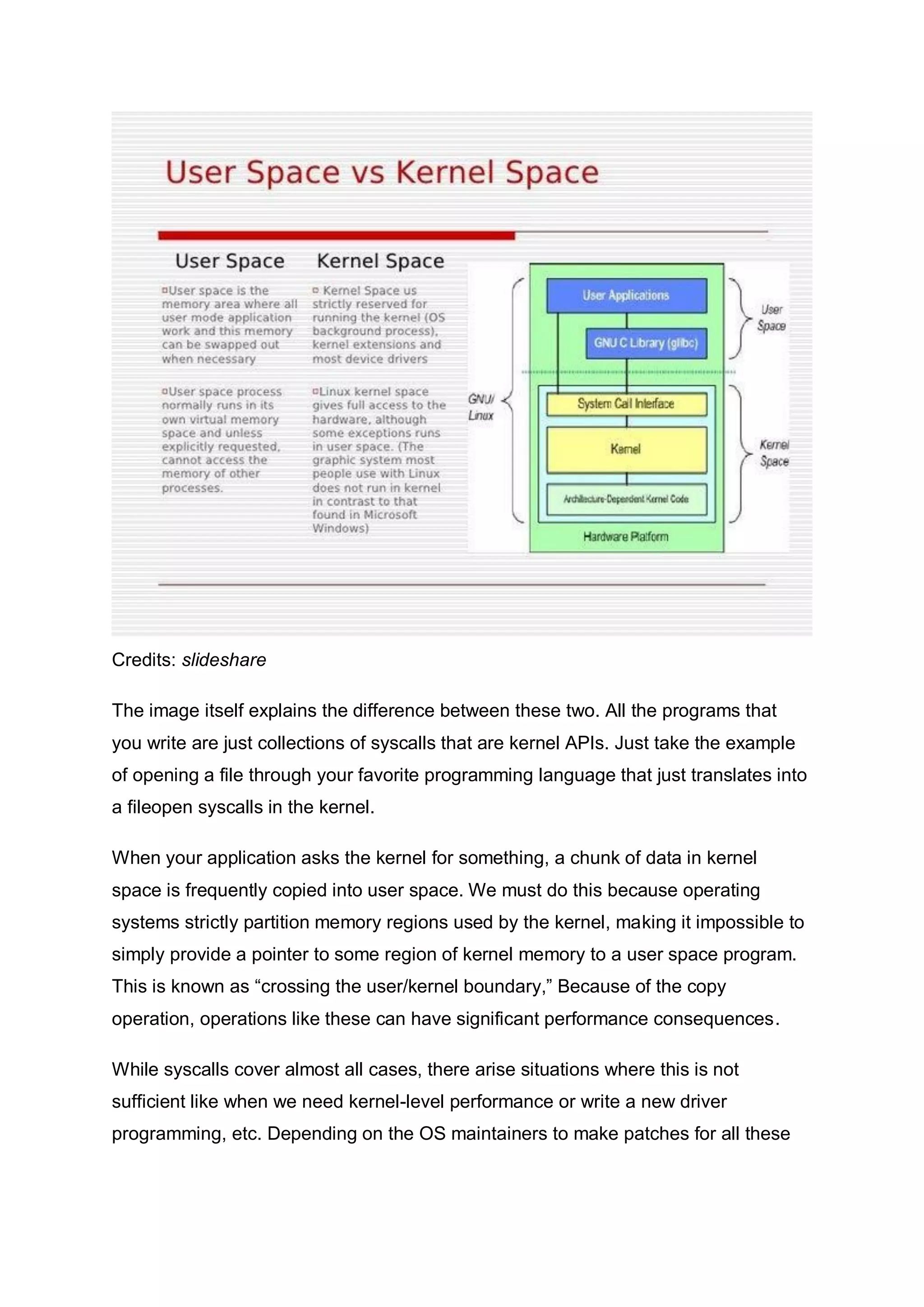
The document discusses eBPF (extended Berkeley Packet Filter), highlighting its importance for performance, network, and security engineers due to its ability to run custom code directly in the Linux kernel without needing patches. Introduced in 2014, eBPF has become essential for large tech companies and various applications such as observability, debugging, and load balancing. While it presents powerful capabilities, it also comes with risks like privilege escalation, necessitating careful use.