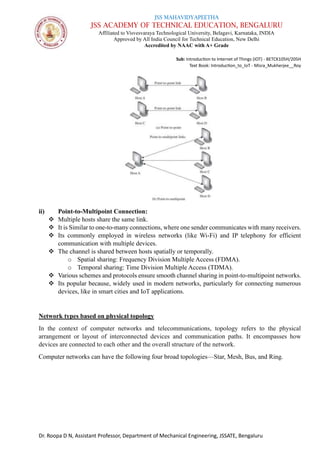
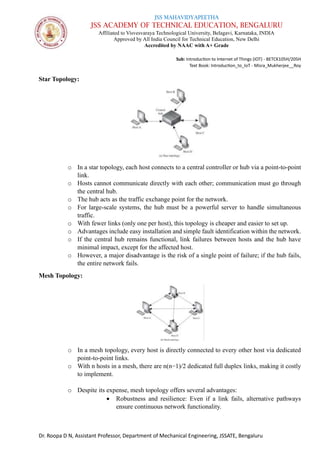
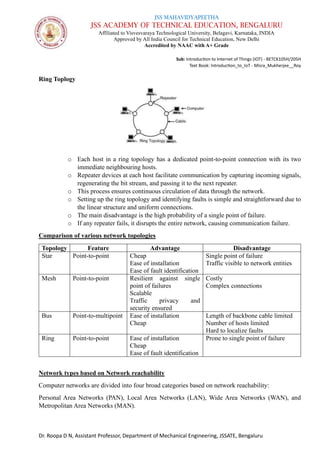
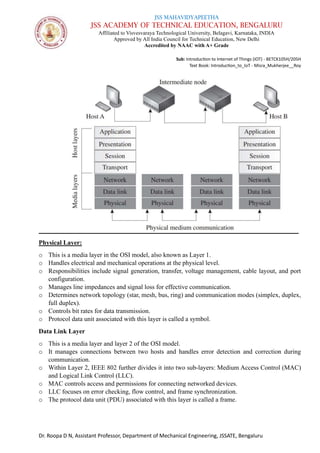
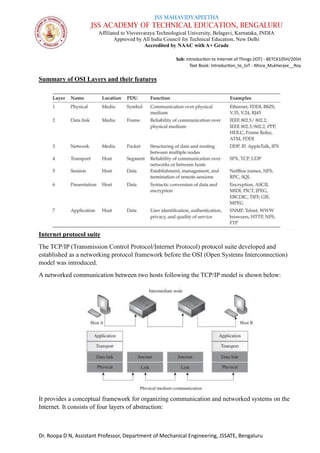
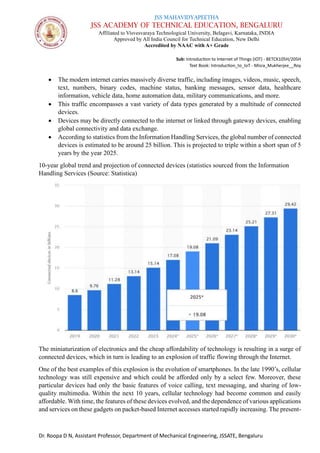
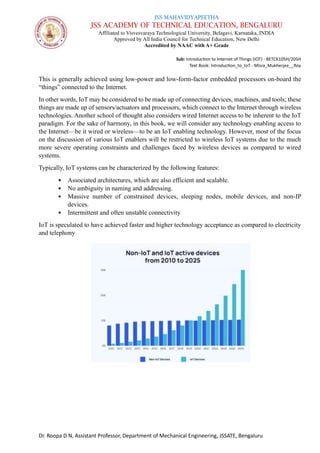
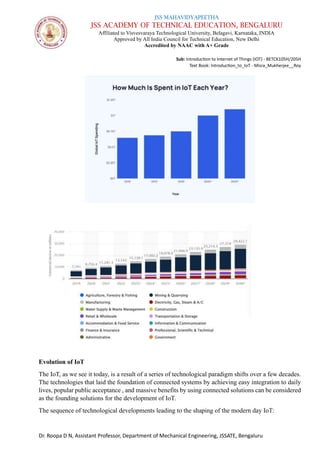
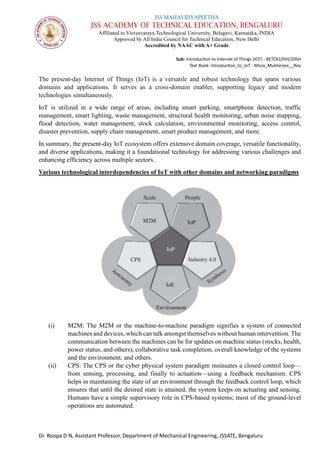
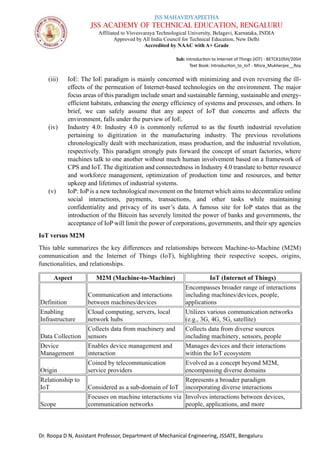
The document is a course syllabus for an introductory module on the Internet of Things (IoT) at JSS Academy of Technical Education, detailing fundamentals of networking and IoT technologies. It covers various network types, topologies, and layered network models, while providing key topics and questions for learning assessment. Additionally, it emphasizes the significance of data sharing and networking in modern technological applications.