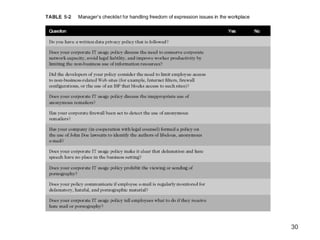
The chapter discusses key issues relating to freedom of expression and the use of information technology. It covers what speech the First Amendment protects, such as freedom of religion and expression, and what it does not protect, like obscene speech and defamation. Some key issues examined are controlling access to internet information, especially for children; anonymous communication; the spread of defamation and hate speech; access to pornography; and CAN-SPAM Act limitations on email messages.