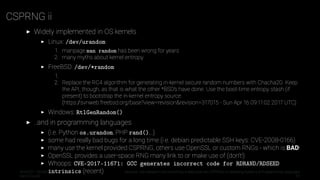
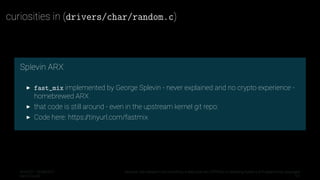
This document explores the importance and implementation of cryptographically secure pseudo-random number generators (CSPRNGs) in operating systems and programming languages, emphasizing the limitations of simply using '/dev/urandom'. It discusses historical context, common misconceptions, and various implementations across different platforms, highlighting vulnerabilities and improvements in random number generation practices. The author, Aaron Zauner, emphasizes the need for secure methods and critiques existing practices in various programming languages.