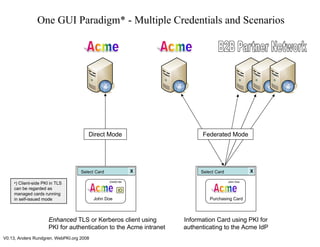
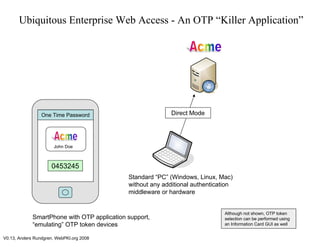
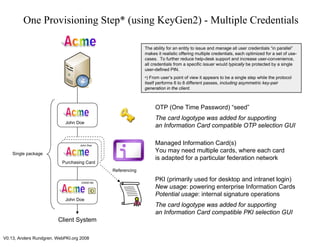
This document discusses two-factor authentication in enterprises and outlines a vision for a "united" enterprise multi-credential system. It claims that using a single enterprise credential does not fully address authentication needs due to technical and privacy limitations. Currently, different two-factor authentication schemes like OTP, PKI, and CardSpace are managed separately, making unified deployment difficult. The presented vision is based on work on KeyGen2, which would allow an entity to issue and manage multiple user credentials through a single provisioning step, while each credential is optimized for specific use cases. This could offer users multiple authentication options through a single interface.