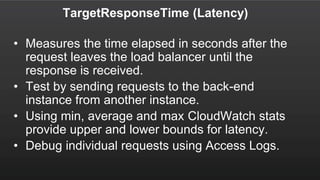
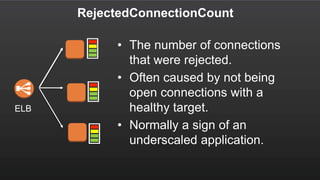
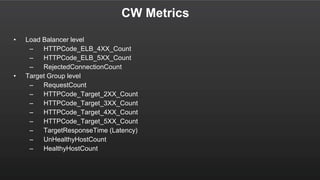
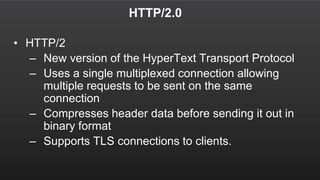
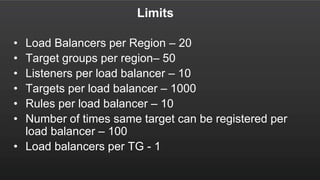
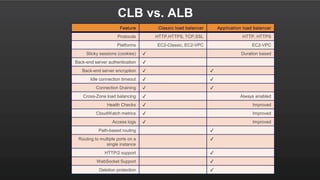
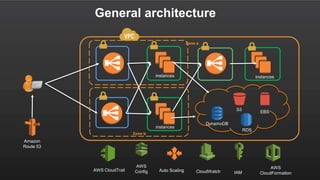
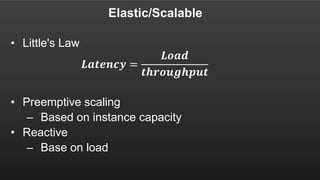
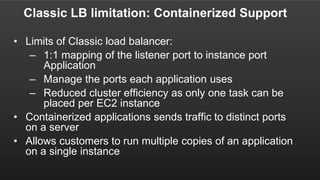
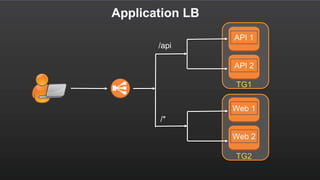
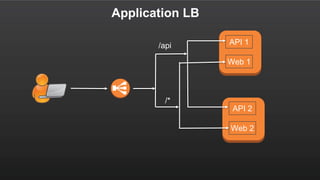
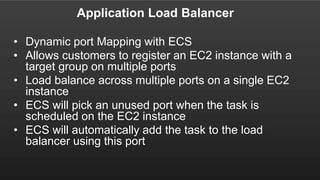
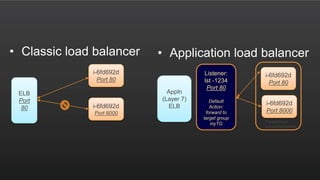
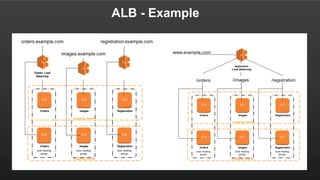
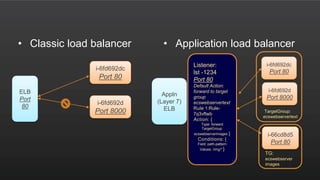
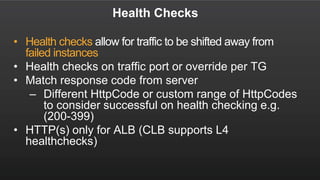
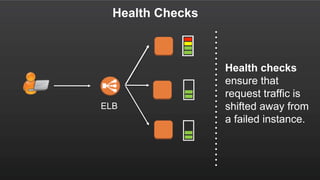
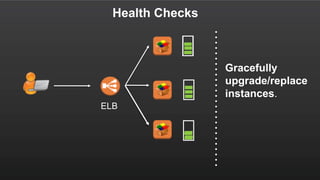
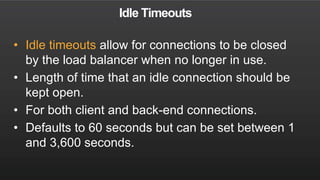
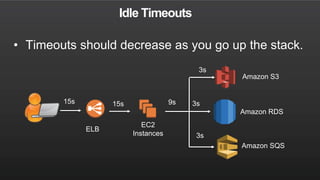
The document summarizes a meetup about AWS Elastic Load Balancing (ELB). The meetup covered an overview of ELB, the new Application Load Balancer, and a demo. It discussed key ELB concepts like health checks, metrics, logging, and integration with other AWS services. The new ALB supports features like path-based routing and HTTP/2 that improve on the classic load balancer.



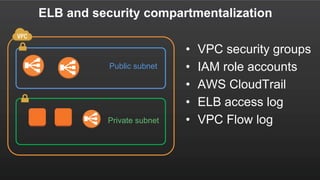




![Access Log
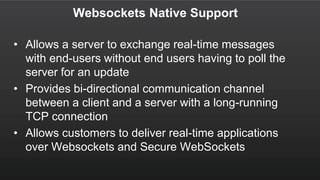
• S3
– bucket[/prefix]/AWSLogs/aws-account-
id/elasticloadbalancing/region/yyyy/mm/dd/aws-account-
id_elasticloadbalancing_region_load-balancer-id_end-time_ip-
address_random-string.log.gz
– ELB put files into S3 bucket(s) you own.
• Format:
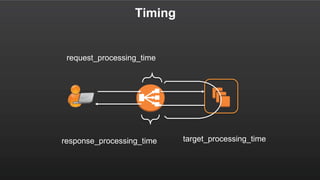
– type timestamp elb client:port target:port
request_processing_time target_processing_time
response_processing_time elb_status_code target_status_code
received_bytes sent_bytes "request" "user_agent" ssl_cipher
ssl_protocol target_group_arn](https://image.slidesharecdn.com/thuandb-elb-deepdiveandbestpractices-awsvn-161123105843/85/Meetup-4-AWS-ELB-Deep-dive-Best-practices-36-320.jpg)