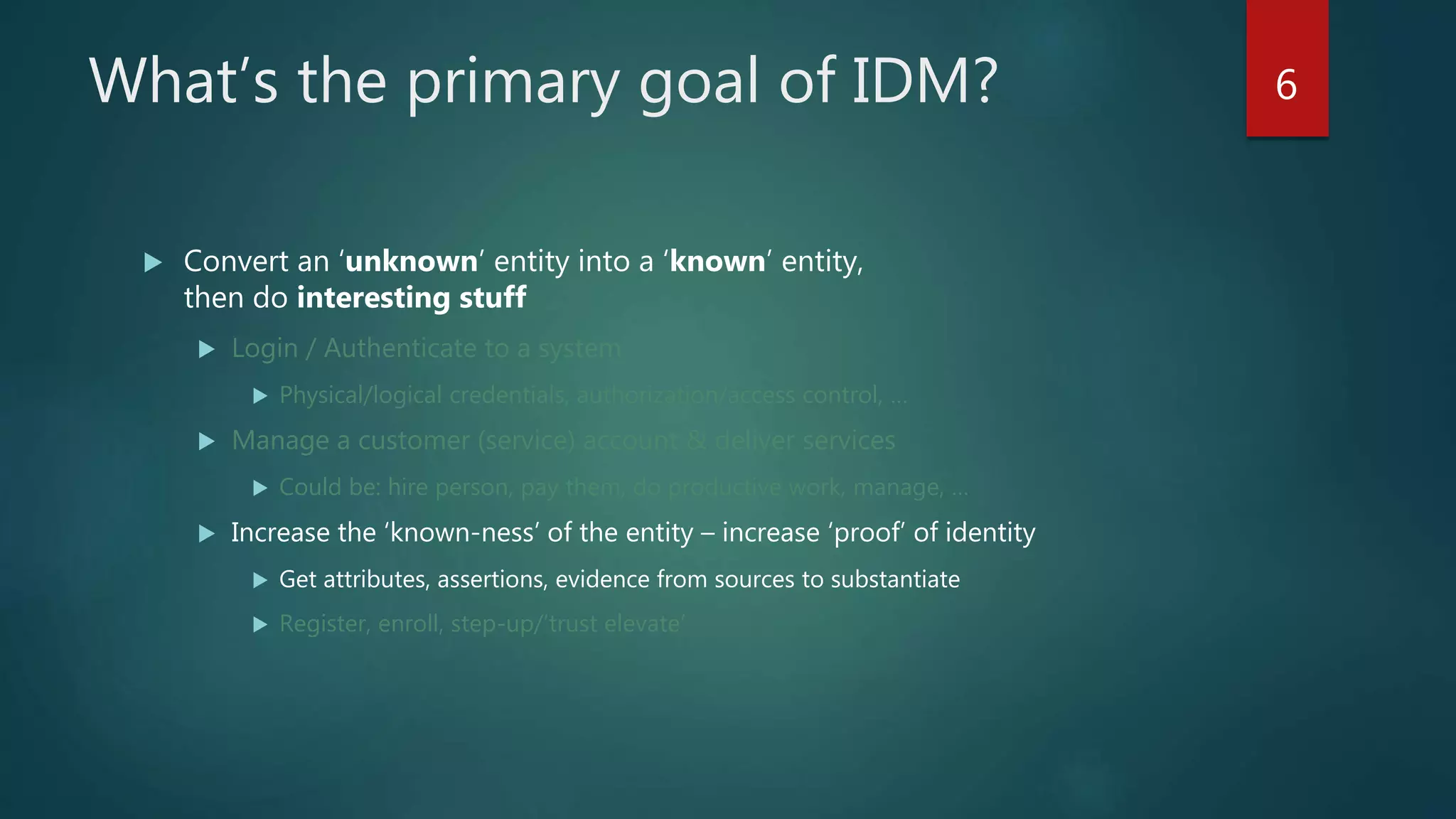
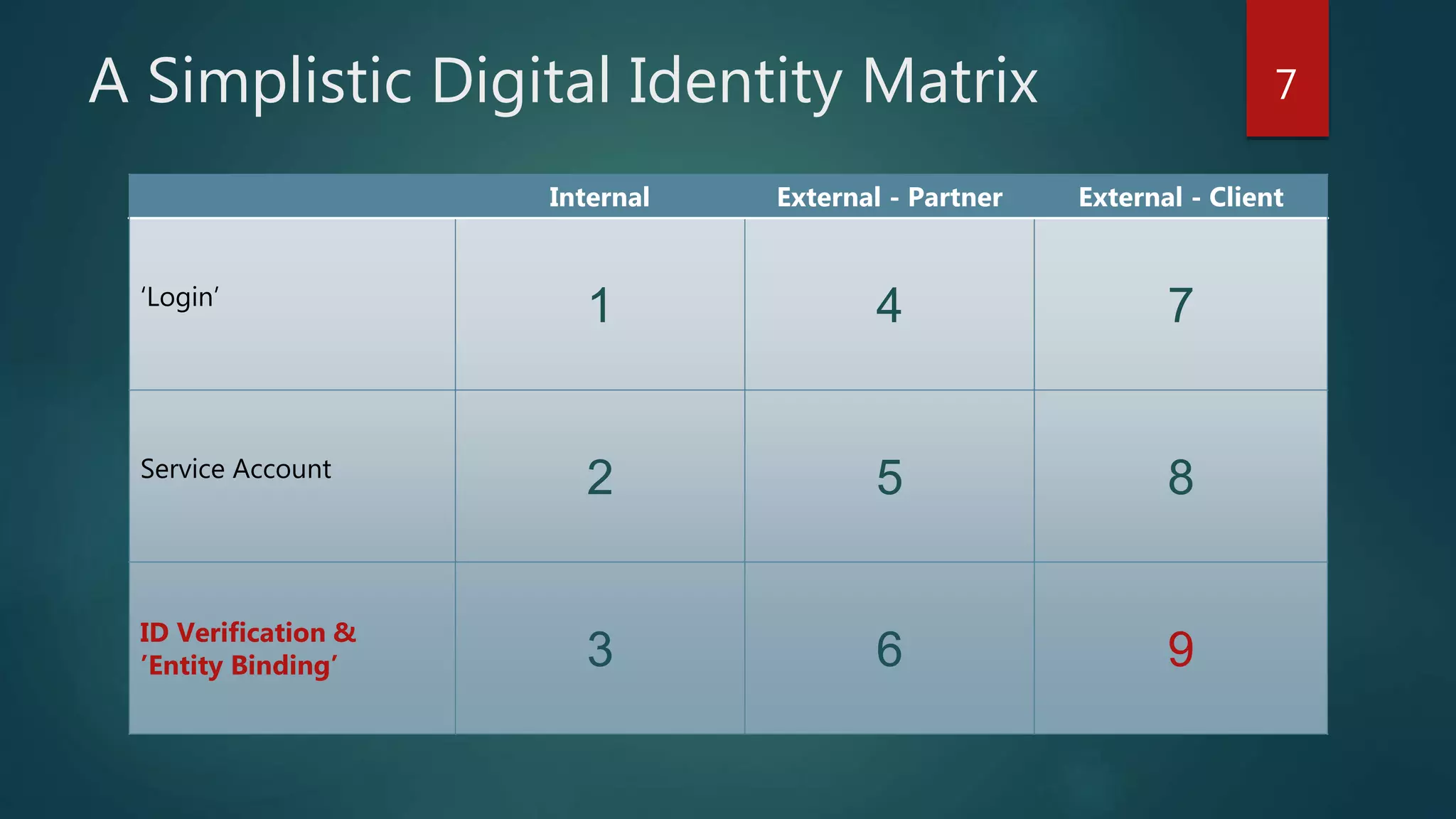
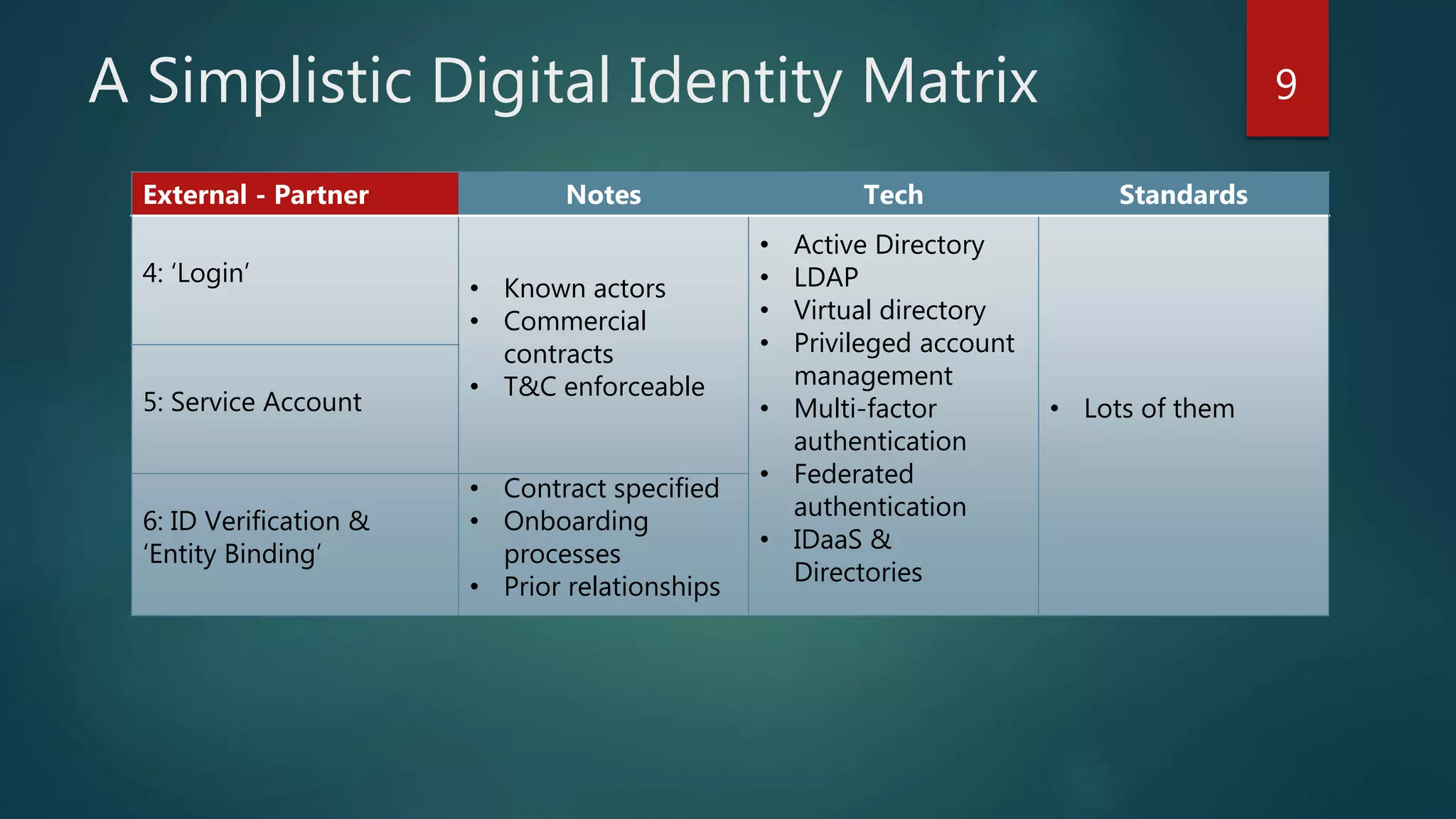
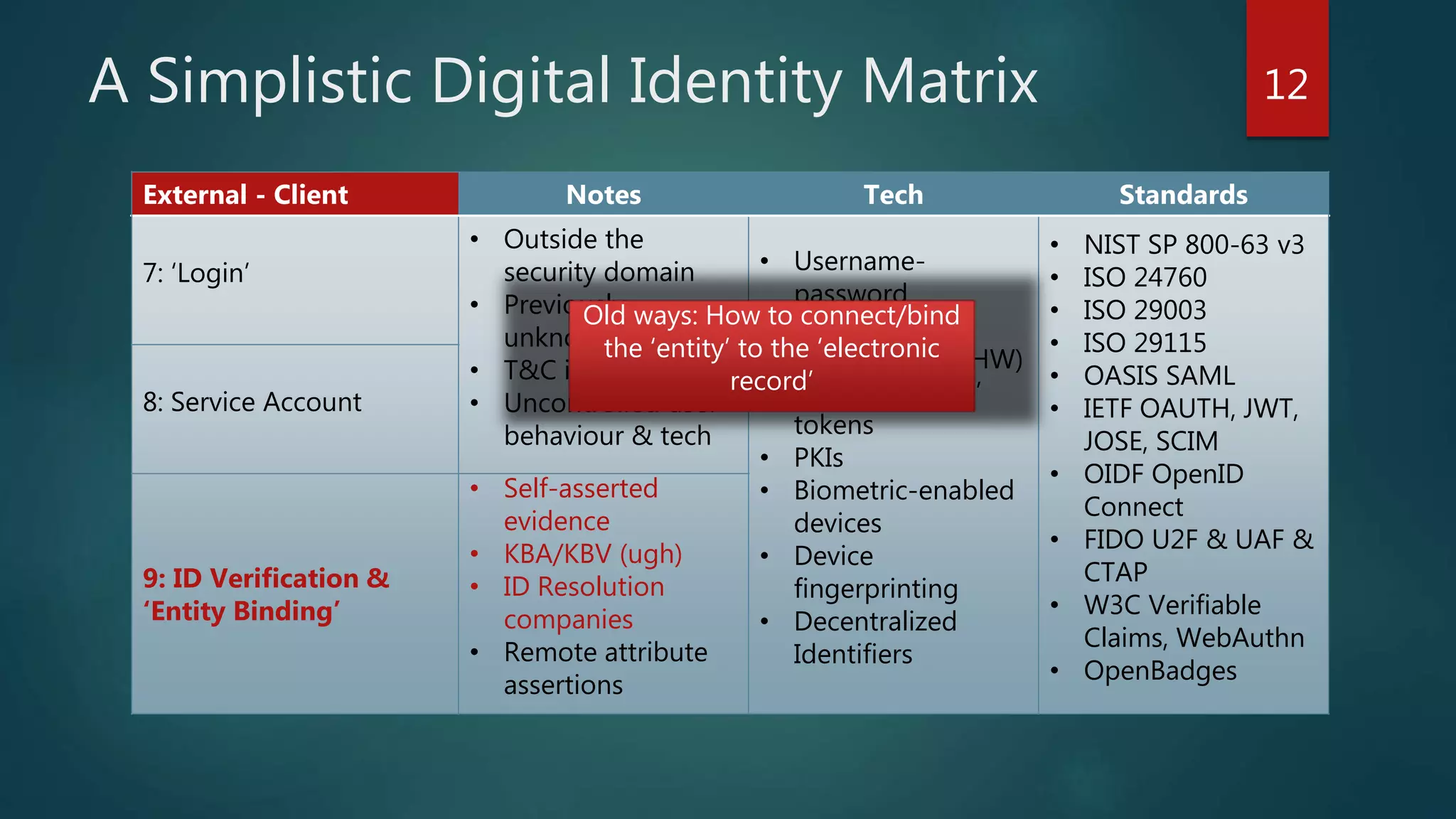
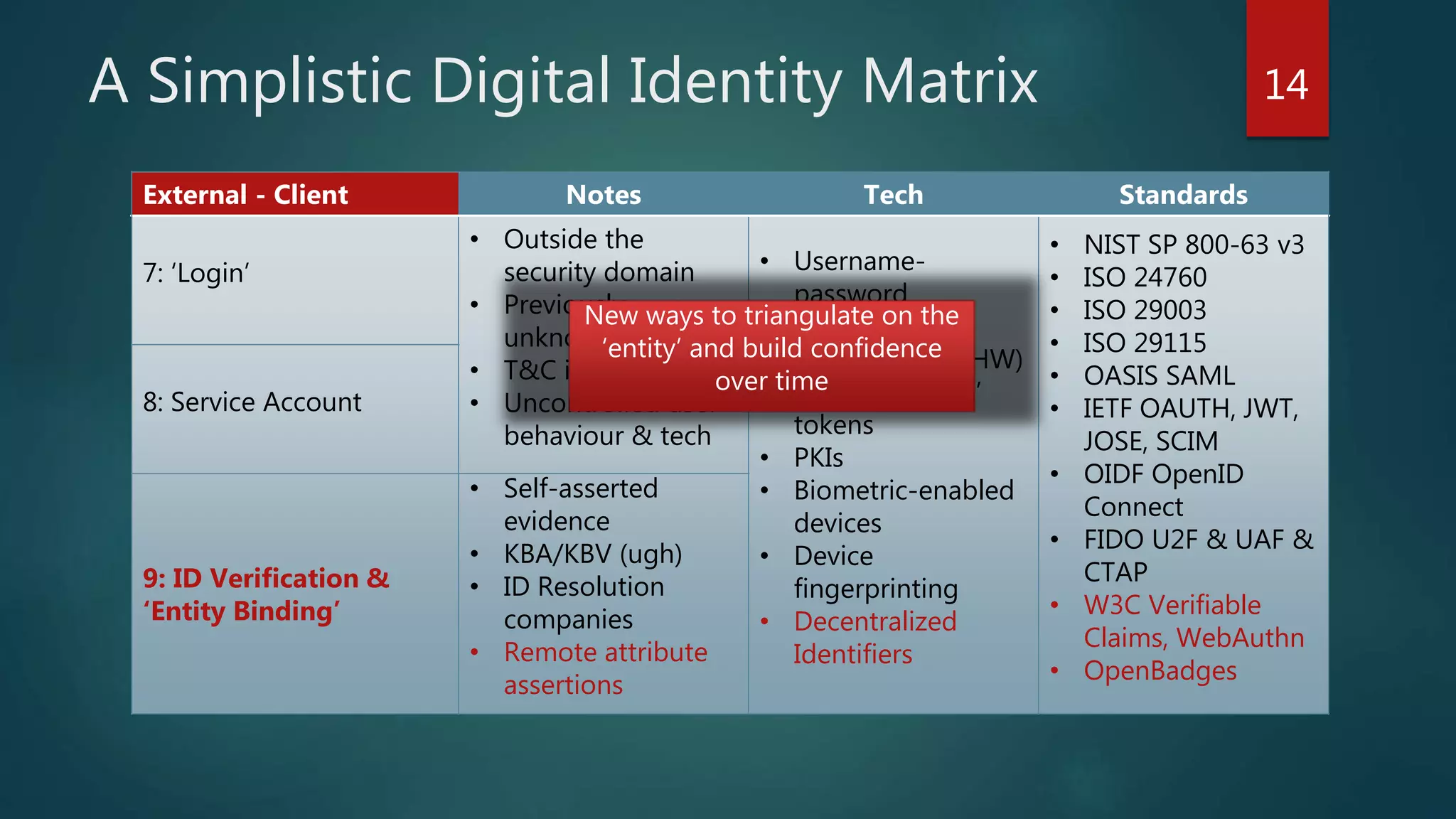
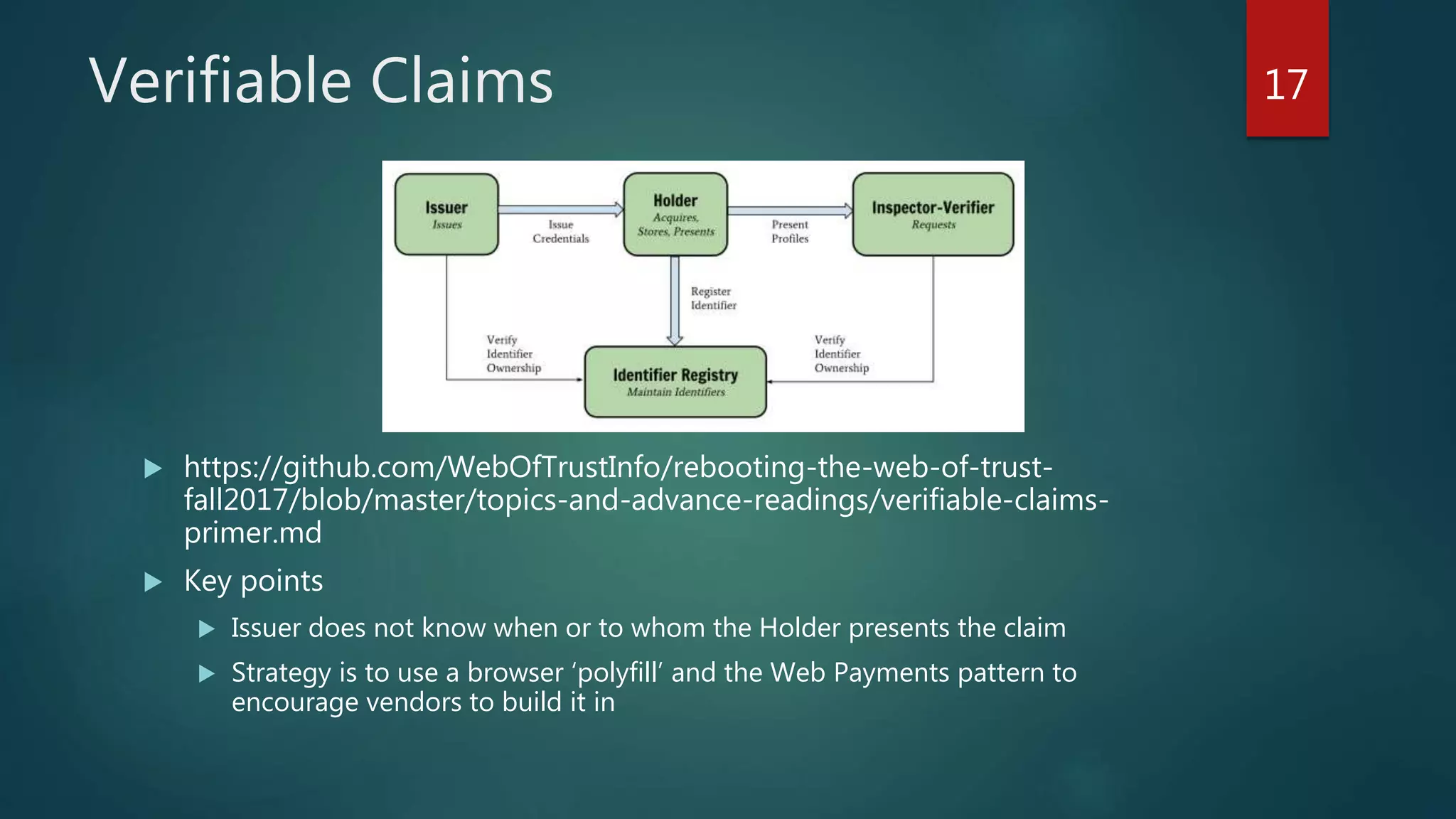
The document discusses the landscape of digital identity management (IDM) in a presentation by Andrew Hughes at the Vancouver IAM meetup. It covers the organizational contexts of identity management, goals of increasing the 'known-ness' of entities, evolving technologies such as decentralized identifiers, and the roles of trust and verification in user experience. The document emphasizes the need for new techniques for authenticating and managing digital identities while addressing challenges related to data reliability and user behavior.