This document outlines the syllabus for a CS 332 algorithms course. It discusses the following key points:
- The course will introduce rigorous design and analysis of algorithms through lectures, homework, exams, and a textbook.
- Grading will be based on homework, exams, final exam, and participation. The instructor is David Luebke and TA is Pavel Sorokin.
- Core topics will include proof by induction, asymptotic notation, and analyzing algorithms' time and space complexity as input size increases. Analysis will focus on worst-case performance.








![David Luebke 9 8/29/2022
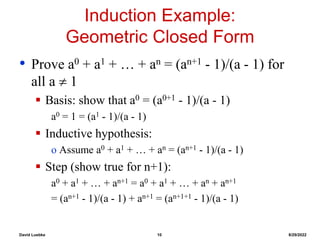
Induction Example:
Gaussian Closed Form
• Prove 1 + 2 + 3 + … + n = n(n+1) / 2
Basis:
o If n = 0, then 0 = 0(0+1) / 2
Inductive hypothesis:
o Assume 1 + 2 + 3 + … + n = n(n+1) / 2
Step (show true for n+1):
1 + 2 + … + n + n+1 = (1 + 2 + …+ n) + (n+1)
= n(n+1)/2 + n+1 = [n(n+1) + 2(n+1)]/2
= (n+1)(n+2)/2 = (n+1)(n+1 + 1) / 2](https://image.slidesharecdn.com/lecture1-220829050824-d6edadb8/85/lecture1-ppt-9-320.jpg)