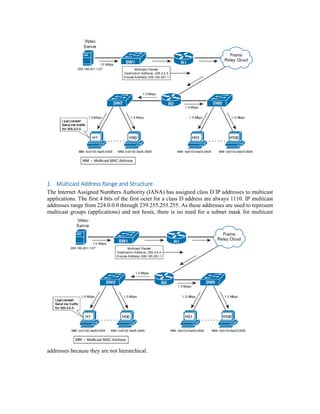
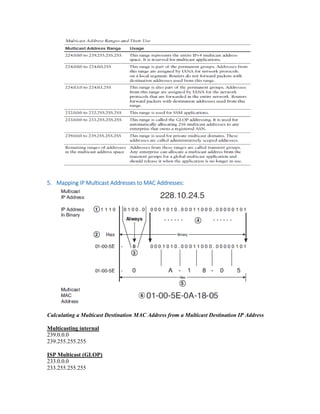
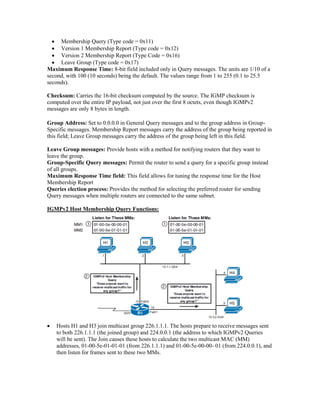
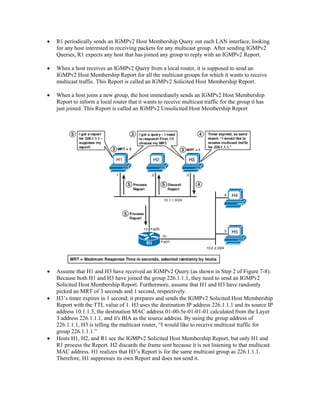
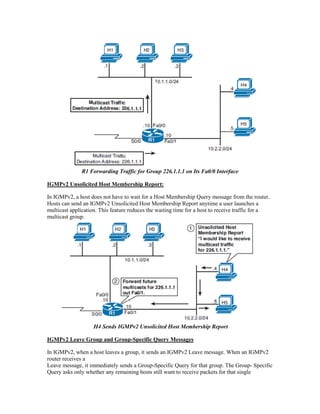
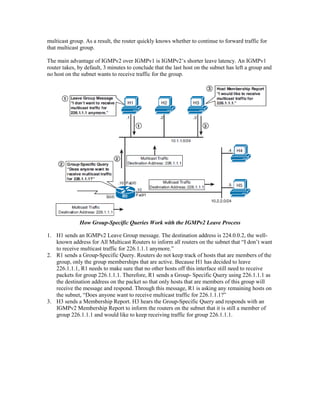
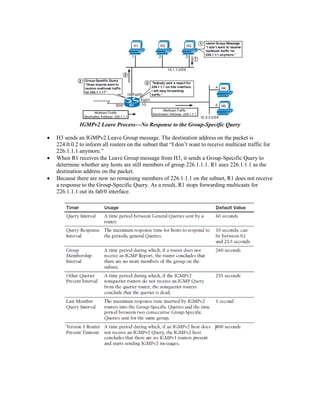
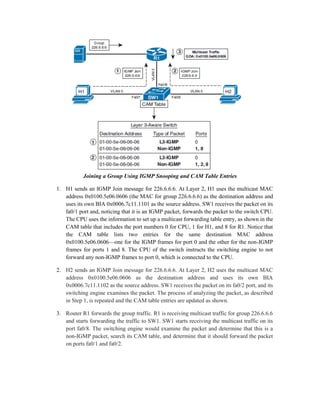
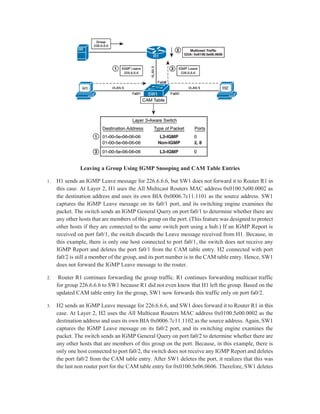
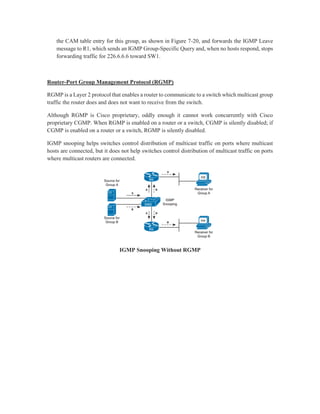
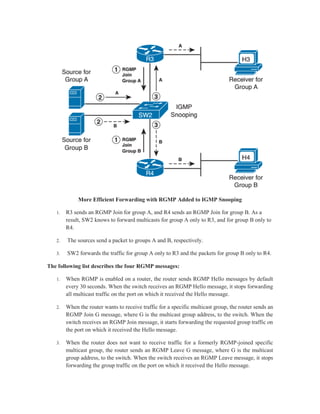
Multicast IP addresses range from 224.0.0.0 to 239.255.255.255. The document discusses well-known multicast addresses, calculating multicast MAC addresses from IP addresses, and protocols for managing multicast traffic distribution including IGMP, CGMP, IGMP snooping, and RGMP. IGMP is used by hosts to join and leave multicast groups and by routers to manage multicast traffic forwarding. Version 2 is the default and includes features like group-specific queries and shorter leave latency. CGMP and IGMP snooping allow switches to optimize multicast forwarding.