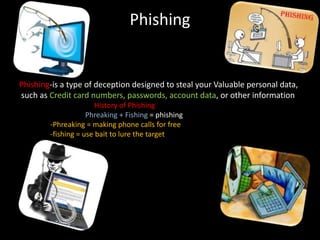
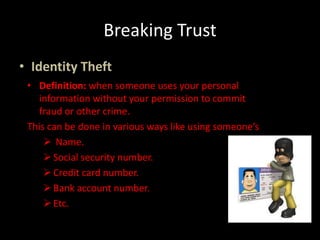
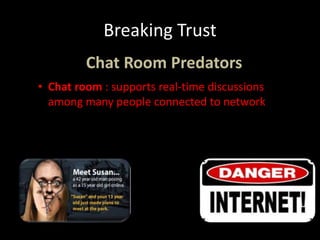
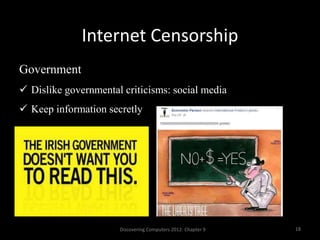
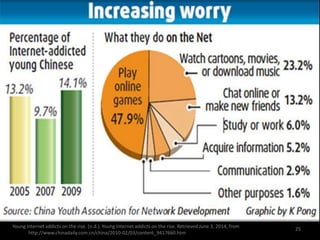
This document is an interactive guide to the digital world from a course on computer applications at Zaman University. It discusses topics like communications and networks, email and issues like spam and phishing, net neutrality, breaking trust online through identity theft and cyberbullying, internet censorship by governments, freedom of expression, inappropriate content for children, and internet addiction. The guide provides definitions and explanations of these topics with examples and advice on how to deal with certain issues. It also includes references used to compile the information in the guide.