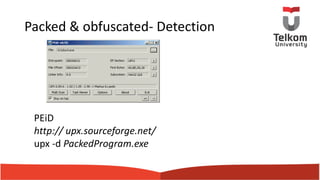
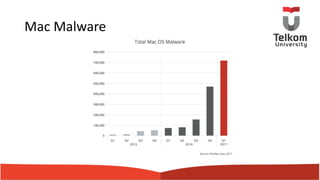
This document summarizes a presentation on malware analysis techniques. It discusses how malware spreads, common types of malware like ransomware and cryptomining malware, and approaches to analyzing malware both statically and dynamically. Static analysis techniques examined include scanning files, searching for strings, and analyzing file headers and dynamic linking. Dynamic analysis involves running malware in a controlled environment to observe its behaviors and network activity. Cryptomining malware is described as using victims' computers to mine cryptocurrency without permission.
































































![Terima Kasih
jul [at] tass.telkomuniversity.ac.id
jul_ismail
Blog: julismail.staff.telkomuniversity.ac.id
www.cert.or.id/](https://image.slidesharecdn.com/malwarecryptomining-uploadv3-180608080256/85/Malware-cryptomining-uploadv3-83-320.jpg)