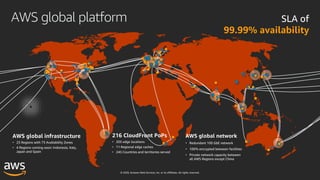
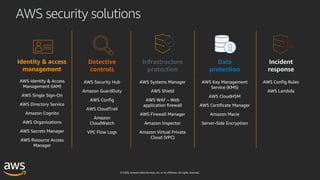
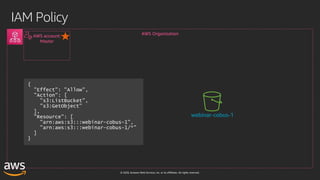
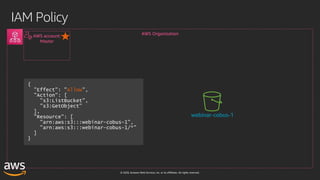
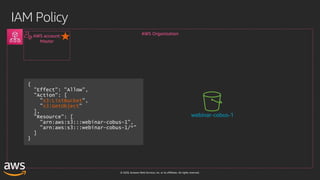
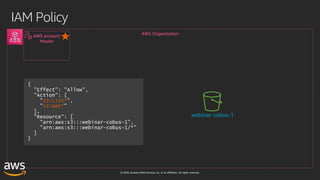
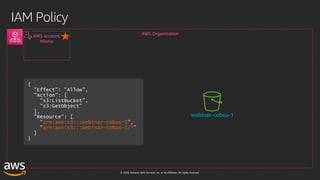
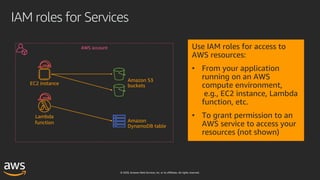
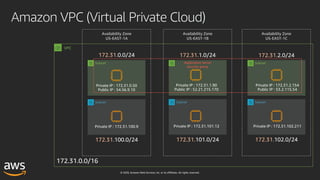
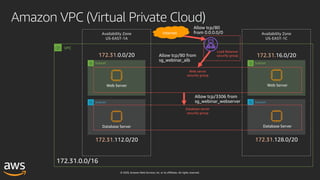
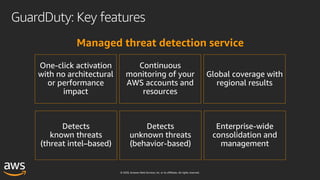
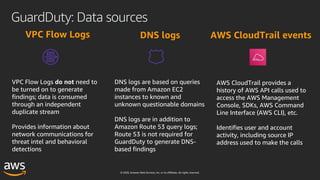
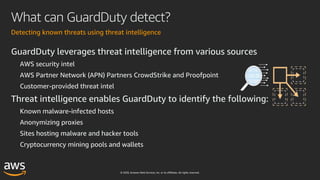
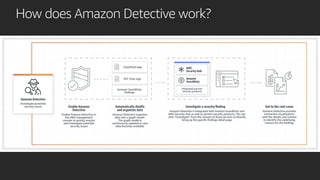
This document outlines key aspects of AWS security as presented in a webinar by Cobus Bernard, covering topics such as securing root accounts, identity management, and AWS global infrastructure. It highlights AWS's security solutions, including IAM policies, AWS Security Hub, Amazon GuardDuty, and web application firewalls (WAF). Emphasis is placed on best practices for compliance and threat detection across AWS services.