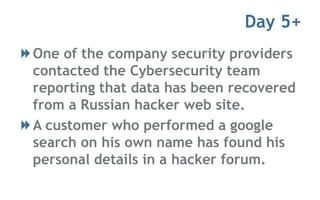
The MassTLC Security Conference featured a simulated data breach of WindResources, a wind turbine manufacturer. The breach began when a sales director's computer was infected with malware from a phishing email. An investigation found other infected computers and logs showing customer credentials being accessed from Russia. The breach escalated as stolen data was found online and a customer discovered their personal details exposed. The simulation panel discussed lessons around having an incident response plan, engaging legal and law enforcement, communicating about the breach, and practicing incident response.