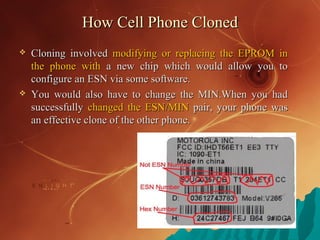
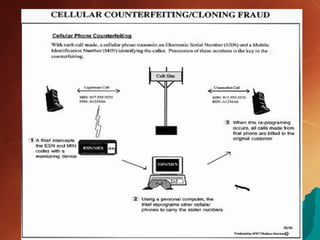
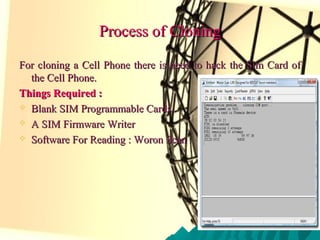
The document discusses cell phone cloning, detailing its definition, history, and types, as well as the processes involved in cloning mobile phones. It highlights the methods for detecting and preventing cloning, the impact on the mobile industry, and the repercussions on users. The conclusion emphasizes the need for improved security systems to combat the widespread and easily executable crime of mobile cloning.