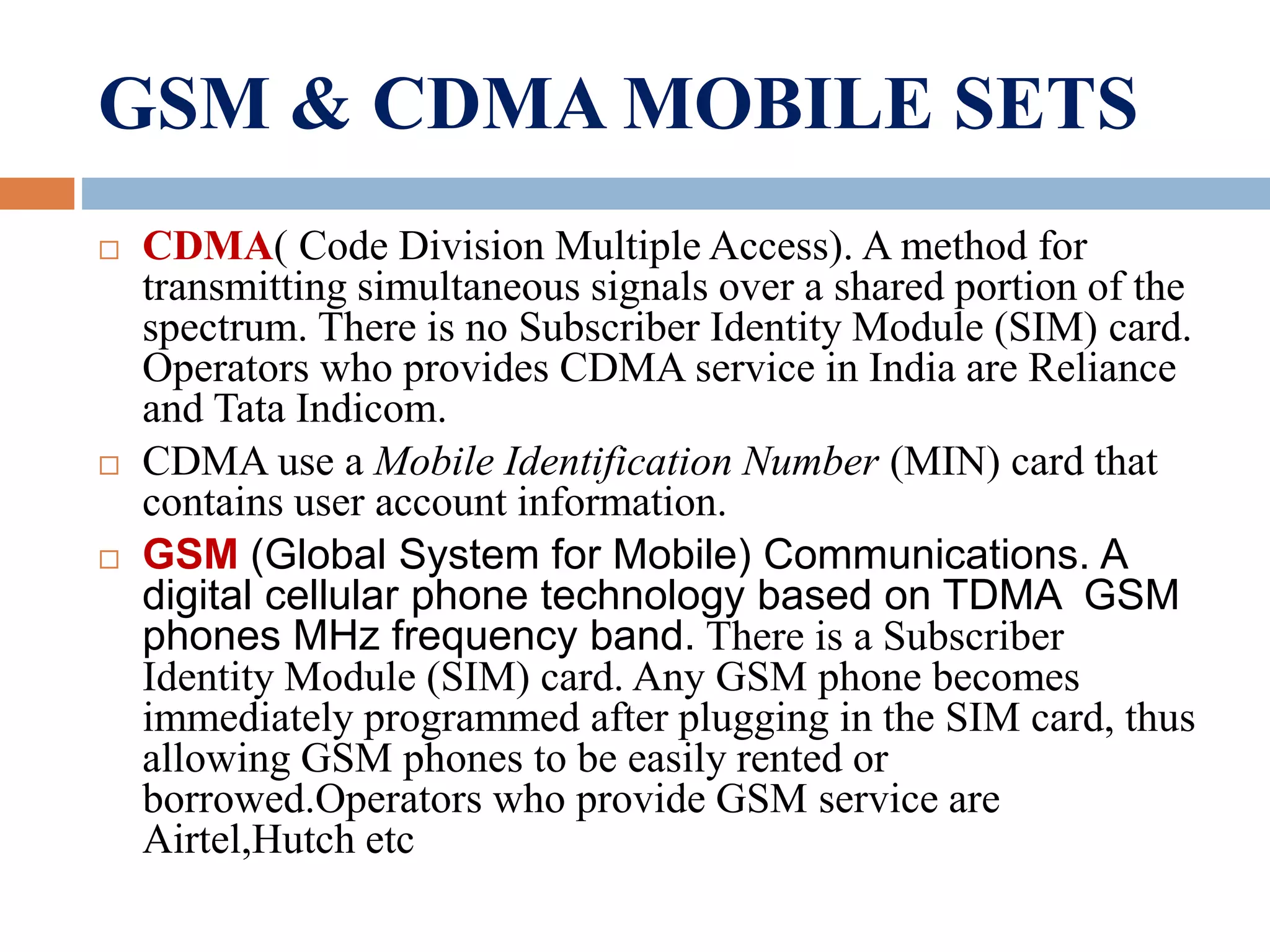
This document summarizes a seminar presentation on mobile phone cloning. It begins with an introduction that defines cloning as creating an exact genetic copy and explains that mobile phone cloning copies the identity of one phone to another, usually for fraudulent calls. It then covers topics like GSM and CDMA networks, how phones are cloned by capturing identifiers, methods to detect cloned phones, the impacts of cloning, and ways to prevent it. Statistics are provided on the costs of cloning to carriers and its use in criminal activities. The conclusion emphasizes the need for legislation against cloning fraud and for carriers and users to take security seriously.