Embed presentation




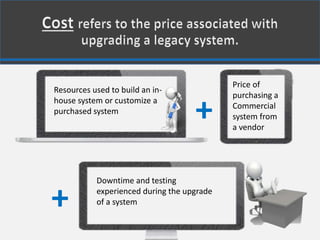

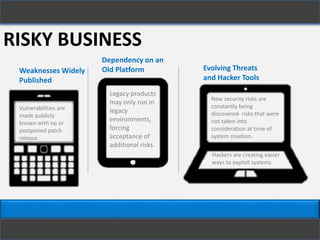
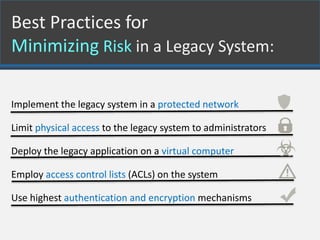


Legacy systems are outdated technologies still in use for critical business functions, often due to cost considerations. They pose various security risks, particularly as vendors may no longer support them, leading to vulnerabilities and potential exploitation by hackers. Best practices for mitigating these risks include implementing protective measures, limiting access, and utilizing strong authentication and encryption.








