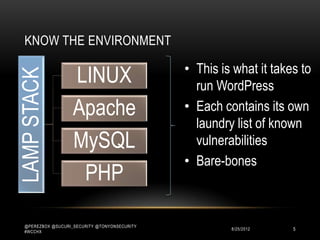
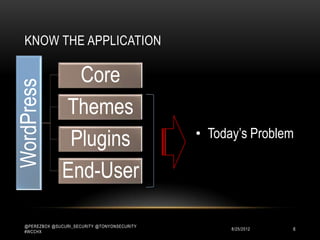
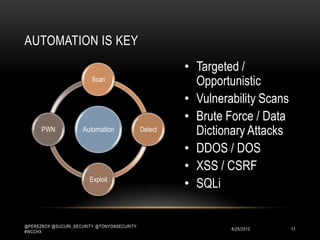
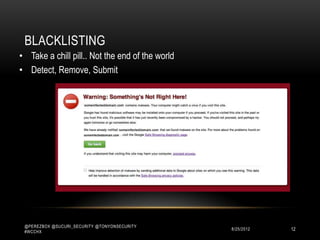
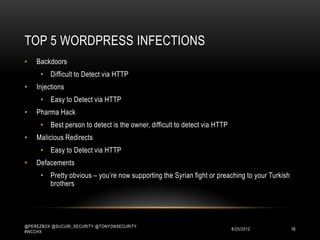
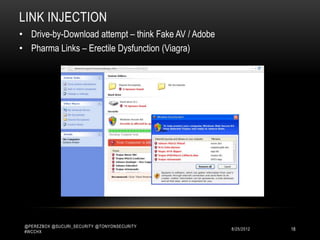
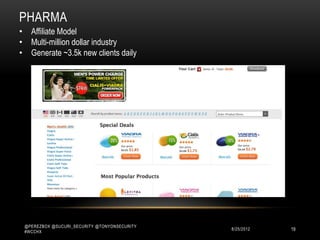
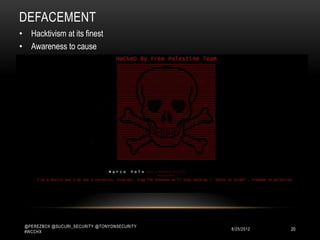
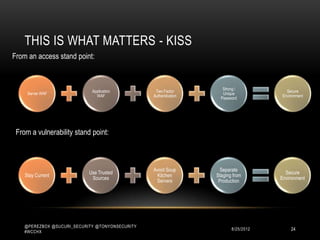
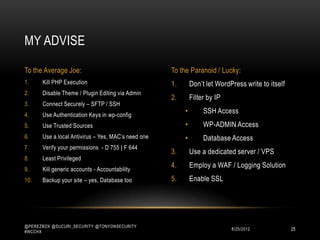
This document discusses WordPress security best practices. It notes that securing WordPress involves understanding the full technology stack, including the Linux operating system, web server (Apache), database (MySQL), and programming language (PHP). It also emphasizes the importance of securing access to the WordPress admin interface and files. Some key recommendations include using strong passwords and two-factor authentication for admin logins, installing a web application firewall for WordPress and the server, and ensuring WordPress plugins and themes are up-to-date to prevent exploits. The document stresses that most WordPress hacks occur due to gaining unauthorized access.













![KILL PHP EXECUTION
• The idea is not to let them execute any PHP files. You do so by adding this in an
.htaccess file in the directory of choice. Recommendation:
• WP-INCLUDES
• UPLOADS
#PROTECT [Directory Name]
<Files *.php>
Deny from all
</Files>
@PEREZBOX @SUCURI_SECURITY @TONYONSECURITY
#WCCHX
10/15/2012 26](https://image.slidesharecdn.com/wordcampchicago-wordpresssecurity-120821201101-phpapp01/85/WordPress-Security-The-No-BS-Version-26-320.jpg)



![BLACKLIST ENTITIES
• Google
• Chrome, FireFox
• Search Engine Results Page (SERP)
• http://www.google.com/webmaster/tools
• http://www.google.com/safebrowsing/diagnostic?site=[your site]
• Bing
• Internet Explorer
• Yahoo
• http://www.bing.com/toolbox/webmaster/
• Norton
• SafeWeb Browsing
• Facebook
• http://safeweb.norton.com/
• AVG
• Opera
• http://www.avgthreatlabs.com/sitereports/
@PEREZBOX @SUCURI_SECURITY @TONYONSECURITY
#WCCHX
10/15/2012 30](https://image.slidesharecdn.com/wordcampchicago-wordpresssecurity-120821201101-phpapp01/85/WordPress-Security-The-No-BS-Version-30-320.jpg)

