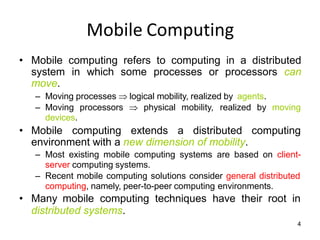
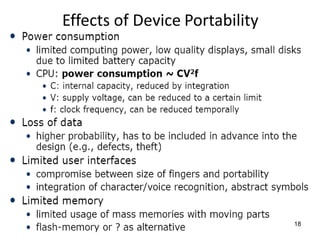
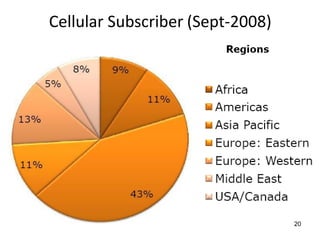
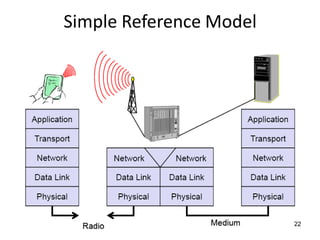
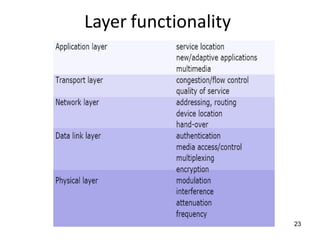
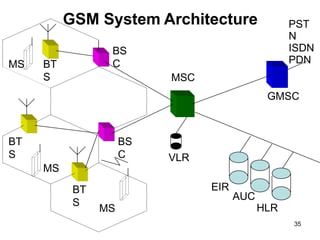
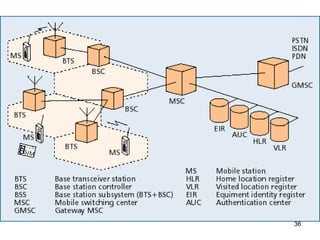
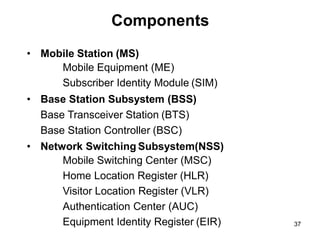
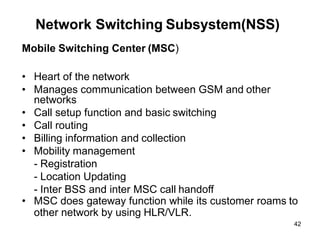
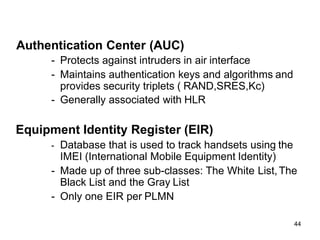
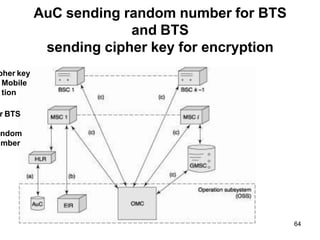
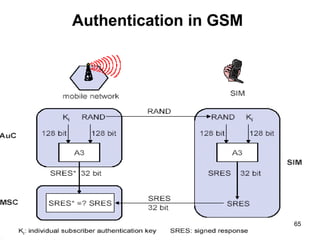
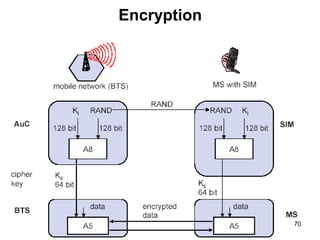
The lecture notes detail the principles and evolution of mobile computing and communication systems, emphasizing their distributed nature and the importance of user mobility. Key topics include the architecture of mobile systems, limitations of wireless networks, and the Global System for Mobile Communications (GSM) as a digital standard for voice and data services. The notes also cover the components of GSM, such as mobile stations and network switching subsystems, alongside security measures implemented to protect user privacy and resource access.









![Novel Applications [2]
15](https://image.slidesharecdn.com/mobilecomputingunit-1-210503042611/85/Mobile-computing-15-320.jpg)
![Novel Applications [3]
16](https://image.slidesharecdn.com/mobilecomputingunit-1-210503042611/85/Mobile-computing-16-320.jpg)



![24
PART-II
Global System for Mobile
Communication [GSM]](https://image.slidesharecdn.com/mobilecomputingunit-1-210503042611/85/Mobile-computing-24-320.jpg)


![27
Introduction to GSM [2]
• Developed by Group Special Mobile (founded 1982) which was an
initiative of CEPT ( Conference of European Post and Telecom )
• Aim : to replace the incompatible analog system
• Presently the responsibility of GSM standardization resides with special
mobile group under ETSI (European telecom Standards Institute )
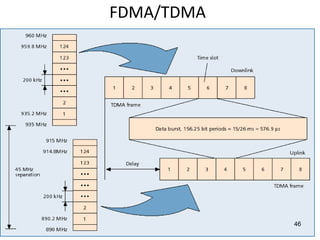
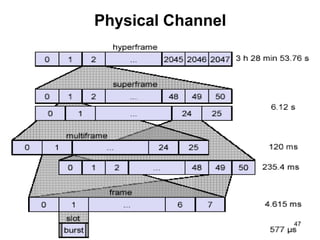
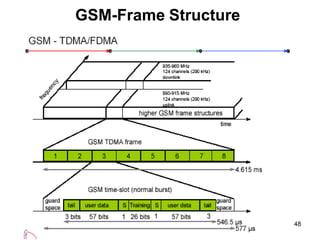
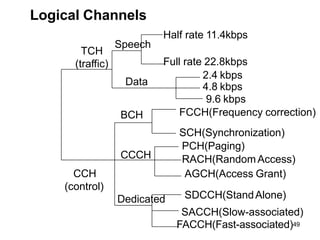
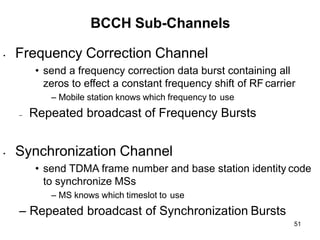
• GSM have 124 duplex channels, each 200Khz wide, are used for FDMA.
• GSM offer data rates of up to 9.6Kbps and up to a speed of 250Km/hr
• Under ETSI, GSM is named as ―
Global System for Mobile communication ―
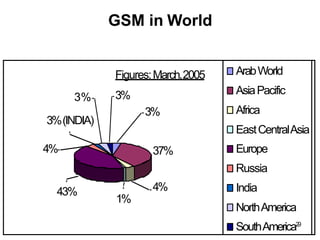
• Today many providers all over the world use GSM (more than 190
countries in Asia, Africa, Europe, Australia,America)
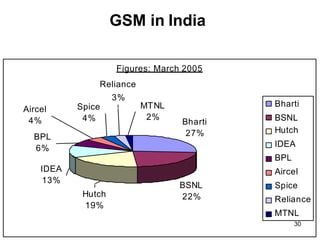
• More than 1300 million subscribers in world & 45 million subscriber in India.](https://image.slidesharecdn.com/mobilecomputingunit-1-210503042611/85/Mobile-computing-27-320.jpg)



























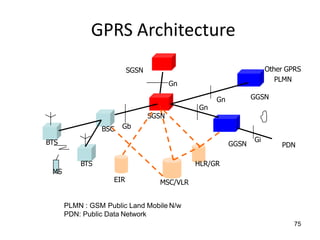
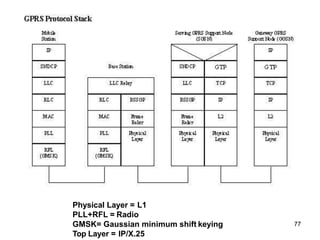
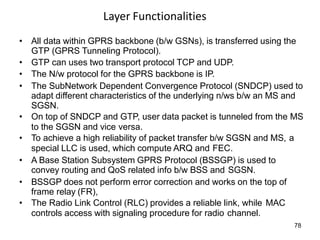
![74
GPRS [2]
• It offers point-to-point packet transfer in 2 versions
– PTP connection-oriented service (PTP-CONS)
– PTP connectionless service (PTP-CNLS)
• It also offers Multicasting, called Point-to-Multipoint
(PTM) service
• User specify QoS profile
– Service precedence (high, normal, low)
– Reliability class
– Delay class
– Peak throughput class for data
– Mean throughput class for data](https://image.slidesharecdn.com/mobilecomputingunit-1-210503042611/85/Mobile-computing-74-320.jpg)