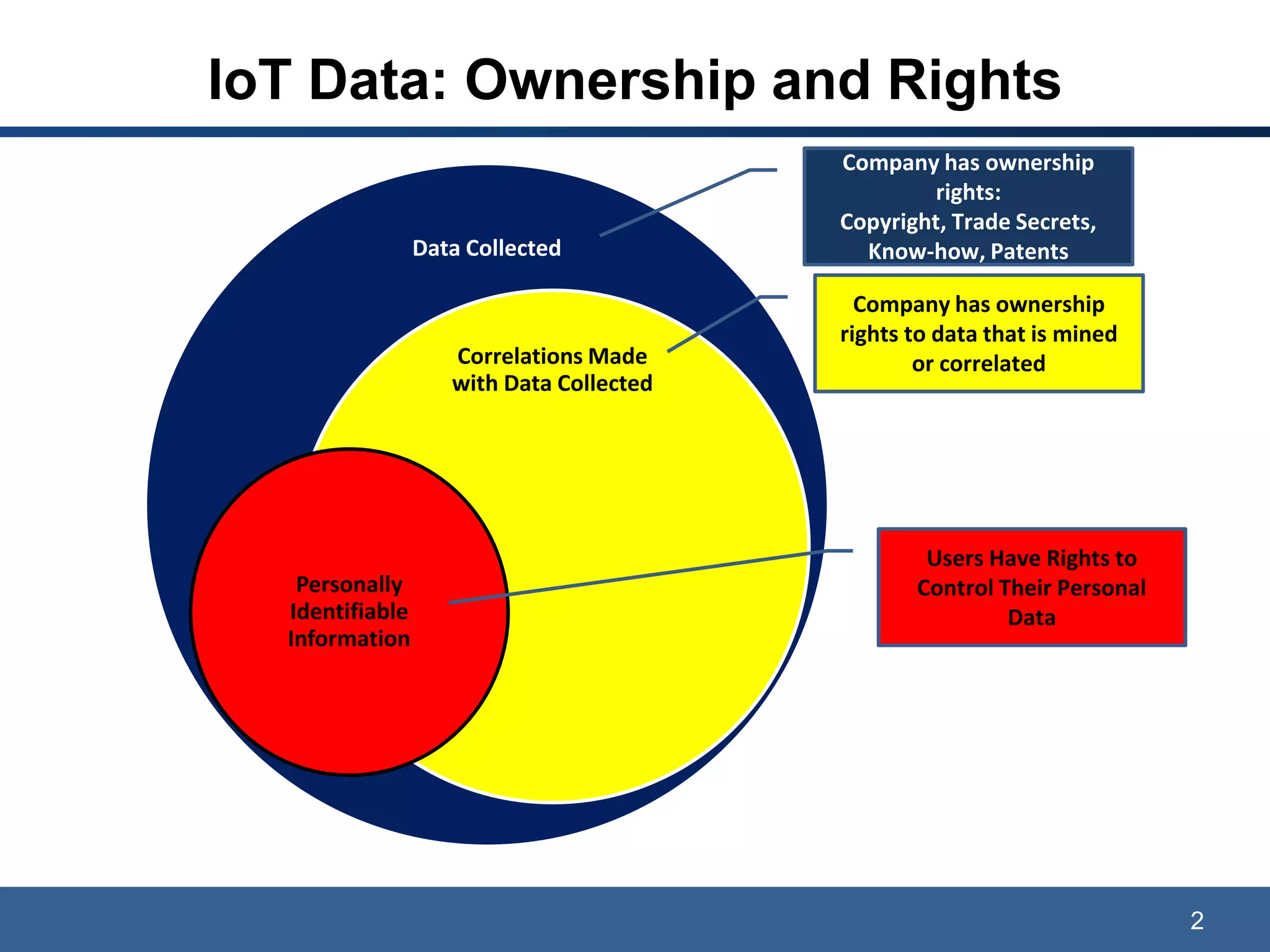
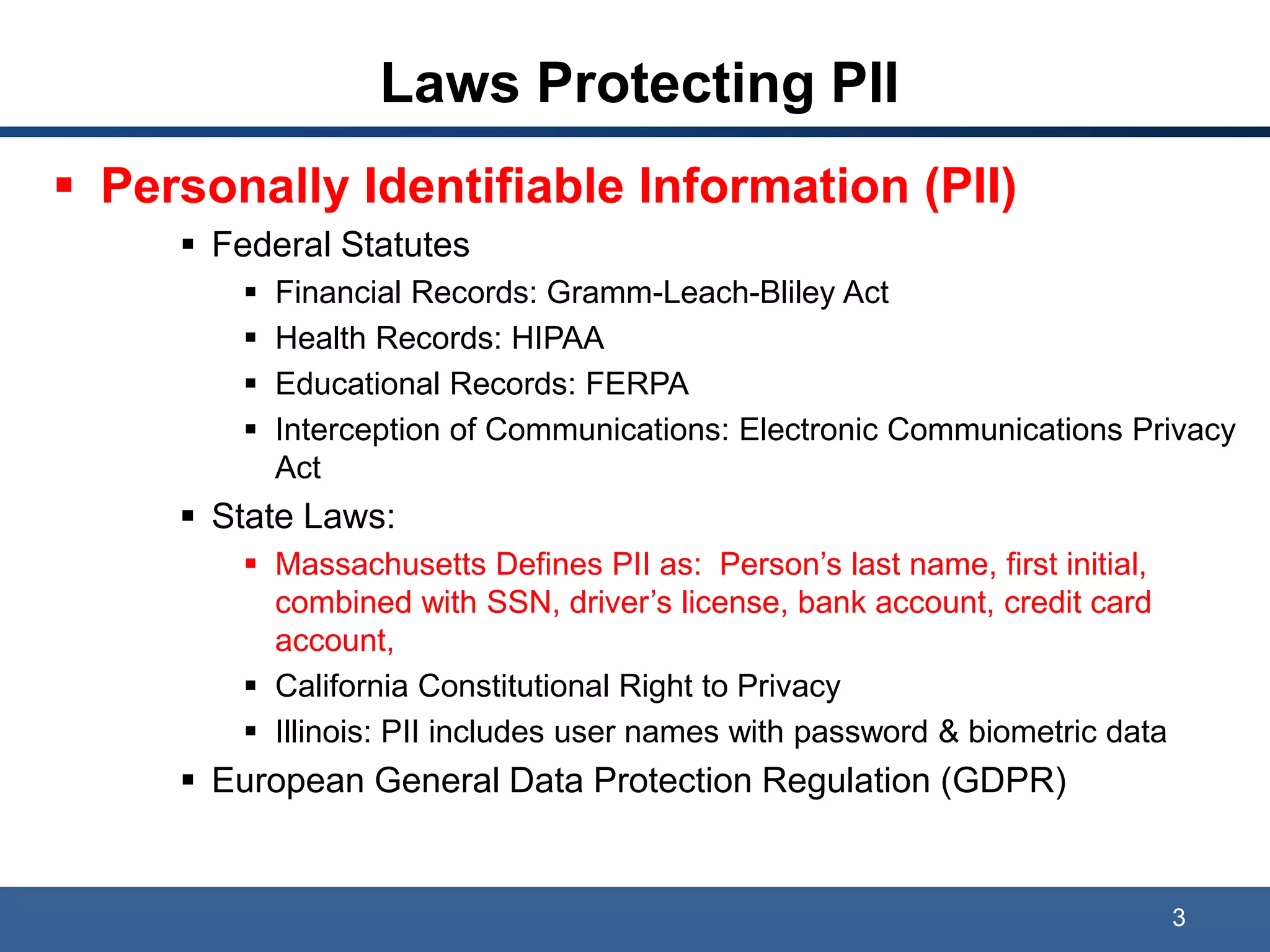
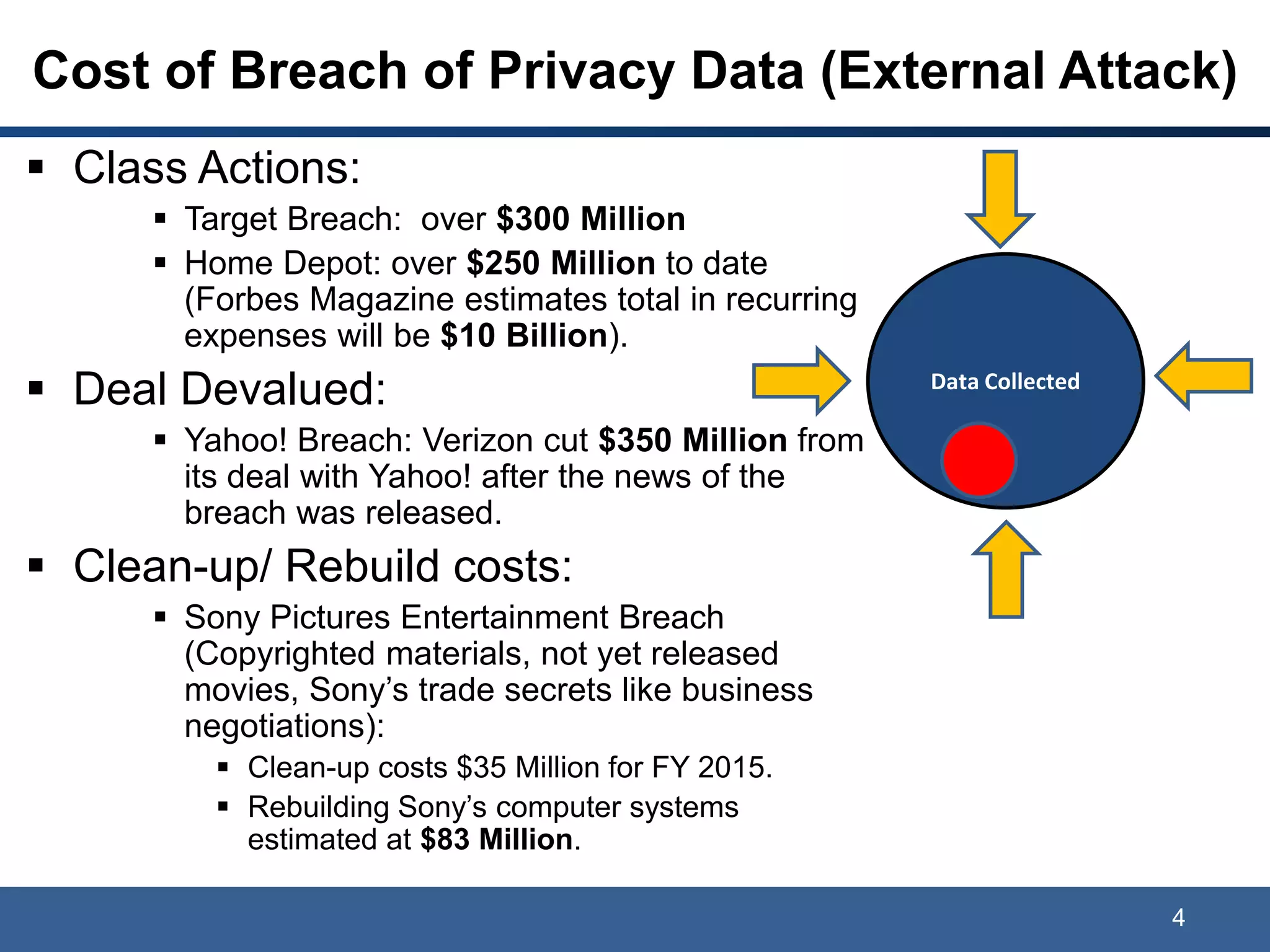
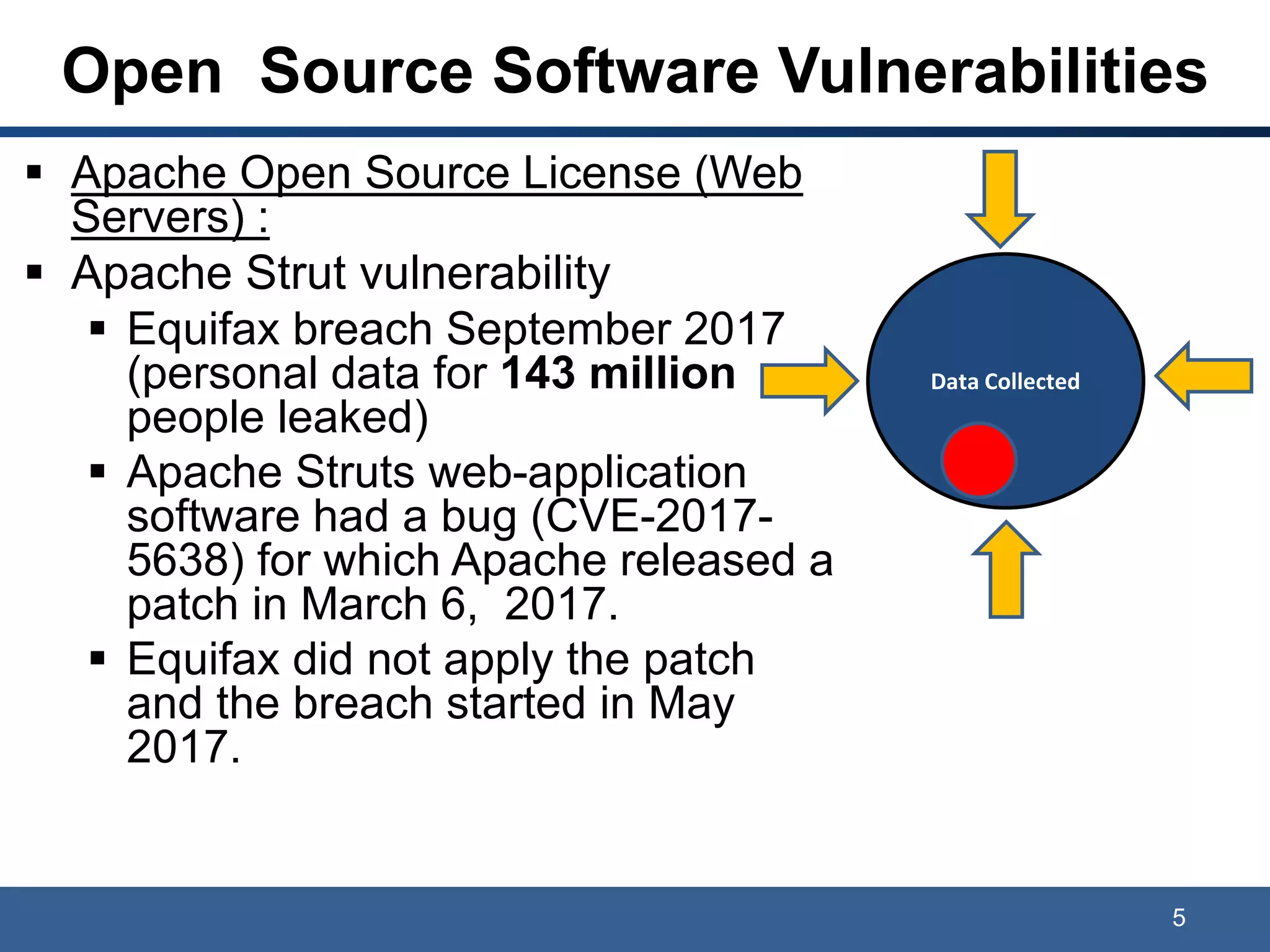
The document discusses data privacy, ownership, and the Internet of Things (IoT). It notes that while companies own data collected and correlations made, users have rights to control their personal data. Laws like GDPR protect personally identifiable information (PII), and breaches can result in costly class actions, clean-up costs, and fines if PII is collected without consent. The document recommends mitigating risks by following privacy- and security-by-design practices and obtaining user consent in privacy policies.