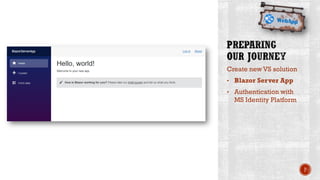
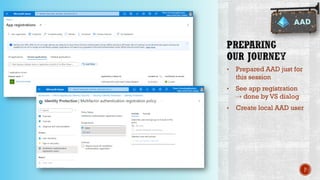
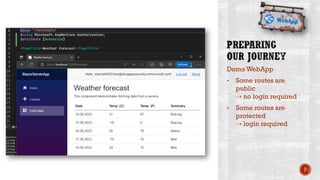
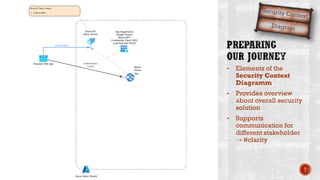
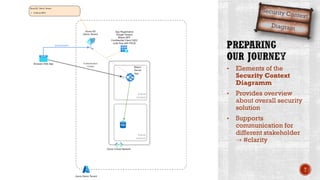
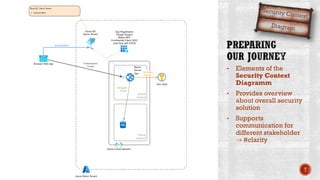
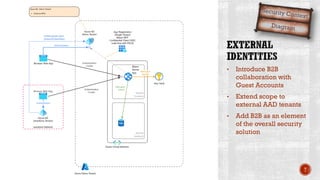
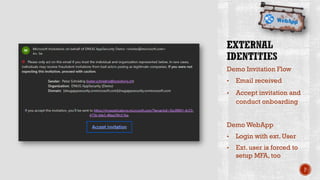
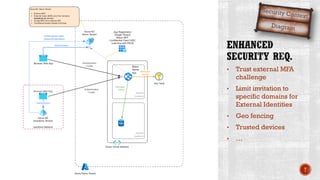
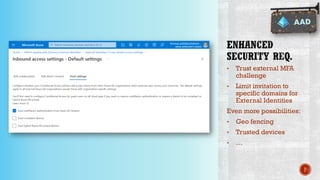
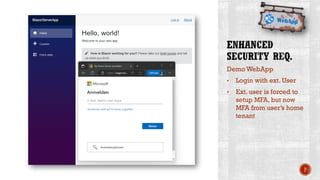
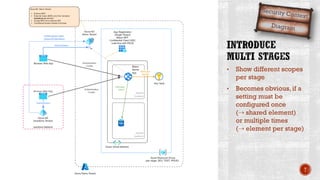
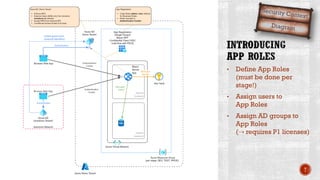
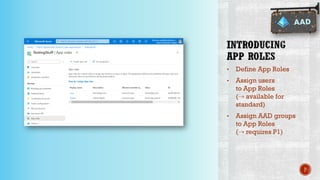
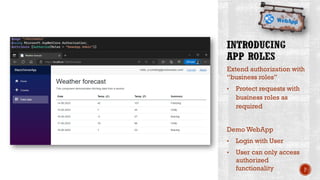
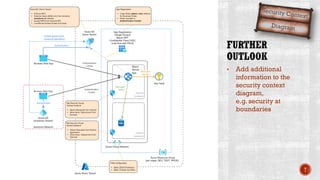
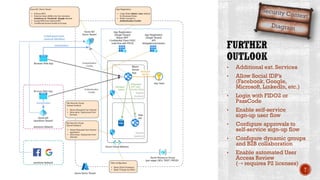
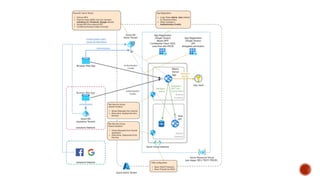
The document discusses creating secure .Net applications and implementing a zero trust security model. It introduces security context models which provide a framework for understanding authentication and authorization in modern applications. The remainder of the document outlines a demo of building a Blazor web application secured with Azure Active Directory, including authentication of external users, authorization with application roles, and using a security context diagram to communicate the security solution.