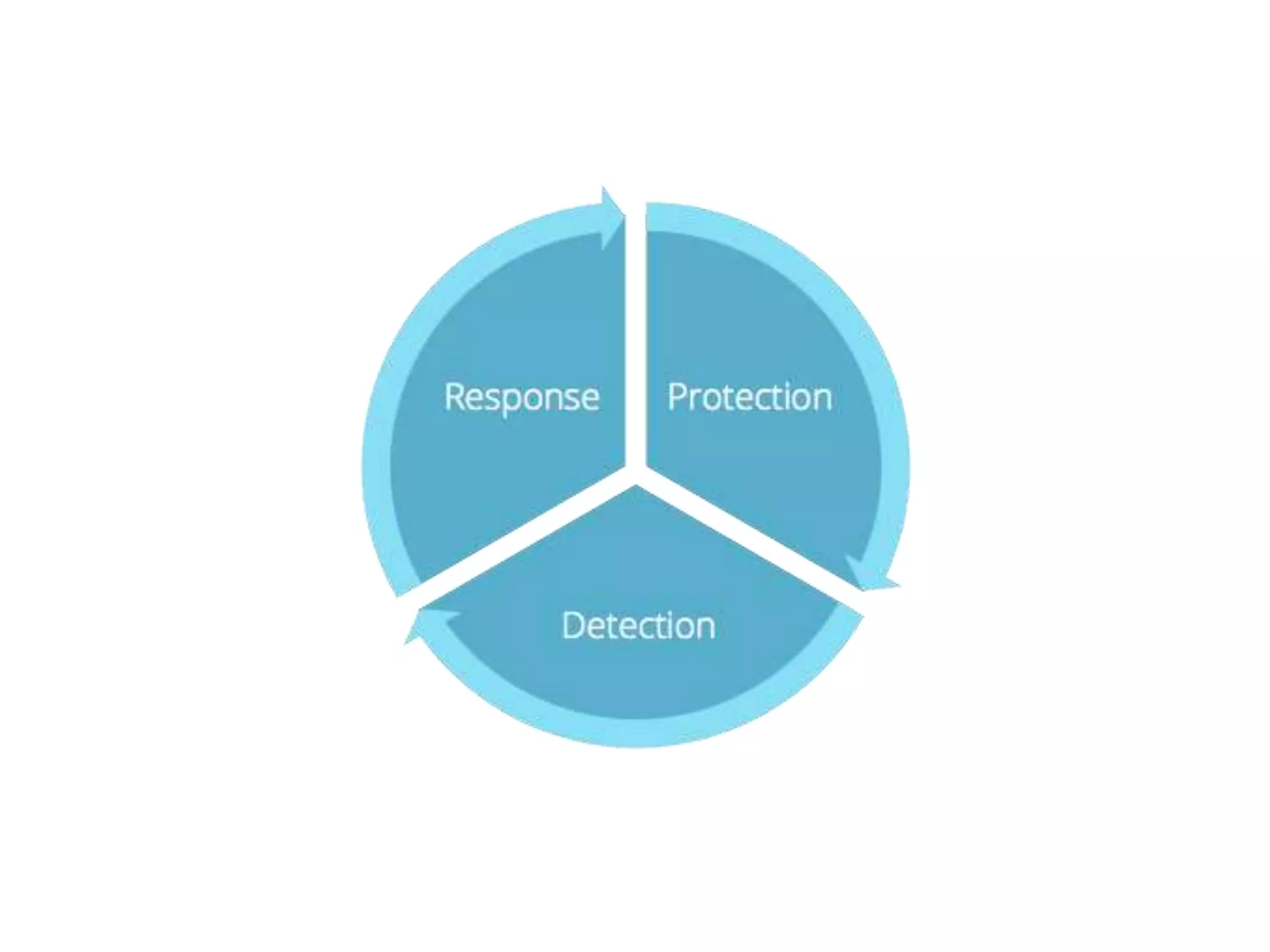
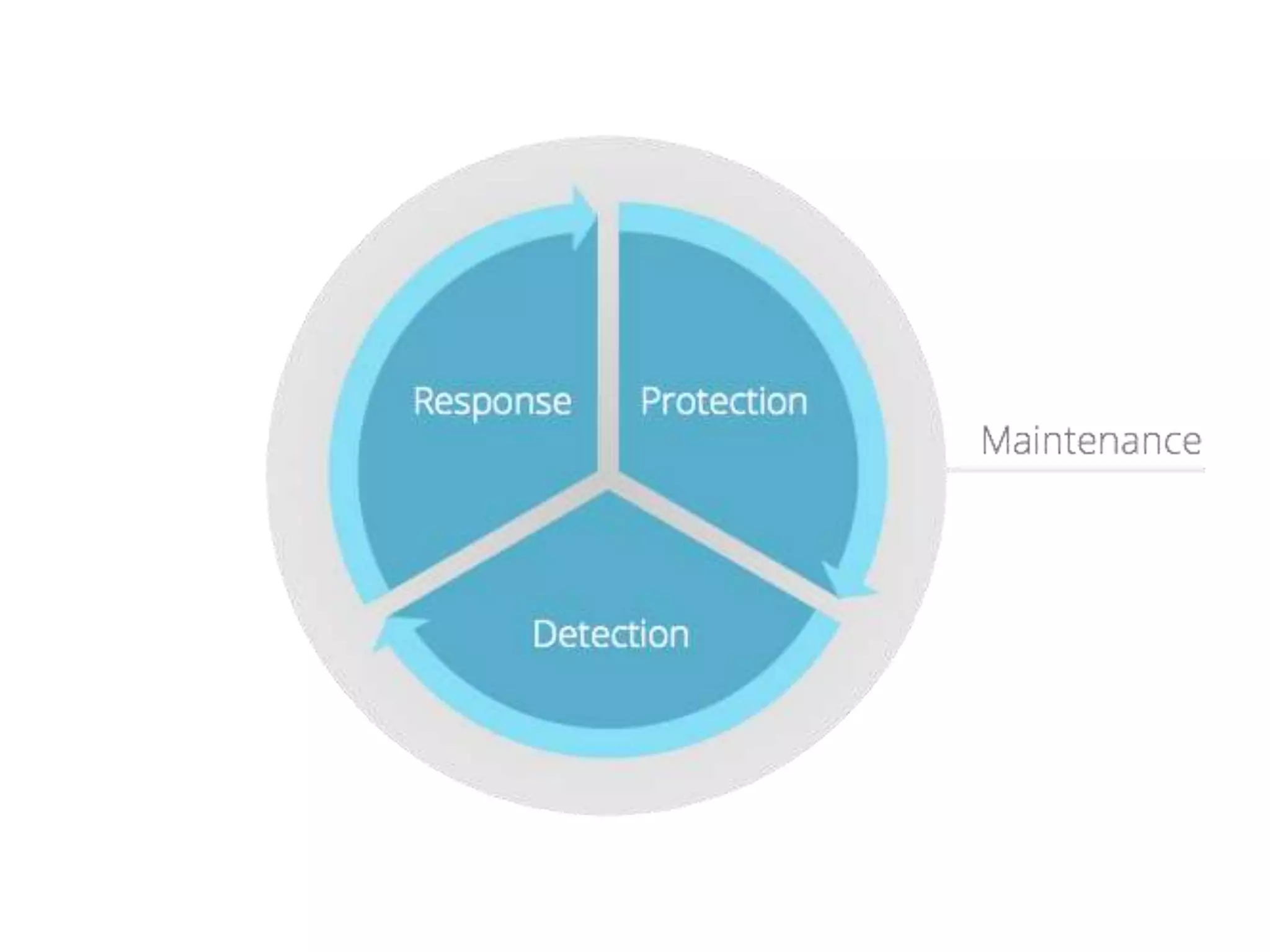
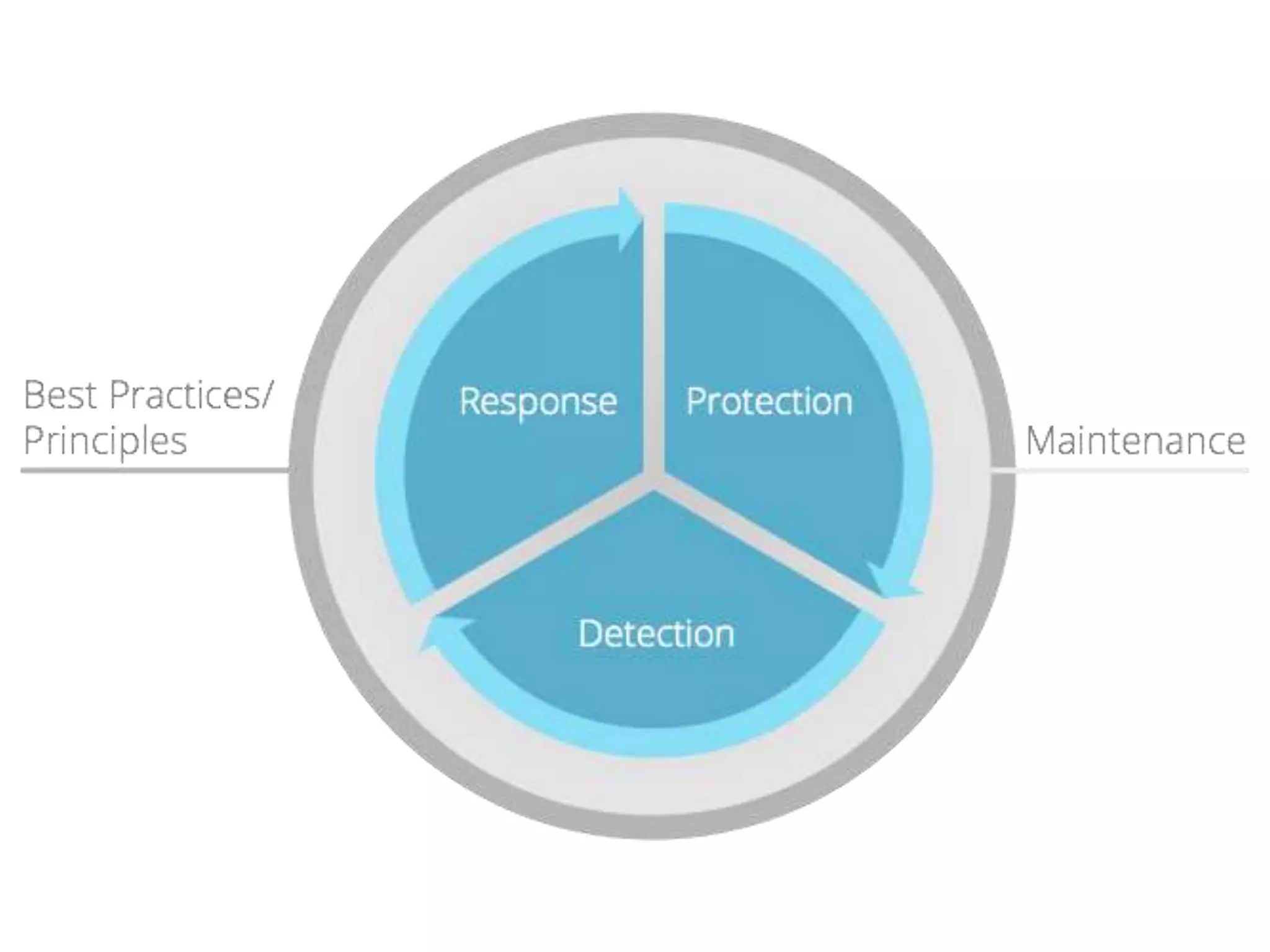
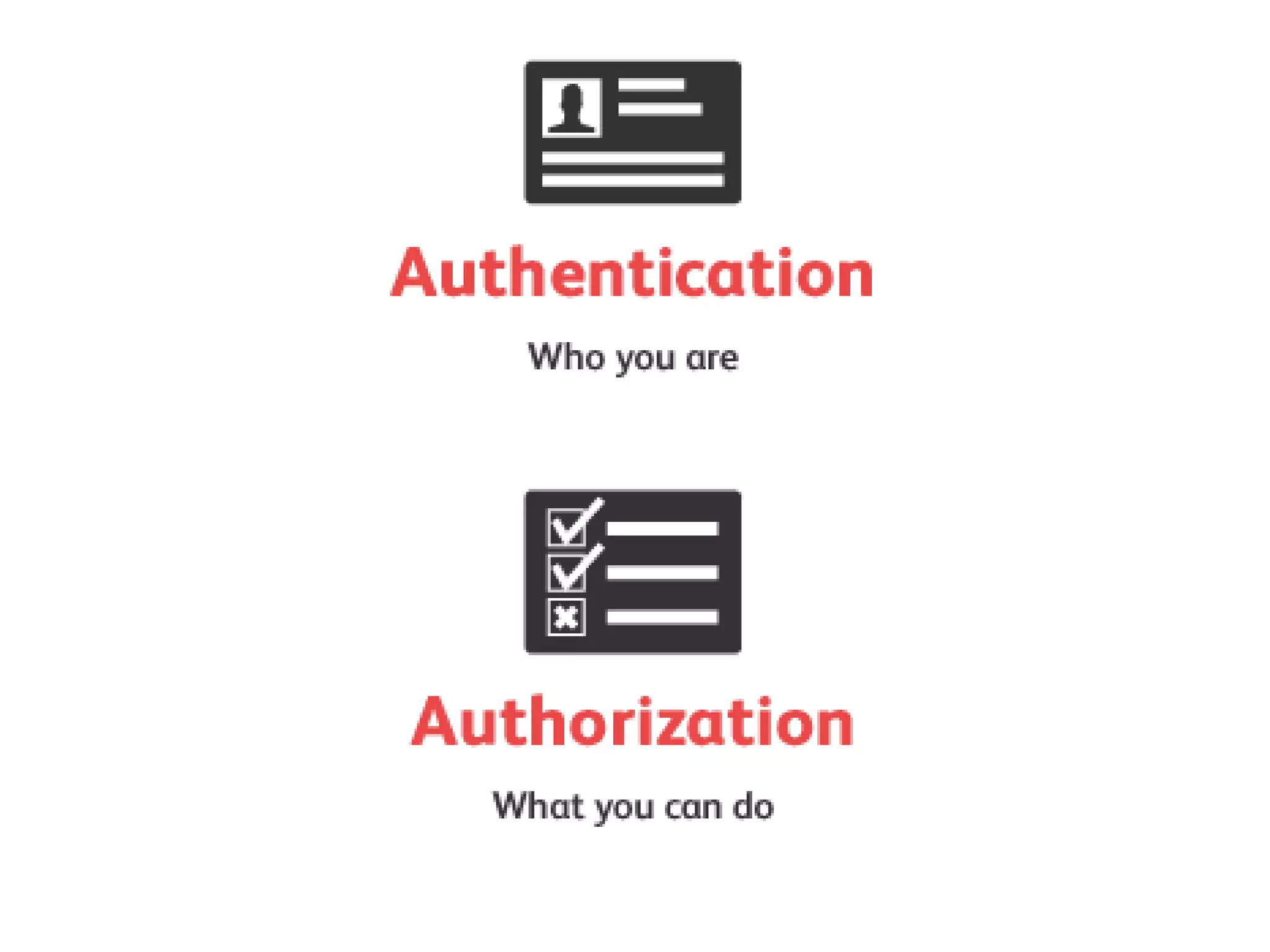
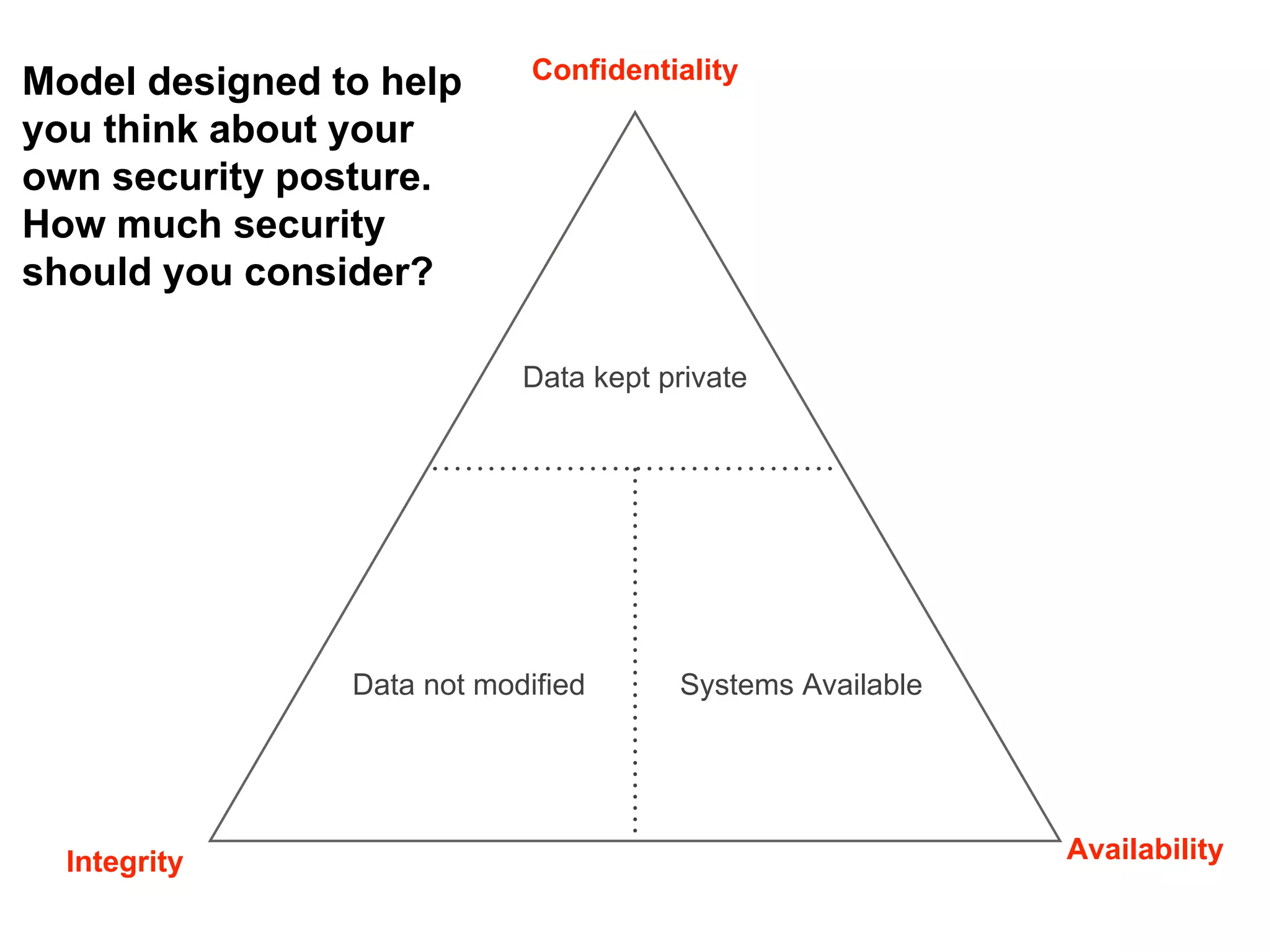
The document presents insights on website security from Sucuri, highlighting the importance of ensuring a safe online experience for users and the complexities of website environments. It outlines various attack vectors, the motivations behind hacking, and the potential impacts on a website's reputation and functionality. The author emphasizes the necessity of adopting a risk management approach to security, advocating for good administrative practices and professional help where needed.