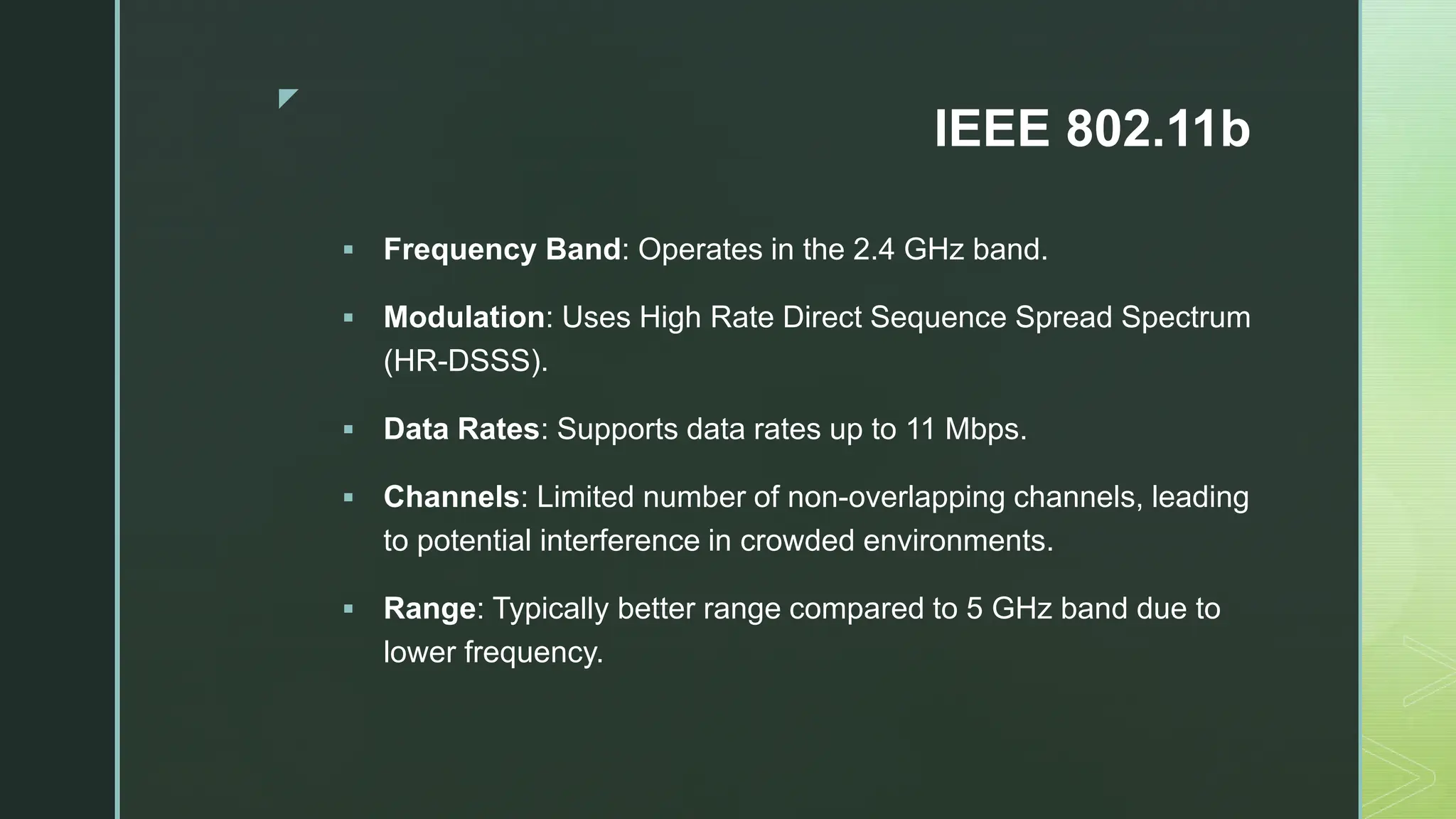
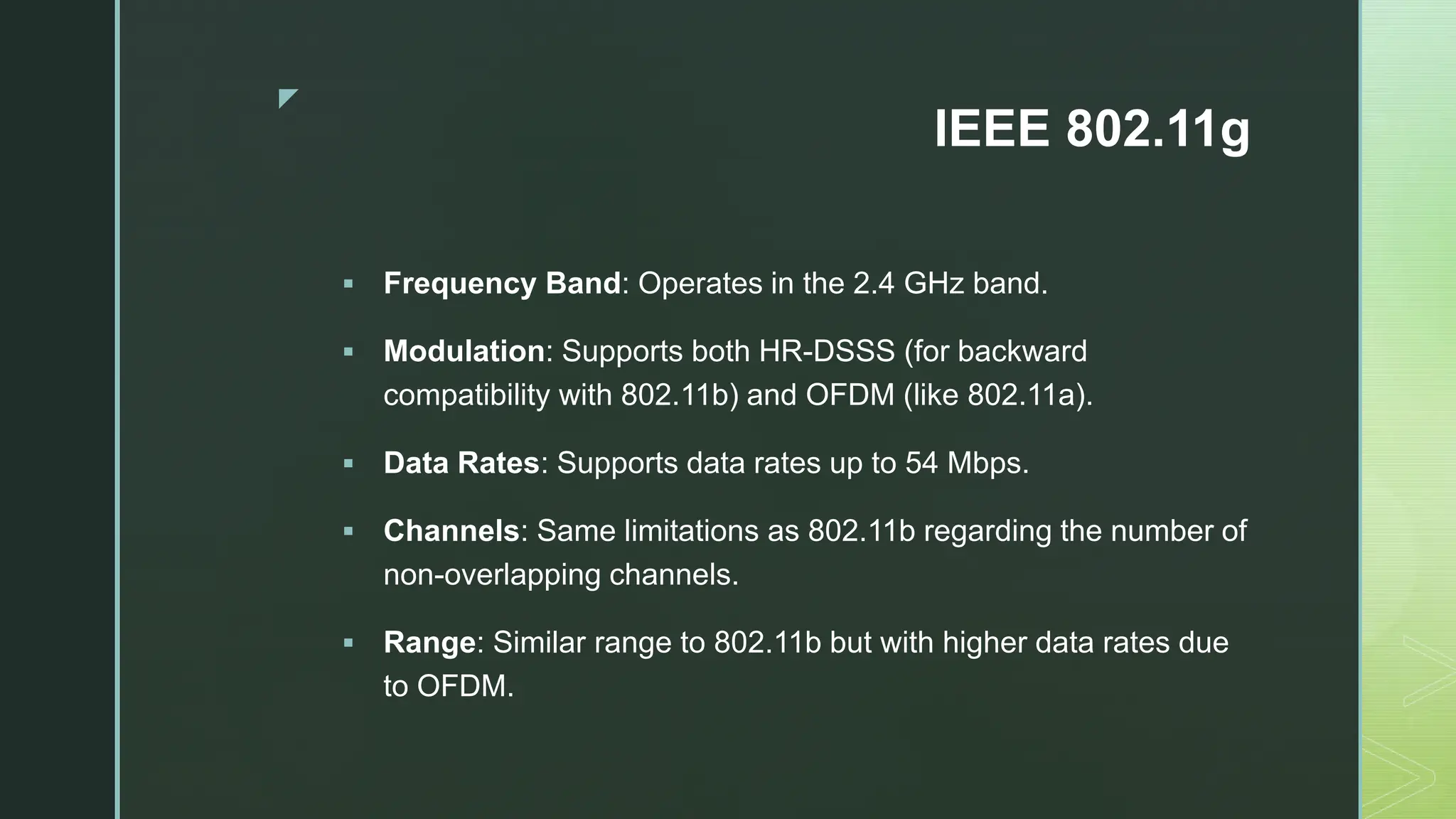
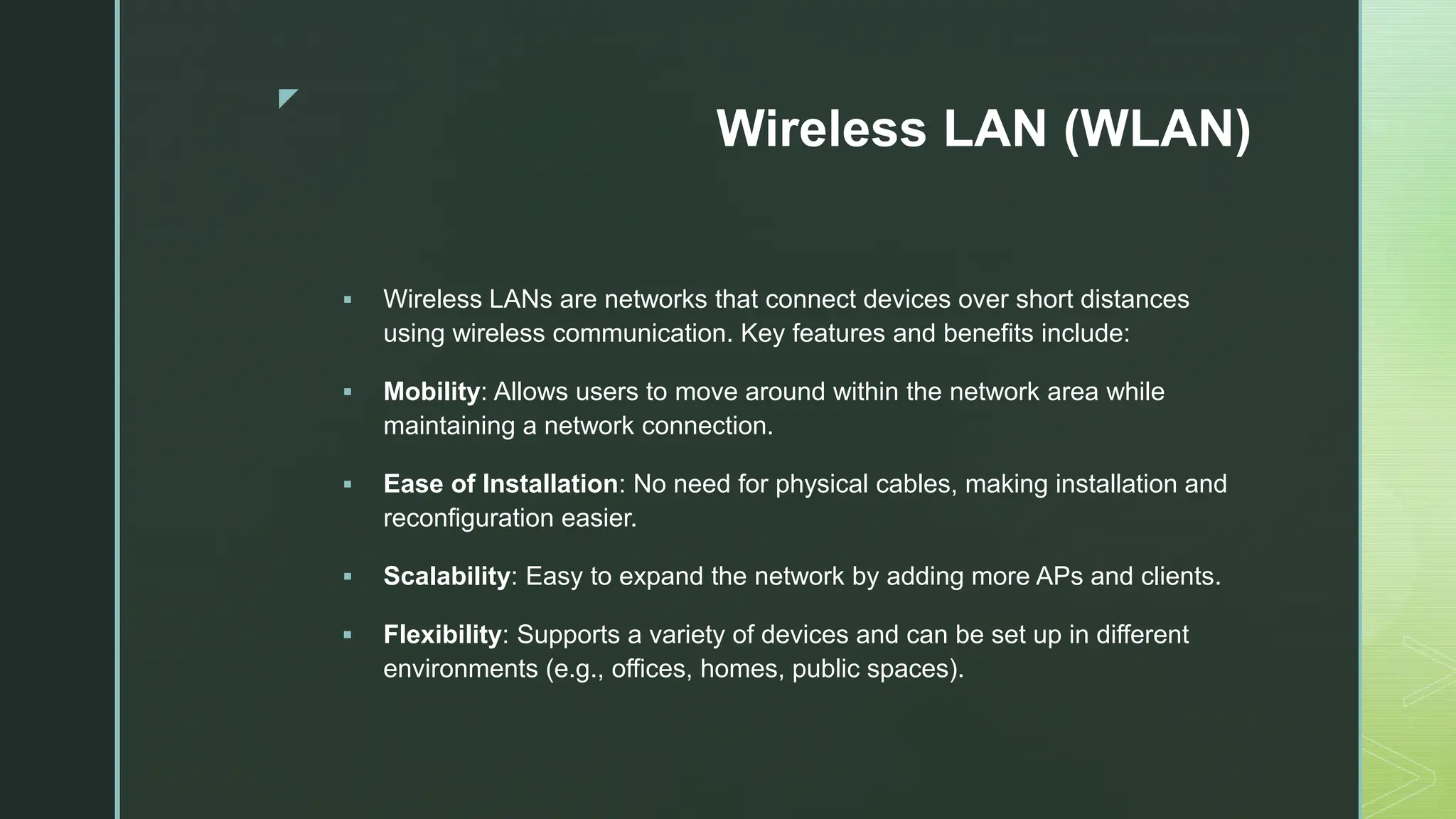
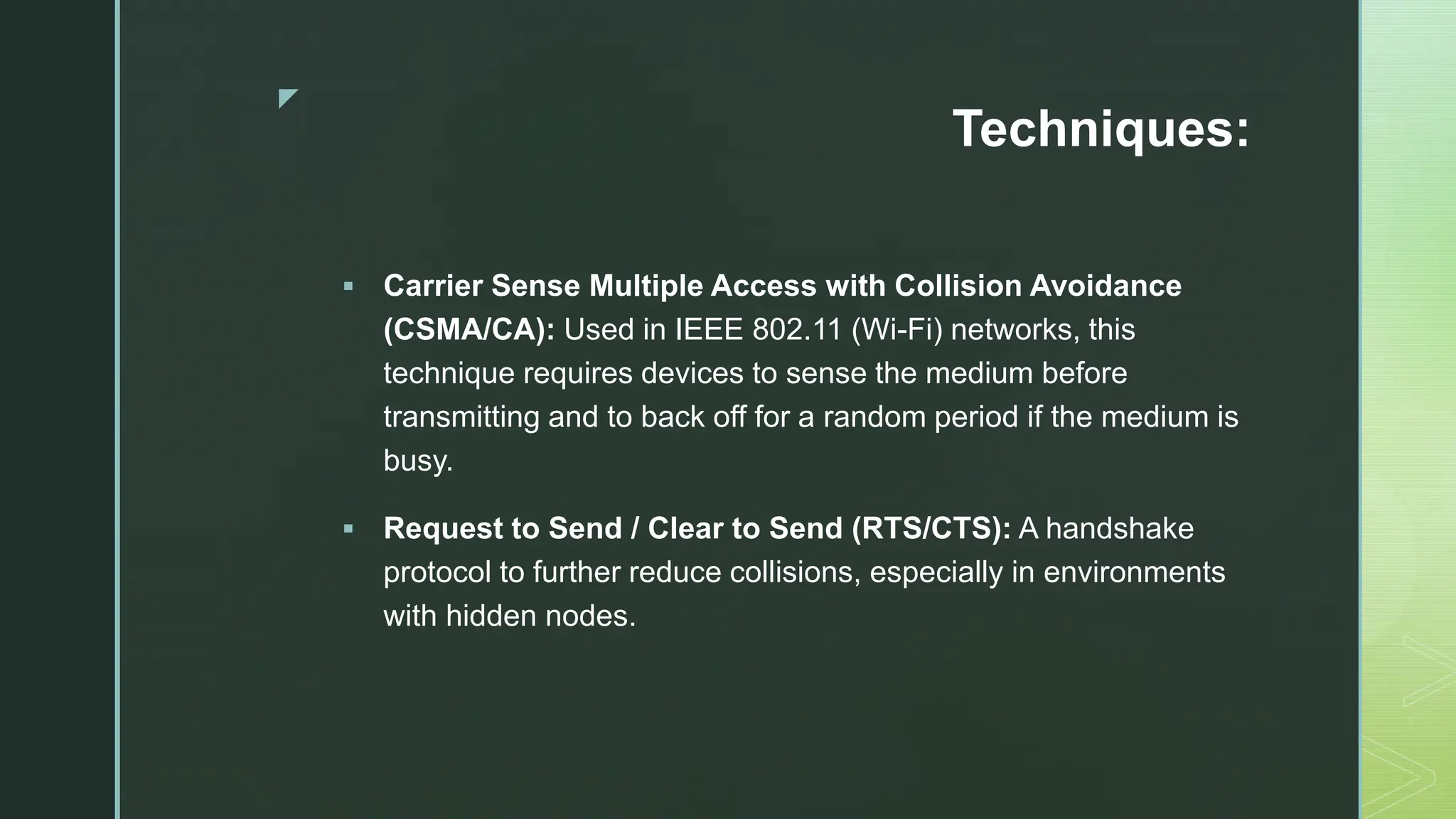
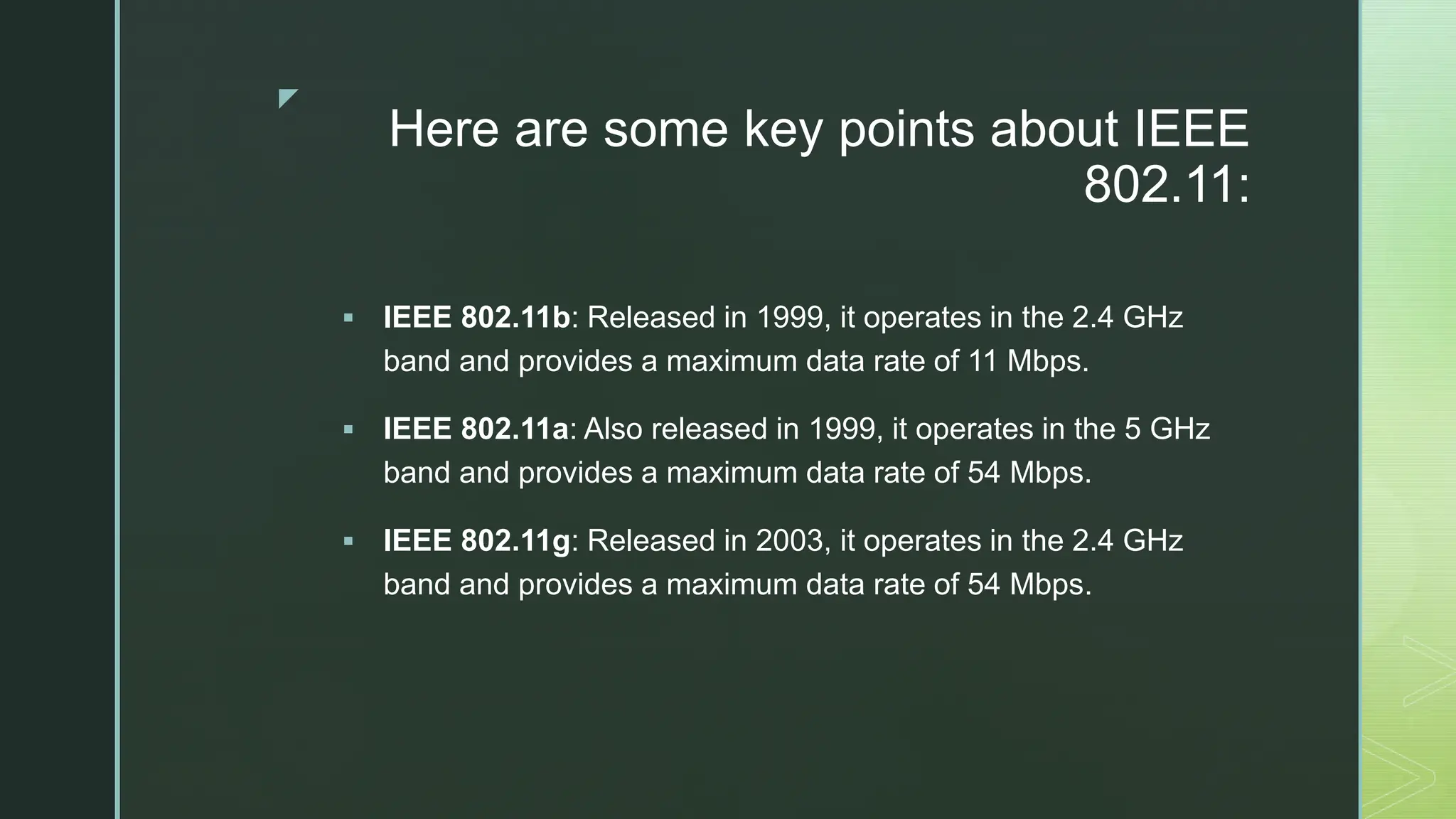
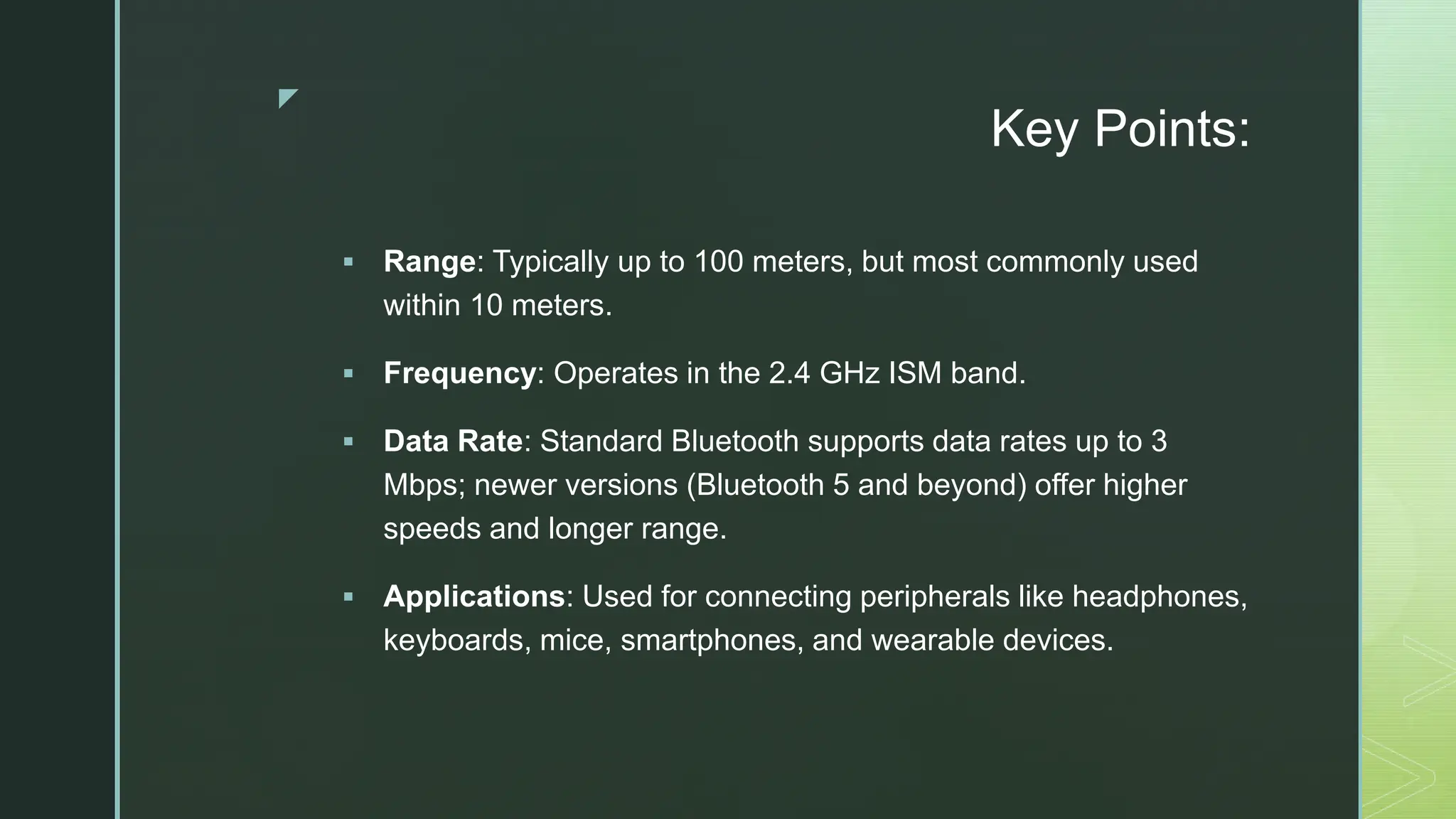
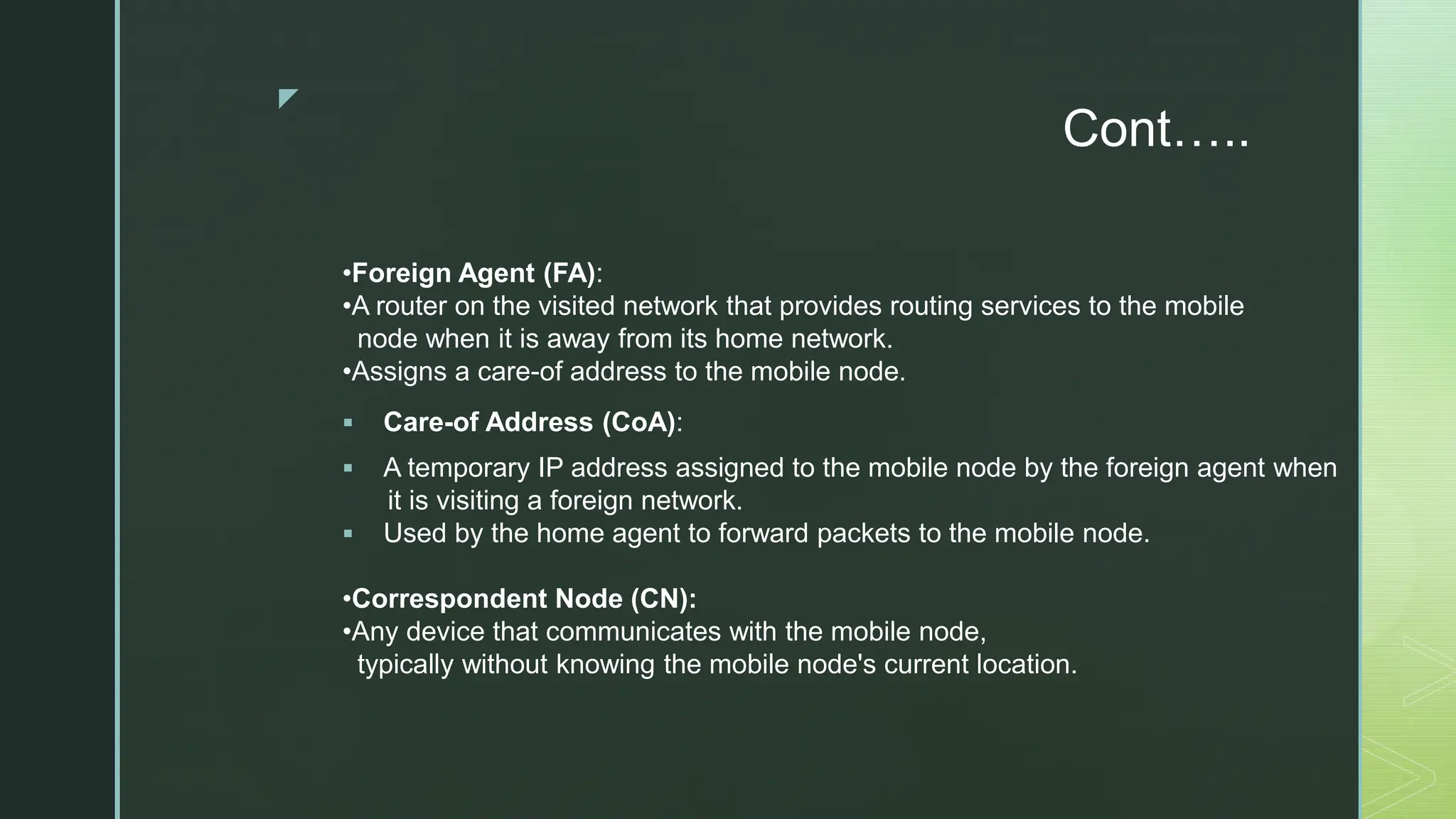
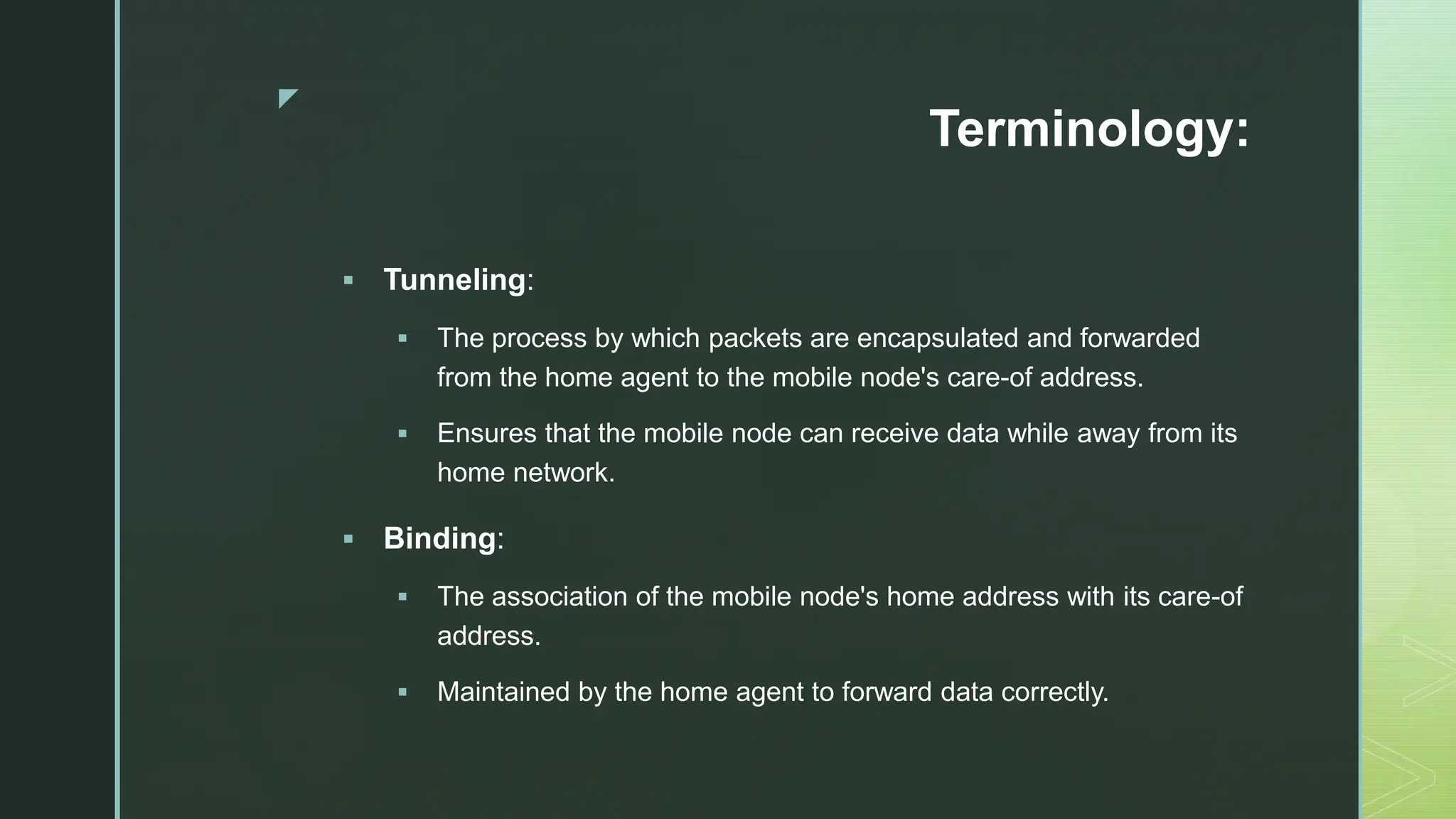
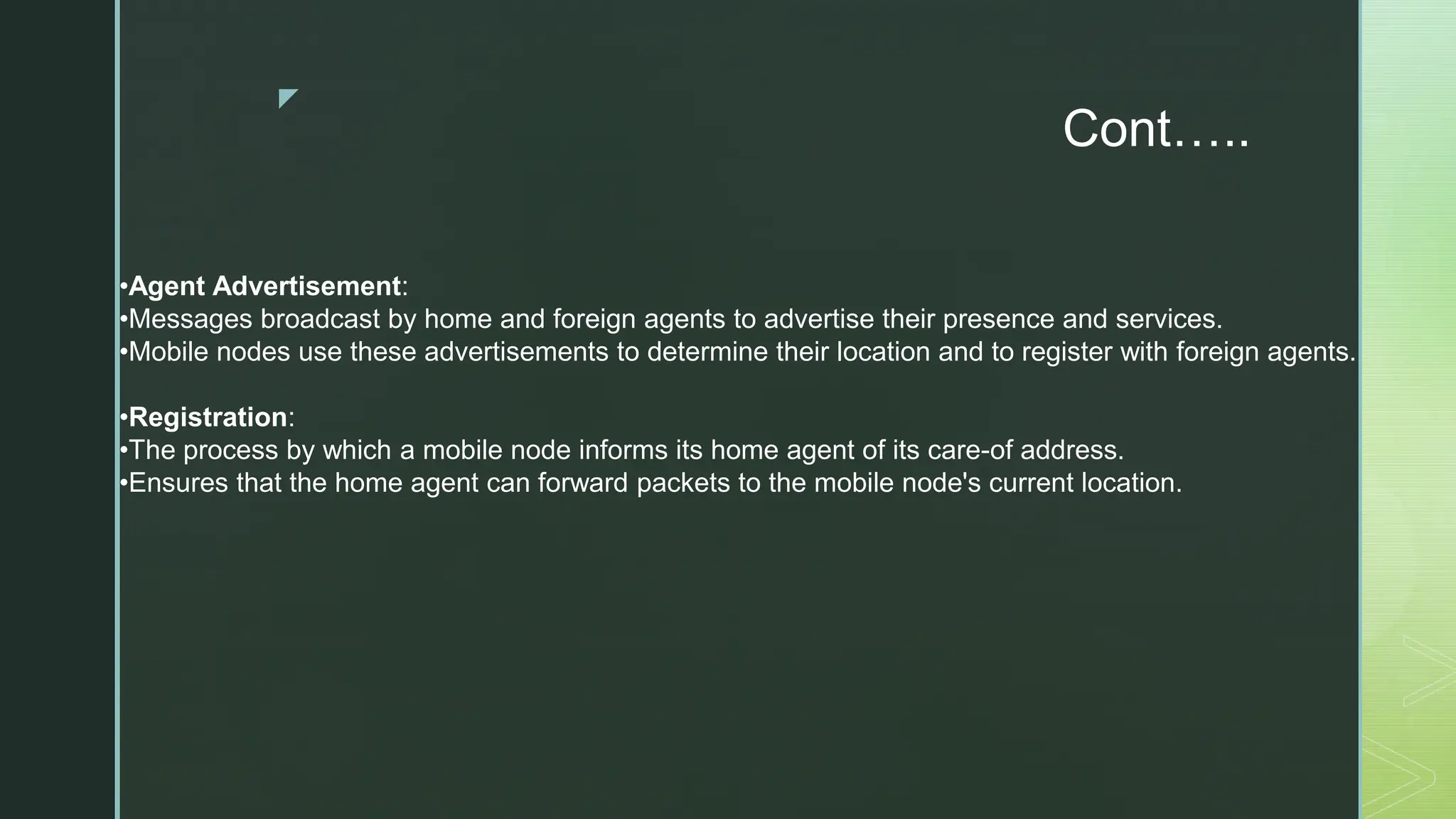
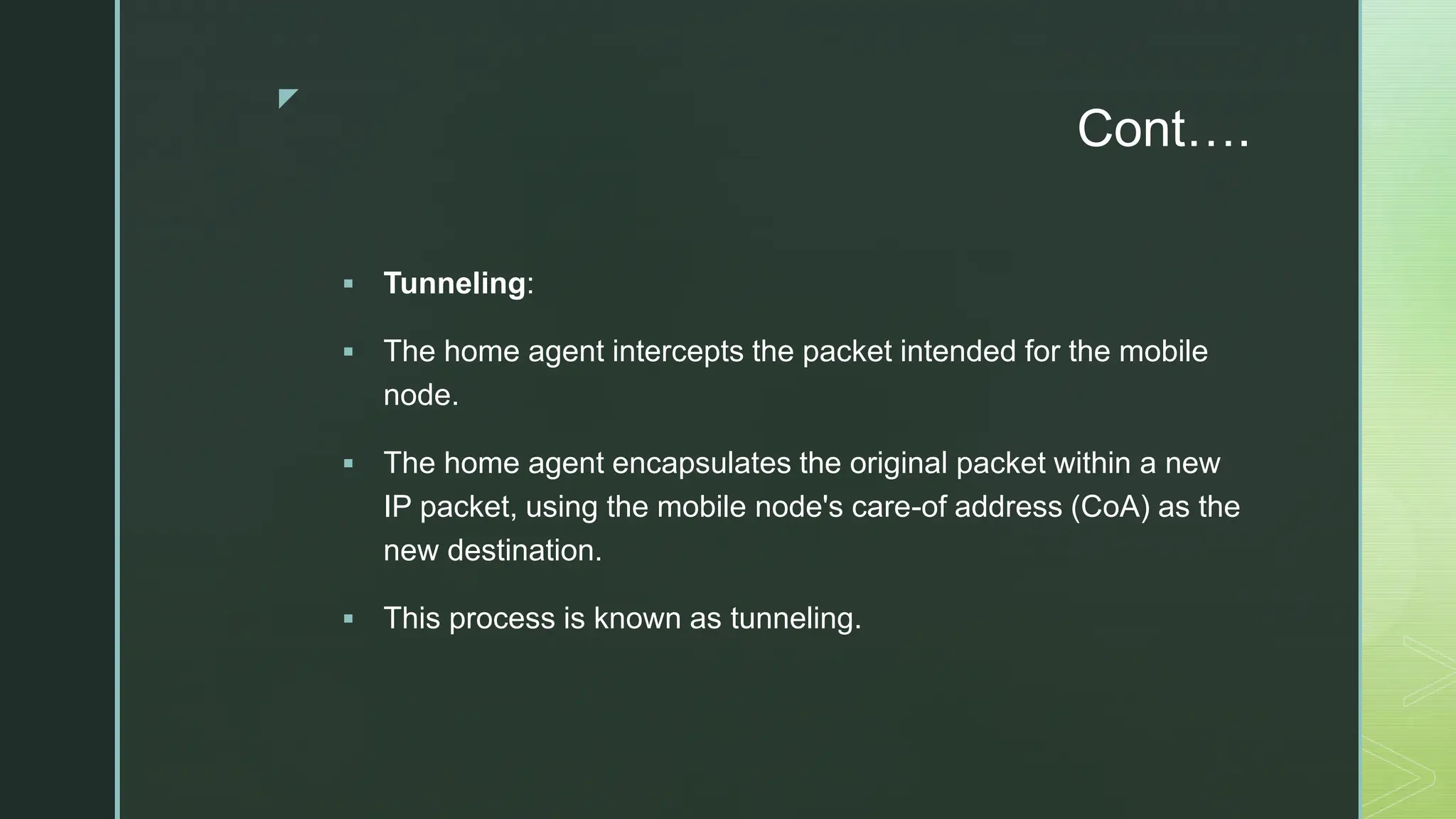
The document provides an extensive overview of mobile computing, covering the ISM bands, spread spectrum techniques, and various wireless networking standards such as IEEE 802.11. It discusses physical layer access methods like FHSS, DSSS, and OFDM, and addresses challenges such as security, efficiency, and complex network management. Additionally, it outlines the principles and terminology related to mobile IP and data broadcasting, emphasizing the significance of these technologies in enhancing wireless communications and functionality.